OpenVPN is famously difficult to get up and running, but the truth is that it needn’t be. In this second and concluding OpenVPN article I am going to go through what it takes to get an OpenVPN Ethernet tunnel set up between a laptop computer and an office or home machine acting as an OpenVPN […]


OpenVPN is famously difficult to get up and running, but the truth is that it needn’t be. In this second and concluding OpenVPN article I am going to go through what it takes to get an OpenVPN Ethernet tunnel set up between a laptop computer and an office or home machine acting as an OpenVPN server.
Before you can get OpenVPN running on any computer you need to download and install it:
Windows: Download the OpenVPN GUI installation package from http://openvpn.se/download.html
Red Hat, Fedora, CentOS: Download RPM packages from http://dag.wieers.com/rpm/packages/openvpn/
Ubuntu: Download and install OpenVPN using Synaptic Package Manager
Mac OS X: Download and install Tunnelblick OpenVPN GUI client installation package from http://code.google.com/p/tunnelblick/
Source code: Download source code from http://www.openvpn.net/index.php/downloads.html, compile and install it.
Once you’ve got OpenVPN successfully installed, it’s time to build the public key infrastructure needed for certificate-based authentication. If you don’t know what this means, don’t worry: just follow the instructions. A fuller explanation can be found at http://openvpn.net/index.php/documentation/howto.html#pki
To get started, you’ll need to use the Easy-RSA PKI suite.
On Windows machines you’ll find it at: C:Program FilesOpenVPNeasy-rsa
On Linux machines this will probably be installed in an easy-rsa directory machines at /usr/share/doc/packages/opevpn or /usr/share/doc/openvpn-2.0, but it’s a good idea to move this to /etc/openvpn to prevent it getting overwritten by future updates.
Windows: From the Start button select cmd, and in the command window type:
cd "C:Program FilesOpenVPNeasy-rsa
Linux/BSD/UNIX: Open a terminal window and type
cd /etc/openvpn/easy-rsa
(assuming you have moved the easy-rsa directory to this location)
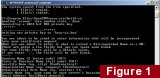
Then type the following commands, followed by return:
Windows:
init-config
vars
clean-all
build-ca
Linux/BSD/UNIX:
./init-config
./vars
./clean-all
./build-ca
Then next step is to generate a server certificate and key, again using the Easy-RSA suite. The command for this is:
build-key-server server./build-key-server serverIn the interactive session that follows, simply press Enter to provide the default value each time, until you are asked for a Common Name. For Common Name enter “server” , then continue entering the default values until prompted to sign the certificate. Answer “y” to this question and to the following one to finish.
Then generate the certificate and key for your client machine. The process is similar to the one for building the server certificate and key, but this time enter client1 as the common name.
If you think you may want to access the OpenVPN server from more than one laptop, repeat the process, replacing client2 or client3 for client1 each time.
build-key client1./build-key client1The final step is to generate Diffie-Hellman parameters for key exchange:
build-dh./build-dh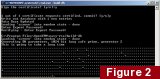
C:WindowsProgram FilesOpenVPNeasy-rsakeys/etc/openvpn/Your public key infrastructure is now set up.
When OpenVPN runs it reads a configuration file at c:Program FilesOpenVPNconfig (Windows) or in /etc/openvpn (Linux/BSD/Unix). This text file contains all the information OpenVPN needs to know to make or receive a connection, so it’s crucial that these files are correct.
The easiest way to get OpenVPN working in the way we want is to edit the highlighted lines in the following config files to match your network setup, save them as a text file and copy them to the appropriate location.
Server configuration file:
#server config file start
local 192.168.1.15 # Change this address to the IP address of the network card attached to your router. To ensure this does not change you need either to have a static local IP address, or to configure your router to always assign this local IP address to your server.
port 1194 # This is the port OpenVPN will run on. Change it to a different port if you prefer
proto udp
mssfix 1400
push "dhcp-option DNS XXX.XXX.XXX.XXX" # Replace the Xs with the IP address of the DNS server for your network
push "dhcp-option DNS YYY.YYY.YYY.YYY" # Replace the Xs with the IP address of the secondary DNS server for your network
dev tap
ca "C:Program FilesOpenVPNeasy-rsakeysca.crt" #change this location to /etc/openvpn (without quotation marks) for Linux/BSD/Unix systems
cert "C:Program FilesOpenVPNeasy-rsakeysserver.crt" #change this location to /etc/openvpn for Linux/BSD/Unix systems
key "C:Program FilesOpenVPNeasy-rsakeysserver.key" #change this location to /etc/openvpn for Linux/BSD/Unix systems
dh "C:Program FilesOpenVPNeasy-rsakeysdh1024.pem" #change this location to /etc/openvpn for Linux/BSD/Unix systems
server 192.168.10.0 255.255.255.128 # This will be the virtual IP address and subnet of the server’s OpenVPN connection. Change it to something similar like 192.168.11.0 if this subnet is already in use
ifconfig-pool-persist ipp.txt
push "redirect-gateway def1"
keepalive 10 120
cipher BF-CBC # Blowfish (default)If you prefer, you can use one of the two ciphers listed below (which must be the same as the client)
#cipher AES-128-CBC # AES
#cipher DES-EDE3-CBC # Triple-DES
comp-lzo
max-clients 3 # Change the 3 to the number of client keys you have created
persist-key
persist-tun
status openvpn-status.log
# user nobody # remove the # at the start of the line for Linux/BSD/Unix systems
# group nobody # remove the first # at the start of the line for Linux/BSD/Unix systems
verb 1
#config file ends
Save this file as server.ovpn, and move it to c:Program FilesOpenVPNconfig (Windows) or /etc/openvpn (Linux/BSD/Unix)
OpenVPN clients connect to the OpenVPN server using a public IP address or host name that needs to be entered into the client config file. If your ISP provides your business or home network with a dynamic IP address that changes each time an Internet connection is reset then your client config will no longer work after a reconnection. To get round this you can get a free hostname from DynDNS which automatically points to your dynamic IP address, even when it changes. To get a dynamic host name (such as myhost.dyndns.org) visit http://www.dyndns.com.
#client config file start
client
dev tap
proto udp
remote XXX.XXX.X.XXX 1194 #Change the Xs to the static public IP address of your home or office network. If you do not have a static IP enter you dyndns name (like yourhost.dyndns.org) here. If you changed the port from 1194 to another port number in the server config change the 1194 here to the appropriate port number
route 192.168.1.0 255.255.255.0 vpn_gateway 3 #Change this to the IP address scheme and subnet of the local network your server is on.
resolv-retry infinite
nobind
persist-key
persist-tun
ca "C:Program FilesOpenVPNeasy-rsakeysca.crt" #change this to “/etc/openvpn/ca.crt” on Linux/BSD/Unix systems
cert "C:Program FilesOpenVPNeasy-rsakeysclient1.crt" # change this to “/etc/openvpn/client1.crt” on Linux/BSD/Unix systems key
key "C:Program FilesOpenVPNeasy-rsakeysclient1.key" # change this to “/etc/openvpn/client1.key” on Linux/BSD/Unix systems. This key file should be kept secret
ns-cert-type server
cipher BF-CBC # Blowfish (default)If you prefer, you can use one of the two ciphers listed below
#cipher AES-128-CBC # AES
#cipher DES-EDE3-CBC # Triple-DES
comp-lzo
verb 1
# user nobody # remove the first # at the start of the line for Linux/BSD/Unix systems
# group nobody # remove the first # at the start of the line for Linux/BSD/Unix systems
# end of client config file
Save this configuration file as a text file called client1.ovpn, and save it to c:Program FilesOpenVPNconfig (Windows) or /etc/openvpn (Linux/BSD/Unix) on your client device
There are a couple of configuration changes that need to be made to the router connected to your server in order for OpenVPN to work properly.
Port forwarding ensures that any traffic sent to your router from the Internet on port 1194 (or the port that OpenVPN is configured to use in the configuration files) is forwarded to the local IP address of your server machine. To ensure this does not change you need either to configure the server machine to have a static local IP address, or to configure the DHCP server in your router to always assign the same local IP address to your server.
To configure port forwarding, log on to your router’s configuration page, find the option for port forwarding, and enter the following information:
Forward to: 192.168.1.15 (change this to the local IP address of your OpenVPN server)
You’ll also the following routing information on your router’s “routing” or “advanced routing” page, to ensure that data can travel between the OpenVPN link and other devices on your home or office network:

openvpn –-config /etc/openvpn/server.ovpn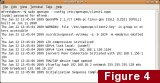
To confirm OpenVPN is working, try pinging another device connected to your LAN using its LAN IP address.
You can also open a browser on your client machine, and check your IP address by visiting a site like http://whatsmyip.org/ If OpenVPN is working correctly the IP address of your server, not your client machine, will be shown.


Paul Rubens is a technology journalist specializing in enterprise networking, security, storage, and virtualization. He has worked for international publications including The Financial Times, BBC, and The Economist, and is now based near Oxford, U.K. When not writing about technology Paul can usually be found playing or restoring pinball machines.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.