Insider threats and targeted attacks are on the rise and becoming harder and harder to detect, especially with enterprises that experience difficulties recruiting and retaining seasoned IT security staff. And if recent intrusions, attacks and data breaches at organizations as large as Target, Home Depot, and Sony have taught us anything, it is that both […]
Insider threats and targeted attacks are on the rise and becoming harder and harder to detect, especially with enterprises that experience difficulties recruiting and retaining seasoned IT security staff. And if recent intrusions, attacks and data breaches at organizations as large as Target, Home Depot, and Sony have taught us anything, it is that both security technology and personnel are coming up short in identifying and remediating threats.
Enter Vectra Networks, a San Jose, CA-based startup that came out of stealth mode earlier this year. Vectra’s X-Series security appliances combine advanced security analytics with machine learning to identify data security threats in real time.
To truly appreciate the technology that Vectra has developed, one has to first understand how attacks and intrusions happen on today’s networks. While it would take a thick tome to explain the attack process fully, the basics amount to a few critical steps. These are the most commonly used by hackers and data thieves today.
Obviously, much more activity and many additional subtasks can be incorporated into an intentional data breach, but the process almost always involves the basics of infiltrate, reconnoiter, identify, acquire and exflitrate.
While one may assume that it should be easy to uncover any of the abovementioned actions, the ease or difficulty of the task comes down to how those actions are hidden within the typical noise of network traffic and how each action is separated by time, method and activity. In practice, these variables often make it incredibly challenging to identify an attack in progress and proactively defend against it.
Here’s where Vectra Network’s automated threat detection comes onto the scene. It defends against hacks and prevents data breaches by intelligently correlating seemingly unrelated events into actionable notifications, helping security analysts battle insider and outsider threats, botnets and much more.
On page 2: How Vectra’s X-Series security appliances can prevent data breaches
Header photo courtesy of Shutterstock. All other images provided by the author.
The Vectra X-Series security appliances monitor all internal network traffic by connecting to a span port on the core switch. Multiple connections to multiple span ports on different switches allow the appliances to analyze all possible network data, east-west and north-south traffic, even if that data is travelling across physically isolated subnets.
Initial setup of an X-Series appliance requires little more than using a console connection to set the initial IP address for management. After a known IP address is assigned to the unit, further management takes place using an AJAX-based web/browser management console. The management console allows administrators to further configure the unit with additional settings, such as DNS server IP address, syslog server IP address, email alerts settings, and any public IP subnets (on the internal network) for inclusion in traffic analysis.
For the majority of adopters, the default settings will prove adequate for detection and reporting purposes. Fine-tuning, such as ignoring specific detections, can be done at a later date if needed.

Vectra takes a somewhat unusual approach to identifying assets on the network. The company nomenclature refers to assets as hosts. A host is nothing more than any device assigned an IP address at a given point in time. Vectra also “fingerprints” each host using a variety of artifacts, ranging from MAC addresses to DNS host names. The idea here is that every network-attached element on the network can be identified, classified and associated with its traffic.
Fingerprinting hosts further enables Vectra’s machine learning and automated heuristics to identify the relationships between network traffic, normal usage and the device in question. Ultimately, Vectra is able to create a relationship equation that defines normalized behavior and differentiates it from minor and significant anomalies. This then provides the appliance with the information to score the relevance of possible intrusions, attacks and data theft in real time.
Of course, identifying and rating anomalies provides little value if that information cannot be conceptualized, contextualized, and delivered in an easy-to-understand fashion. This is an area in which Vectra’s X-series security appliances excel. The underlying security event analytics are presented using visual representations that might be the high-water mark for security event data visualization achievements.
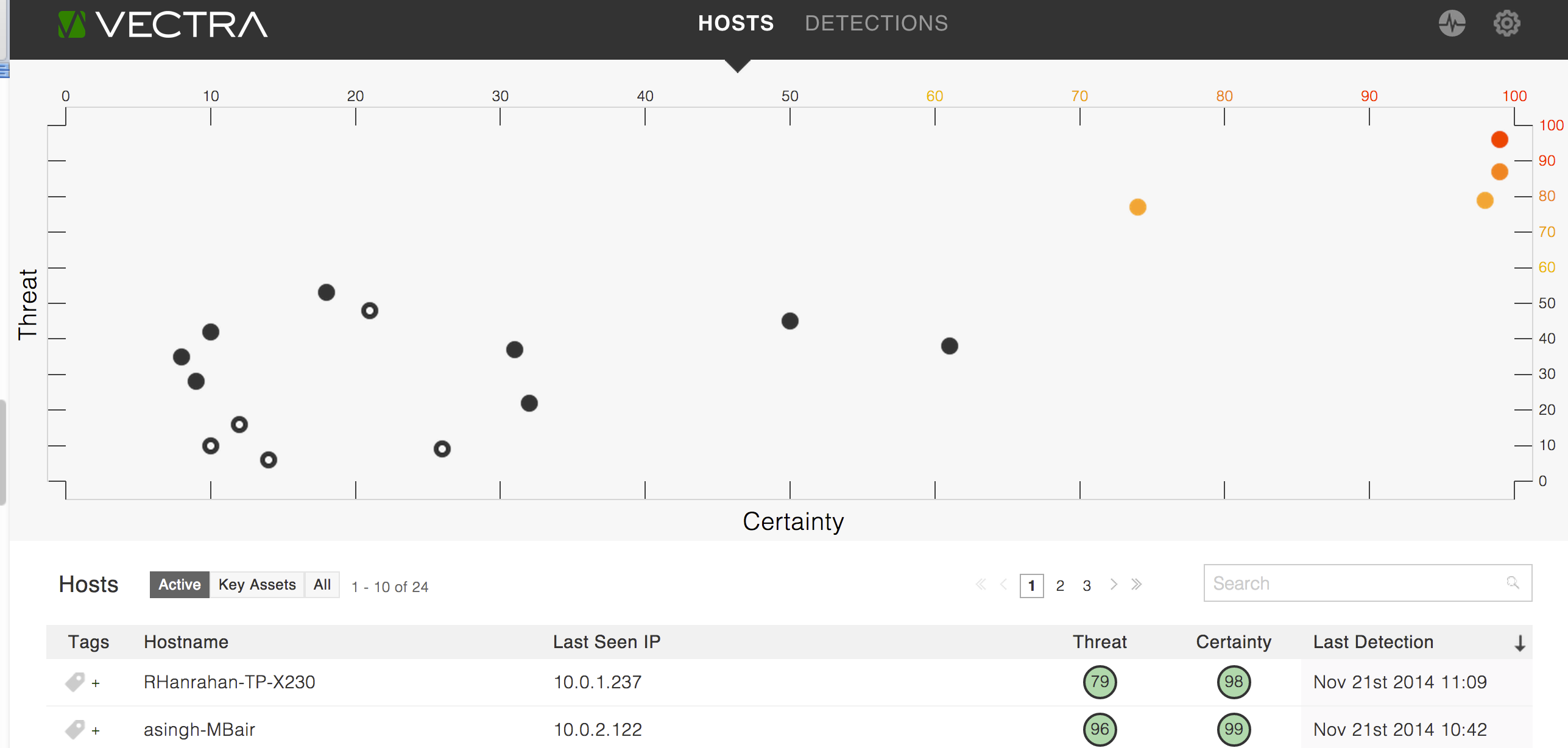
Instead of presenting administrators with static lists of alerts and associated grades, Vectra creates real-time, intuitive reporting that emphasizes activities that must be attended to immediately. Reports and visualizations clearly indicate what hosts are outliers of the normal range of expected activities, determined by a pair of host scores referred as Vectra’s Threat Certainty Index.
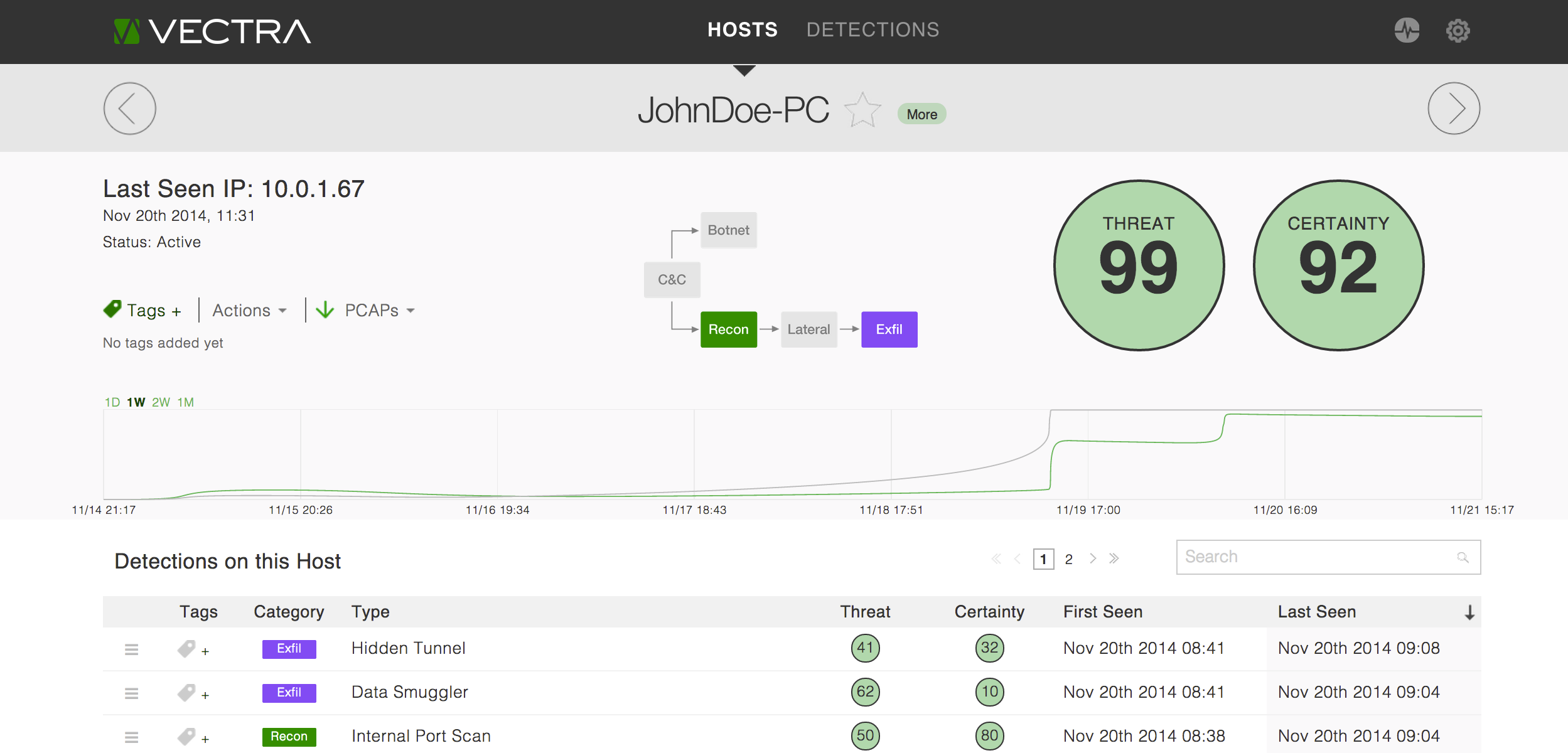
Administrators can readily drill down into the details of any given host and further investigate why that host has been identified as an outlier. The impressive drill-down capability gives administrators a visual representation of the host’s activity and how that activity may fit into an attack’s progression. For example, the console provides a graphical element to illustrate an attack in progress. Administrators can quickly judge the severity and the level of success by just glancing at the graphical progression of the attack and make a decision on the spot as to what action should be taken.
The details screen for the selected host also provides other critical elements, such as scores for threat level and certainty of the detected behaviors according to the Threat Certainty Index. Both of those scores are calculated using a rollup of detections, each of which is scored individually, to give a clear assessment of attack severity while allowing an administrator to delve further into each individual detection.
Another impressive feature is the ability to relate “context” to activity. Here, administrators can evaluate the context of a suspected attack and use that information to detect whether there was indeed a compromise or if the detection of a possible attack was related to a non-malicious cause, such as a change in operational procedures or due to a misconfigured device.
For example, if a host device is assigned a new chore, such as performing extensive backups of network resources, administrators can ascertain that that anomalous activity is a non-threating event without having to first spend hours determining context and the likelihood that data theft is involved.
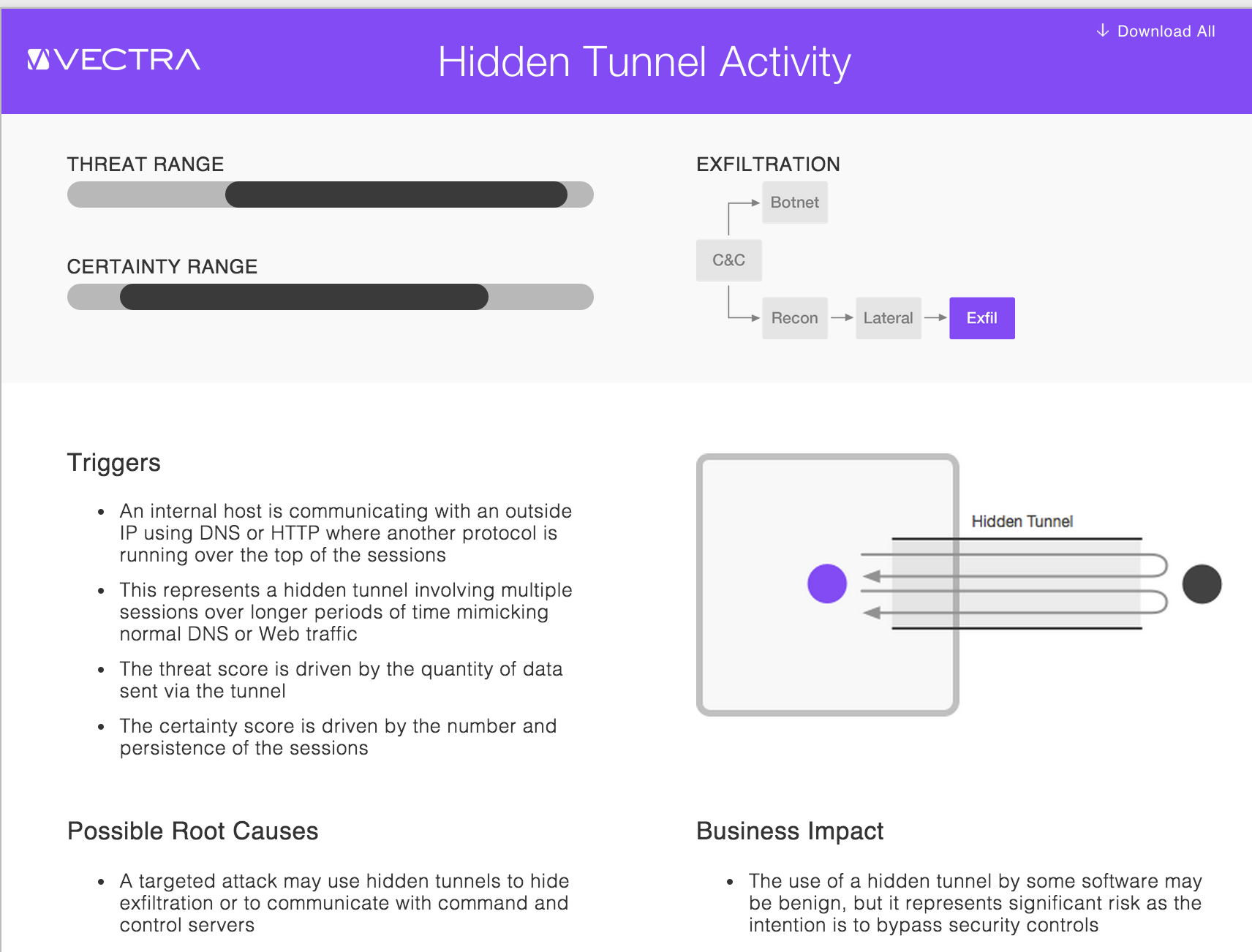
When additional information is needed to clarify concepts for administrators, the system offers a knowledge base of attack definitions. These define the level of the threat, provide the likelihood of the attack, and detail the root causes behind the identified event. An interesting feature of the system is the ability to print out all of the attack definitions into a single document, which makes it a valuable training tool.
Administrators can further fine-tune the Vectra X-Series attack detection system by identifying “key assets.” Making a host a key asset raises its importance in the activity visualization process. By classifying assets, administrators can adopt a triage approach to dealing with threats, quickly determining what needs to be done immediately to protect a key asset. Tasks associated with lower-priority hosts can be put off until the opportunity presents itself.
What’s more, the visual representations of potential problems allow even neophyte network security managers to quickly interpret and respond to threats before serious problems arise. This in turn helps IT managers meet the challenges associated with hiring seasoned security professionals.
That ease of comprehension doesn’t end at the management screens. Vectra’s X-series security appliances also offer reports that break down events into a “management view” that removes much of the technobabble and presents the information in a fashion that non-technologists can easily understand.
Vectra Networks’ X-Series security appliances prove that behavioral analytics can provide an excellent option in the ongoing fight against data theft and other intrusions. Events that other systems may ignore, such as multiple login attempts to an unusual resource, are detected and escalated to a notification level that prompts administrators to look further into the problem. What’s more, Vectra Networks clearly demonstrates the power behind data visualization, a power that has gone unnoticed in the world of IT security systems.
Header photo courtesy of Shutterstock. All other images provided by the author.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.