

Orange lock icon within a circuit grid.
Discover the top IDPS solutions for 2023 to protect your network with advanced defense mechanisms and real-time monitoring. Safeguard your data today!


An intrusion detection and prevention system (IDPS) is a key security strategy in the enterprise environment. An IDPS can protect organizations from cyberattacks and provide an audit log for administrators to do post-security operation analysis.
A decade ago, intrusion detection and prevention technology was regarded as a luxury for enterprises with larger budgets. Today, protection against internal and external threats is an absolute necessity.
After all, organizations can’t survive if they lose their data to malicious attacks or leak proprietary information to competitors. And yet even in today’s cybersecurity-conscious world, many businesses either don’t have proper security systems in place or are unaware of which ones are best suited to their needs.
According to Cybersecurity Ventures, global cyber crime costs are expected to grow by 15% per year over the next five years, reaching $10.5 trillion annually by 2025, up from $3 trillion in 2015. To avoid devastating data breaches, enterprises should deploy high-quality IDPS solutions early.
Here are our picks for the top intrusion detection and prevention systems:
| Best for | 24/7 network monitoring | Reporting capability | User interface | Pricing | |
|---|---|---|---|---|---|
| Cisco Secure Next-Generation IPS | Deep visibility into network traffic | Yes | Yes | Yes | High-end |
| Palo Alto Networks Threat Prevention | Large enterprises | Yes | Yes | Yes | High-end |
| Check Point IPS | Visibility and reporting | Yes | Yes | Yes | High-end |
| OSSEC HIDS | Performing rootkit detection and monitoring file integrity | Yes | Yes | No | Low-end (Starts at $55 per endpoint per year) |
| Snort | Budget-conscious businesses | Yes | Yes | Yes | Low-end (Starts at $29.99 per sensor per year) |
| Trellix Intrusion Prevention System | Hybrid cloud | Yes | Yes | Yes | Moderately priced |
| Alert Logic Managed Detection and Response | Real time threat analysis and behavioral analysis | Yes | Yes | Yes | High-end |
| CrowdSec | Real-time threat intelligence | Yes | Yes | Yes | High-end |
| SolarWinds Security Event Manager | Large organizations with complex security needs | Yes | Yes | Yes | High-end (Starts at $2,877) |
| Security Onion | Performing network security monitoring and incident response | Yes | Yes | Yes | Free |
Jump to:

Best for deep visibility into network traffic
By leveraging big data analytics and machine learning (ML) techniques, Cisco Secure NGIPS can detect advanced attacks and offer granular protection. The platform leverages threat intelligence, in-depth visibility into traffic flows, real-time analysis of global threat information, and a deep understanding of attack patterns to provide high-fidelity detection for known and unknown threats.
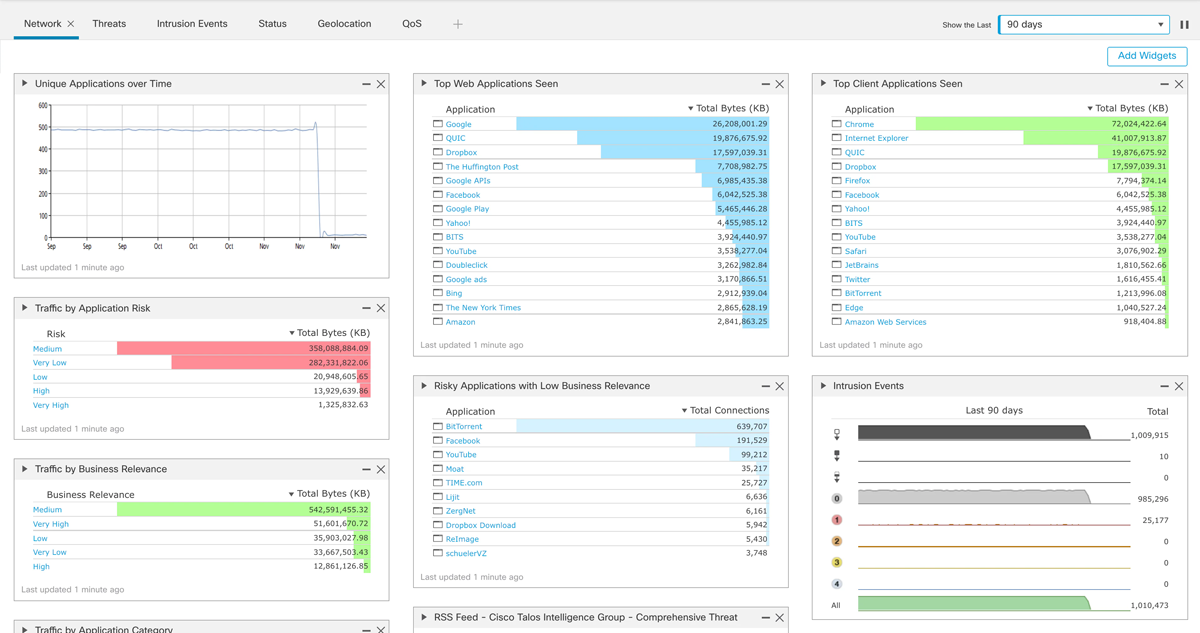
It also offers granular policy controls that allow security teams to determine which applications are permitted to access specific network resources at any given time. And it enables security analysts to quickly identify and block even highly complex DDoS attacks with integrated technology from Arbor Networks.
Pricing information is not provided on the Cisco website. You can contact the Cisco sales team or a verified partner for quotes. Publicly available data shows that the solution price ranges from a few thousand dollars to hundreds of thousands, depending on your needs.

Best for large enterprises
Palo Alto Networks Threat Prevention safeguards your network against traditional attacks and targeted, advanced threats perpetrated by organized cyberattacks. It offers extensive exploit, malware, and command-and-control (C2) security.
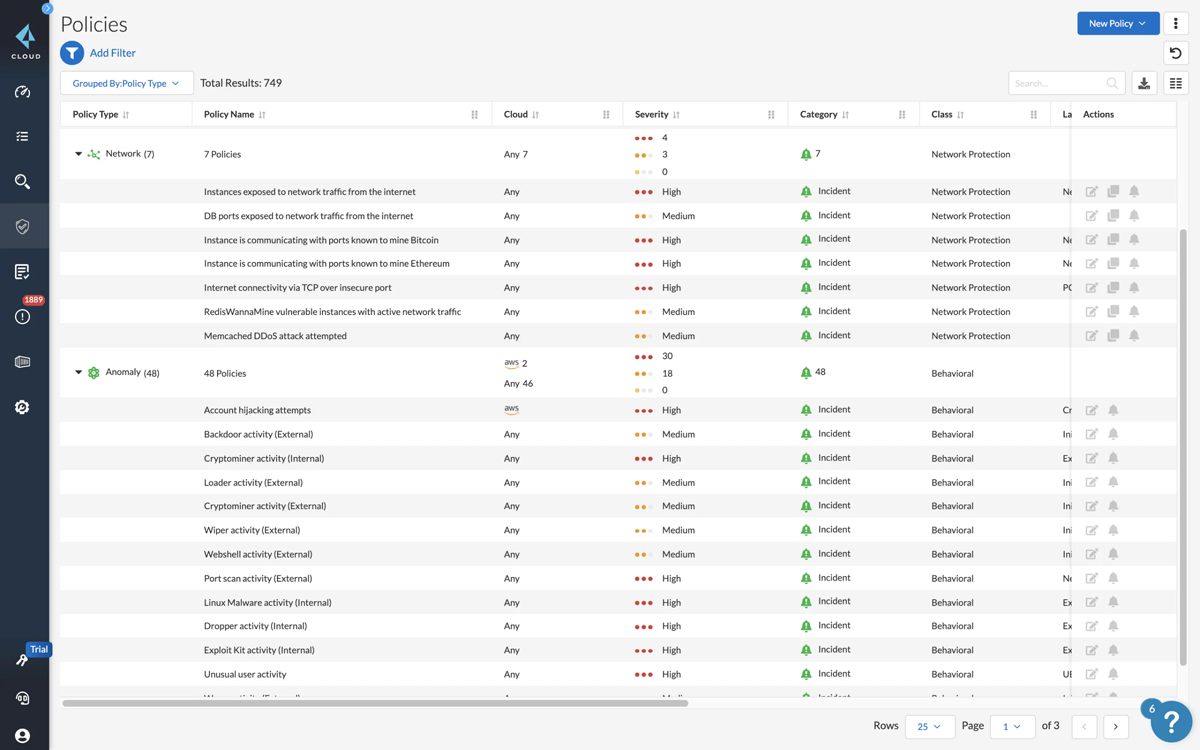
Palo Alto Networks Threat Prevention also provides log management, comprehensive exploit, malware, and C2 protection to protect the enterprise from cyberthreats.
Pricing information is not provided on the Palo Alto website. You can book a demo to get a personalized product recommendation for your enterprise. Some users reported that the solution license cost is expensive, although it can vary greatly.

Best for visibility and reporting
Check Point IPS provides a comprehensive NGFW, with integrated IDS/IPS functionality that combines real-time attack detection and blocking with network security policy enforcement. It can be deployed as a physical or virtual appliance.
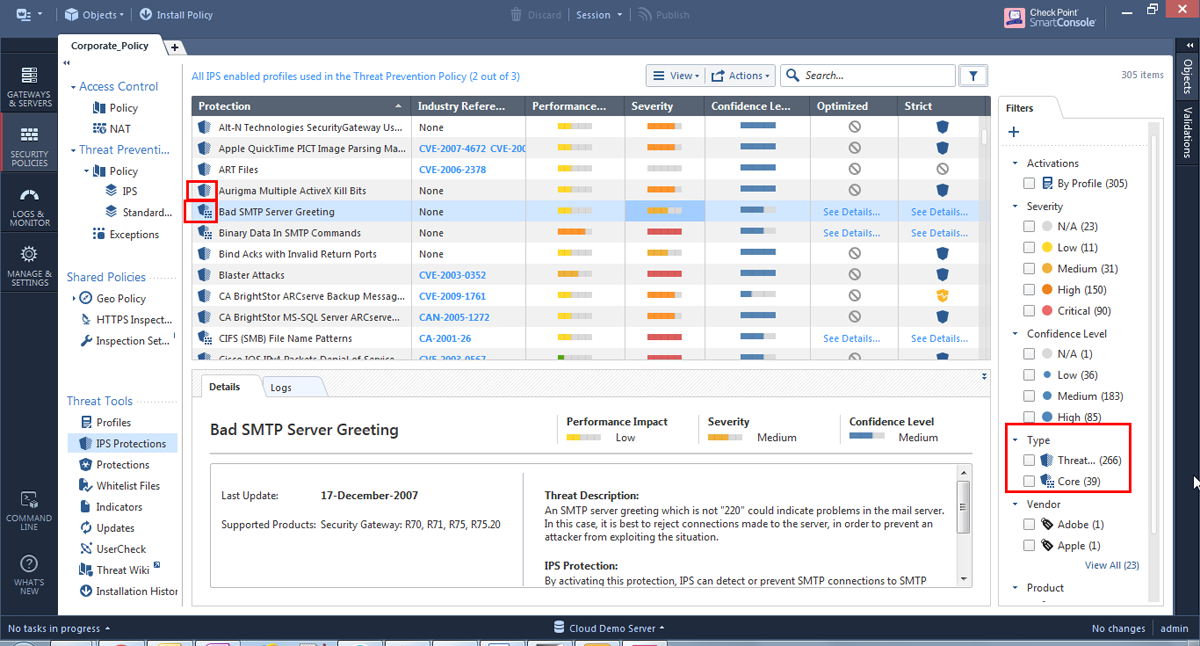
With its ability to stop attacks before impacting your organization, Check Point protects enterprises against cyberthreats, including malware and targeted attacks. It uses a combination of signatures, protocol validation, anomaly detection, and behavioral analysis to detect intrusions in real time. You can also use it to enforce security policies across multiple devices on your network from one centralized location.
Pricing information is not provided on the Check Point website. However, you can book a demo with the Check Point team or find an authorized Check Point partner.

Best IDS for performing rootkit detection and monitoring file integrity
OSSEC is an open-source, host-based intrusion detection system that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting, and active response. It runs on most operating systems (OSs), including Linux, OpenBSD, and Mac OS X.
Daniel Cid originally developed the software and it has been under constant development since 2004. OSSEC can be deployed either stand-alone or as a client/server architecture.
OSSEC is a free and open source tool. It is available in three versions: OSSEC, which is the regular version, OSSEC+, which includes additional capabilities and Atomic OSSEC, which is an enterprise version.
The enterprise plan features clustering, agent management, reporting, security, vulnerability management, and third-party systems integration. Pricing starts at $55 per endpoint per year, or less than $5 per month.

Best for budget-conscious businesses
Snort is an open-source network IDPS developed in 1998 by Martin Roesch, founder and former CTO of Sourcefire. It performs real-time traffic analysis and packet logging on IP networks. It can also detect malicious traffic in your networks, such as DDoS attacks, worms, or viruses.
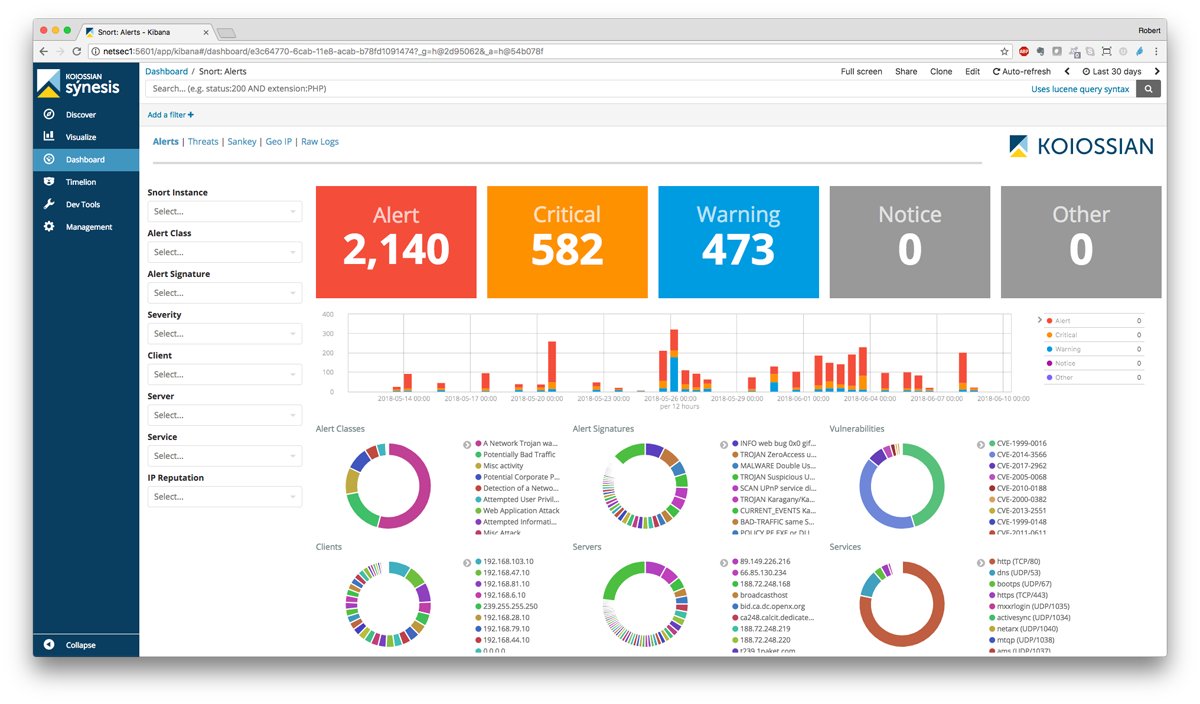
Snort uses a flexible rule-based language to describe traffic it should collect or pass as well as a detection engine that uses pattern matching rules to identify suspected malicious traffic.
The software can be run in both in-line blocking and passive monitoring modes. In-line blocking mode inspects packets passing through a router or switch, while passive monitoring mode listens to network traffic but does not block any packets.
While Snort is a free, open-source tool, it also offers three subscription-based product rule sets. Snort’s personal rule set subscription costs $29.99 each for a one-year subscription, and Snort’s business rule set subscription costs $399 per sensor for a one-year subscription. For the Snort integrator, prospective buyers can contact the Snort team for details.

Best for hybrid cloud
Trellix Intrusion Prevention System, formerly McAfee Network Security Platform, has advanced threat protection and malware detection. It uses a combination of deep packet inspection (DPI) and threat intelligence to detect unknown attacks, classify threats, and stop attackers in their tracks.
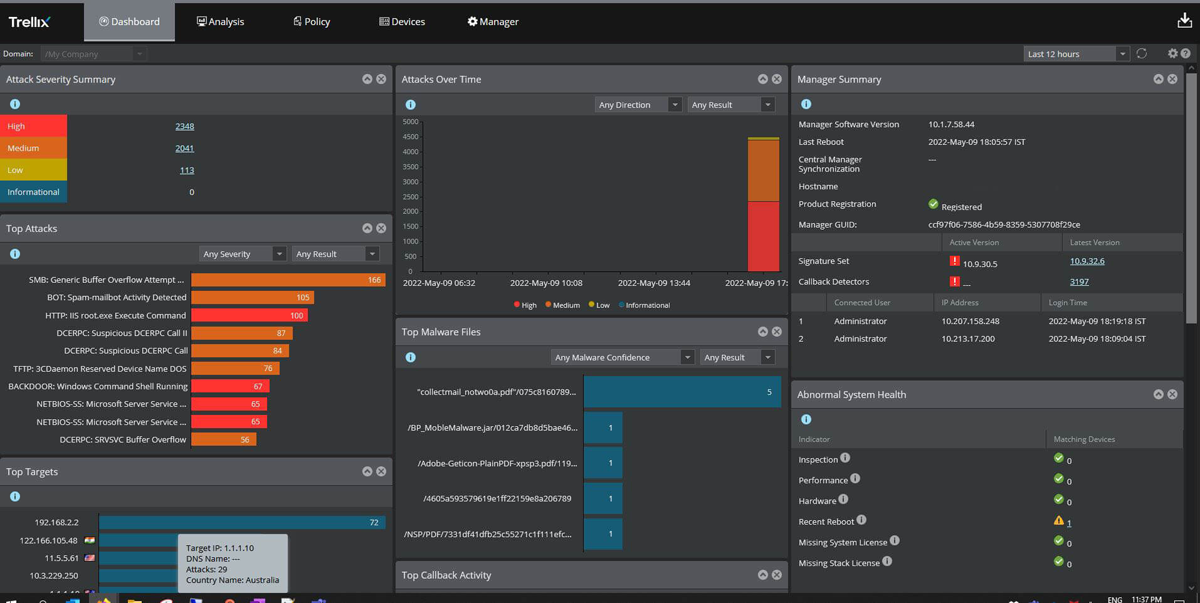
Trellix provides visibility into data packets for more granular control over network traffic, which enables you to block malicious content before it reaches end users. The platform also provides security analytics that help you identify vulnerabilities across your network infrastructure, so you can quickly patch them before hackers exploit them.
Trellix doesn’t advertise its product pricing on its website. The company encourages buyers to discuss their needs with an in-house expert before sending out personalized quotes based on your needs.

Best for real time threat analysis and behavioral analysis
Alert Logic is part of Fortra’s comprehensive cybersecurity portfolio. Alert Logic provides comprehensive IDS coverage for public cloud, SaaS, on-premises, and hybrid environments. It provides protection against both known and zero-day threats and continuous network monitoring.
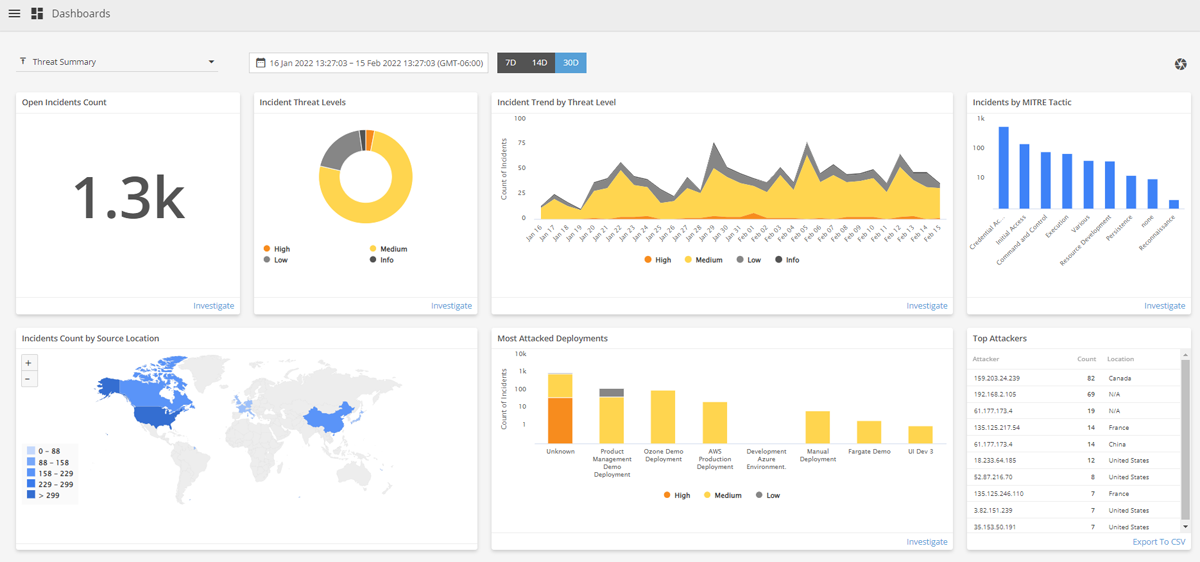
Alert Logic MDR has an always-on threat monitoring capability, allowing it to detect network intruders more quickly and faster, leading to shorter attacker dwell time and less environmental damage. The managed security solution is designed to help organizations detect and respond to intrusions in real-time by continuously monitoring all devices on a company’s network for suspicious activity.
Alert logic offers a pay-as-you-grow model, and pricing starts at 25 nodes. Although exact pricing information is not available on the vendor’s website, they offer three pricing plans: Alert Logic MDR essentials, Alert Logic MDR professional, and Alert Logic MDR enterprise. For more information on pricing, prospective buyers can request a quote or book a demo.

Best for real-time threat intelligence
CrowdSec is an open-source collaborative IPS platform that leverages the community to detect and prevent security threats. Using a combination of ML, predictive analytics, and user-generated data, CrowdSec can detect and block both known and unknown cyberattacks. This approach allows it to provide real-time threat intelligence while protecting its users from false positives.
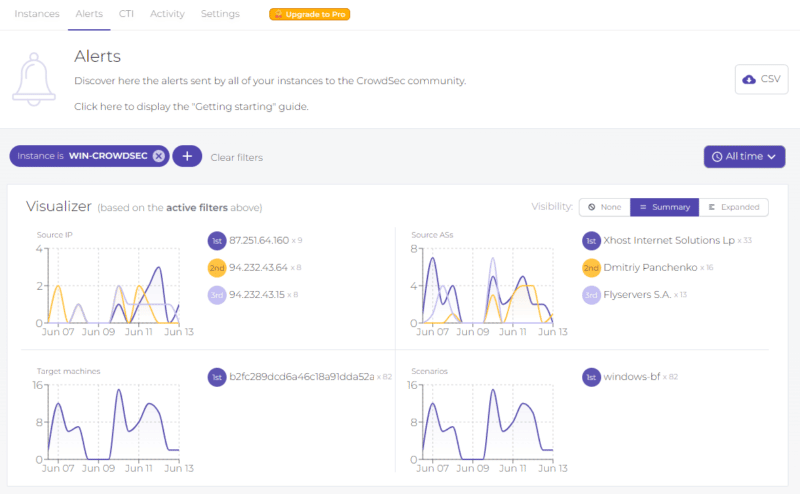
CrowdSec is designed to run on virtual machines (VMs), bare-metal servers, containers, or called directly via API.
CrowdSec offers two plans: A community plan, which is free and is designed for individual users, hobbyists, and open source software enthusiasts, and an Enterprise plan designed for large organizations and advanced security teams. To get pricing for the enterprise plan, buyers must contact the CrowdSec team.

Best for large organizations with complex security needs
SolarWinds Security Event Manager ensures transparency in showing compliance with features intended to let users conveniently monitor and manage any security event throughout their network infrastructure, including the ability to produce thorough and easy-to-customize reports.
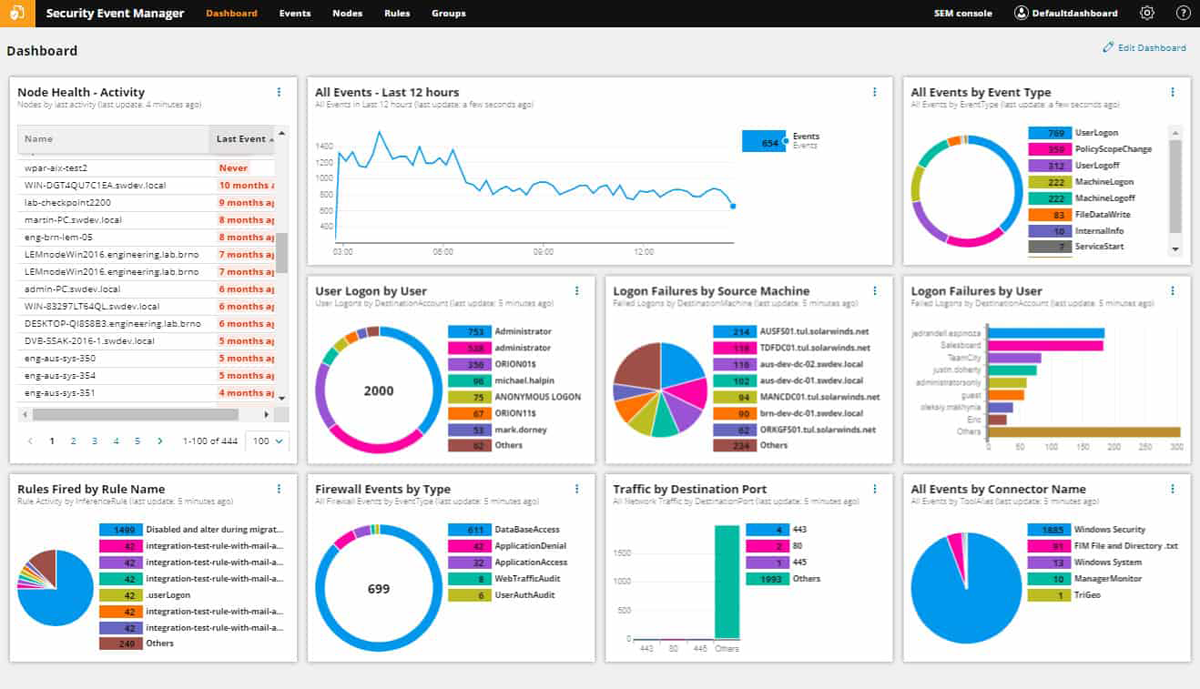
SolarWinds offers a 30-day free trial. The vendor subscription starts at $2,877, and the perpetual licensing starts at $5,607. In addition, prospective buyers can request personalized quotes tailored to their enterprise.

Best for performing network security monitoring and incident response
Security Onion is a free and open source Ubuntu-based Linux distribution for threat detection, IDPS testing, and security monitoring. Security Onion includes several tools for sniffing packets, logging activity, running vulnerability scans, generating reports, etc. It also contains Snort, Suricata, Bro, OSSEC HIDS, Sguil clients, and more.
Security Onion aims to provide an all-in-one platform for performing network security monitoring and incident response.
The tool is free to use and open source.
Although their full packages can vary widely, all IDPS tools should include the basics: constant monitoring, signature-based detection, logging and reporting, traffic analysis, and alerts.
By monitoring your network infrastructure 24/7, IDPS can identify unauthorized access attempts, unusual patterns of behavior, or known attack signatures. IDPS analyzes incoming and outgoing data packets, looking for signs of potential intrusion attempts, unauthorized access, or abnormal behavior.
Real-time monitoring enables rapid detection and response to security incidents as they happen, minimizing the potential impact of attacks.
IDPS should employ signature-based detection. This method involves comparing incoming data packets or system activity against a database of known patterns associated with specific threats or attacks. When a match is found, the IDPS triggers an alert or takes appropriate action to prevent the attack from succeeding.
Logging, reporting, and analysis capabilities are important functionalities of IDPS systems. Logs are valuable for forensic analysis, post-incident investigations, and compliance purposes.
IDPS also helps to generate reports on detected threats, analyze attack patterns, and identify potential vulnerabilities in the network or system. This information helps organizations improve their security posture and take necessary measures to prevent future intrusions.
IDPSs analyze network packets and traffic to identify any anomalies or suspicious behavior. This includes examining protocol anomalies, checking for unauthorized protocols, and identifying unusual traffic patterns.
Whenever an intrusion or suspicious activity is detected, these systems generate alerts and notifications to network administrators or security teams. This enables a timely response to mitigate the potential damage.
There are many benefits to intrusion detection and prevention systems. These range from data safety to financial savings and more. Here are six benefits of IDPS:
Many different types of attacks can make their way through an unsecured network, but fortunately, there are many ways to protect against them. For example, IDS and IPS systems may not be able to block every potential security threat, but they monitor activity in real time and detect an attack before any real damage is done.
The type and sophistication of a defense system depend on your company’s resources and goals; what matters most is that you take concrete steps toward protecting your sensitive data.
So when looking for an IDS or IPS system for your organization, you should focus first on how well it addresses specific vulnerabilities identified in research reports, and then, look at its ease of use, so you can set up and maintain a powerful system without sacrificing productivity. The best IDS/IPS system is the one that works best for you.
Yes — IDPSs are designed to detect and prevent unauthorized access, malicious activities, and potential security breaches to your network.
The intrusion detection component scans network traffic and system logs to identify potential threats, such as unusual patterns, known attack signatures, or anomalous behavior.
Once a potential intrusion is detected, the intrusion prevention component takes action to prevent the attack from compromising the network’s security. This can involve blocking malicious IP addresses, isolating affected systems, or even terminating malicious processes.
While IDPS is effective in detecting known attack patterns and signatures, it cannot be considered a complete defense. It may struggle with novel or sophisticated threats that do not match any existing signatures. IDPS should be complemented with other security layers, such as firewalls, antivirus software, behavioral analytics, endpoint protection, and regular security awareness training for employees.
Yes, IDPS is suitable and beneficial for small businesses. Although large enterprises typically have more extensive cybersecurity budgets and resources, small businesses are sadly not immune to cyberthreats. In fact, they can be more vulnerable due to limited IT staff and infrastructure.
IDPS solutions provide an essential layer of defense against various cyberattacks, such as malware, ransomware, and unauthorized access attempts.
We ranked the best IDPS tools based on several core functionalities of IDPS solutions, such as 24/7 network monitoring, alerts and notification, threat intelligence capability, log management, reporting and more.
We gathered primary data about each solution from the vendor’s website and we also analyzed user feedback on review websites to learn about current and past user experience to help us determine each tool’s usability capability.
We understand that our readers are from various industries and organization types and sizes, so our review covers tools that are suitable for small, medium and large enterprises.
The best IDPS tool for you depends on your business’s unique network security needs. Hence the need to select a tool based on its ease of implementation and use, its effectiveness in detecting and preventing attacks, its scalability to adapt to growing needs, and its compatibility with existing security infrastructure.
Our top picks stood out for their advanced threat detection capabilities, real-time monitoring, excellent network visibility and comprehensive reporting capabilities. They also offer a good balance of detection and prevention features, making each tool a reliable solution for organizations with both simple and complex IT landscapes.
For deeper and more granular network visibility, you may want to implement one of the best network monitoring tools, which we have also reviewed.


Aminu Abdullahi is an experienced B2B technology and finance writer and award-winning public speaker. He is the co-author of the e-book, The Ultimate Creativity Playbook, and has written for various publications, including eWEEK, Enterprise Networking Planet, Tech Republic, eSecurity Planet, CIO Insight, Enterprise Storage Forum, IT Business Edge, Webopedia, Software Pundit, and Geekflare.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.