

Business, Technology, Internet and network concept.
NAC solutions implement policies for controlling devices and user access to their networks. Review top NAC software now.


Network Access Control (NAC) solutions are network security and privacy solutions designed to reduce risks and improve performance. Businesses use NAC to enforce policies on the devices that can access the network.
NAC technologies typically use a combination of hardware, software, and policy to control access to a network. However, cloud NAC has also become increasingly popular. Policies may be based on authentication, endpoint configuration (posture), or users’ role/identity.
There are two main reasons why NAC solutions are trending. First, the digital surface has expanded with a significant number of new devices connecting to networks, such as IoT, Industrial IoT, and Bring-Your-Own-Device (BYOD). Secondly, organizations must respond with solid security technologies against the global wave of sophisticated cyberattacks and malware network spread.
Here are our top picks for NAC solutions in 2023:
Several features are essential to all NAC solutions. When choosing a vendor, businesses must evaluate features offered against their operational needs to determine whether the technology fits.
From policy enforcement to user profiling, vulnerability scanning and customer support and pricing, find below a comparison chart to help you choose the best NAC solution for your enterprise.
| Policy enforcement and session control | Vulnerability scanning and malware detection | Scalability and integration | User profiling and reporting | Customer support | Licensing and pricing | |
| CISCO ISE | Advanced: Provides compliance | Advanced: Some components have an extra cost | Easy to scale and integrate | Advanced | 24/7/365: Support via web, email, chat, and phone | Complex licensing. Prices available upon request |
| Forescout | Good: Provides compliance through device monitoring | Advanced: With a focus on device monitoring | Scaling and integration may be complex | Advanced: Device diversity is its main strength | 24/7/365: Support via web, email, chat, and phone | Pricing not available online. |
| Aruba ClearPass | Advanced: Includes compliance and incident response | Advanced | Easy to scale. Powerful integration capability | Good | 24/7/365: Support via web, email, chat, and phone | Pricing not available online. |
| Fortinet FortiNAC | Good | Advanced: Cloud-based incident response | Seamless cloud scaling | Advanced: Cloud reports accessible from anywhere | 24/7/365: Support via web, email, chat, and phone | Complex licensing. Prices available upon request |
| Extreme Networks | Good | Good | Advanced | Advanced | 24/7/365: Support via web, email, chat, and phone | Available upon request |
Best for large enterprises with advanced requirements

CISCO ISE Logo. Source: CISCO.
Cisco Identify Services Engine (ISE) is one of the top NAC solutions in the market. The technology is popular among large enterprises with sophisticated network requirements. ISE is a comprehensive, next-generation NAC solution, rich in features.
Companies using ISE can provide highly secure network access to users and devices while having complete visibility across wired, wireless VPN, and 5G connections. It also provides users with information on apps installed and running and vital contextual data, such as user and device identities, threats, and vulnerabilities.
The company differentiates itself from the competition by being a one-stop solution. It also offers self-service onboarding features for BYOD policies, automated device-compliance checks, and central network device management. Cisco offers separate NAC solutions for the industrial Internet of Things (IIoT), operational technology (OT), and industrial controls for medical devices.
CISCO ISE pricing can not only be expensive but difficult to understand. The CISCO ISE licenses plans are numerous, and components and services may only be available with additional costs, depending on the number of users in the network. The new Tier Licenses include Essentials, Advantage, and Premier. Details of each can be found here. Prices are available upon request.
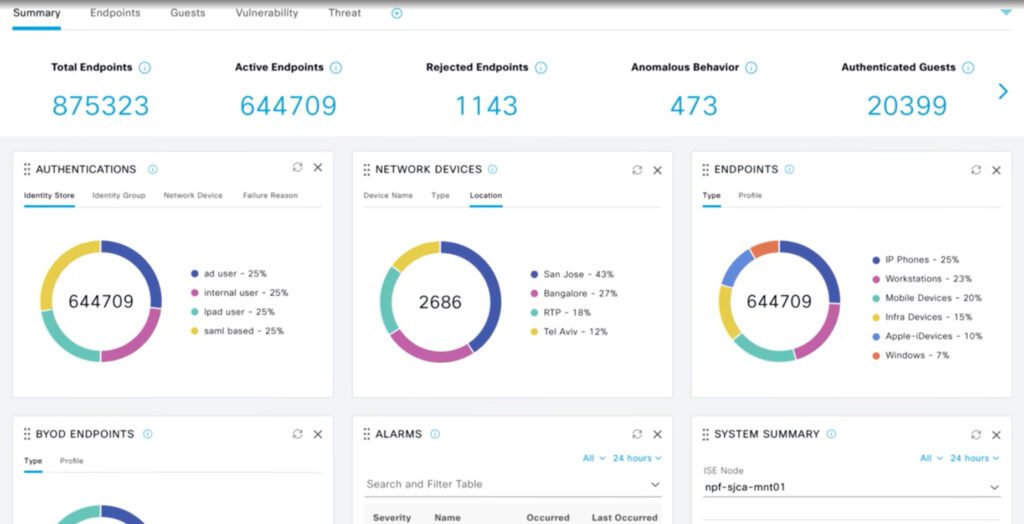
CISCO ISE central visibility dashboard. Source: CISCO.
Best for organizations with user and device diversity

Forescout Logo. Source: Forescout.
Since 2021 when Forescout was recognized as the Customer Choice by Gartner Peer Insights’ “Voice of the Customer” NAC report, the company has consolidated its reputation for offering a robust solution to manage all types of devices.
With an easy-to-use platform and seamless deployment, sided with good support, companies can implement Forescout zero trust access on their networks for a vast array of devices and connected things — including employee devices returning to the office post-COVID, remotely connected devices, transient devices, guest/BYOD devices, and IoT, OT, and smart devices.
Additionally, the company provides modern NAC features, including automated remediation, access control implementations, monitoring, and management and insights.
Forescout does not provide online pricing information. The company does offer a licensing guide that details the hardware and software products. The platform can be deployed on physical on-premises or cloud and edge virtual appliances, as well as smaller use cases licenses.
Forescout products include:
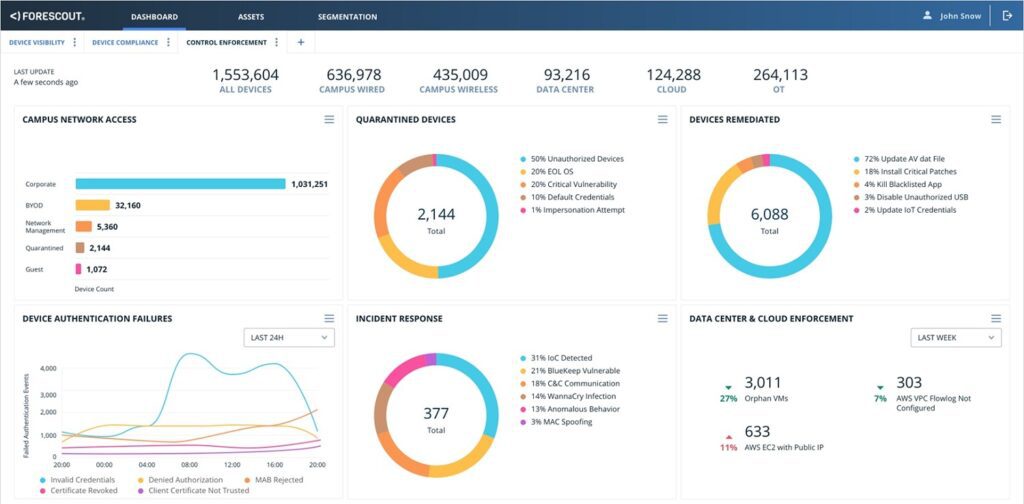
Forescout dashboard. Source: Forescout.
Best for SMBs

Aruba HPE. Source Aruba ClearPass.
Aruba Clearpass, a Hewlett Packard Enterprise company, is popular among SMBs looking to authenticate, authorize, and enforce secure network access control with role-based network policies based on zero trust security.
The solution innovates with AI-powered visibility, robust integrations and state-of-the-art security. ClearPass is available as hardware or as a virtual appliance. It is also a vendor-agnostic technology that works seamlessly with third-party network devices. Besides its Clearpass solution, Aruba offers network switches, access points, and cloud-based technologies. Its ease of use and price make it an SMB favorite.
There are three significant licenses for Aruba ClearPass: Platform Licenses, Base Applications, and add-on Applications. Platform licenses and base applications are required for deployment, while add-ons extend functionality and are optional.
The solution can be purchased as virtual technology or as hardware. For a detailed explanation of ClearPass licenses, you can watch the following official video. The company does not provide pricing information online; it is only available upon request.
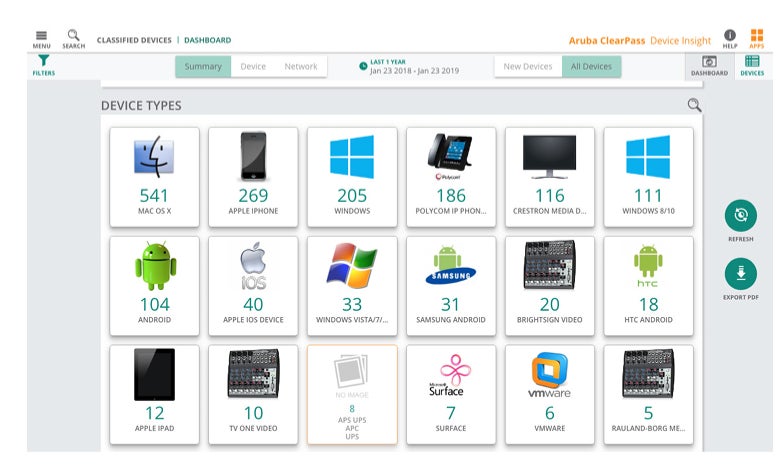
Aruba ClearPass device insight dashboard. Source: Aruba.
Best for cloud-based NAC solution
FortiNAC logo. Source: Fortinet.
FortiNAC is a comprehensive NAC solution that provides visibility, control, and security for all devices connecting to your network. Although it can be deployed on-premises or in the cloud, its cloud version leads in the market due to its rapid deployment, scaling, and management.
The solution is a good option for organizations of all sizes. It is easy to deploy and manage and it offers a wide range of features and capabilities that can help you protect your network from various threats.
FortiNAC pricing can be complex as it varies depending on what products and services the customer needs. The company offers hardware and virtual machines for network controls.
Additionally, its platform can be acquired under three plans, Base, Plus, or Pro. Licenses can be perpetual or subscription-based and depend on the number of endpoints in the network. Details are explained in this official guide on FortiNAC licenses.
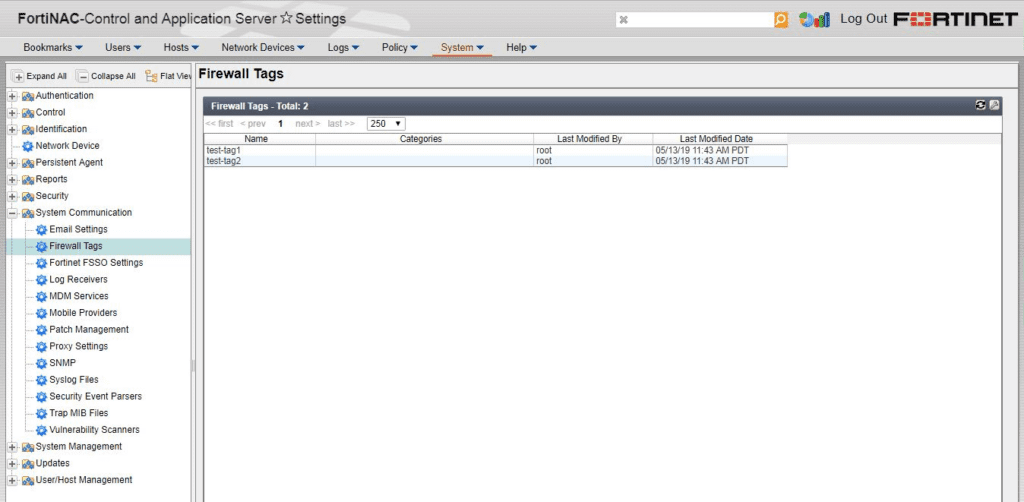
FortiNAC Control and Application Server Settings dashboard. Source: Fortinet
Best for integrating NAC solutions to existing infrastructure

Extreme Networks ExtremeControl Logo. Source Extreme Networks.
ExtremeControl, a product of Extreme Networks, is a flexible and scalable technology that can be deployed in a variety of ways, making it the best for integrating NAC solutions to existing infrastructure.
ExtremeControl can be deployed on-premises, in the cloud, or a hybrid environment. ExtremeControl can also be integrated with other security solutions, including firewalls, intrusion detection, and identity management systems.
Pricing information is only available upon request. Plans and licenses vary depending on the customer’s on-premises technology or cloud needs. ExtremeControl can be purchased as a perpetual license or in subscription models. Prices vary depending on the number of users and features required.
ExtremeControl Extreme Networks. Source Extreme Networks.
As a rule, NAC software should include policy enforcement and session controls, vulnerability scanning and malware detection, and user profiling and reporting capabilities. You’ll also want to consider each solution’s scalability, customer support, and of course its pricing matrices.
Enforcing policies on devices connecting to the network is a fundamental feature of all NAC technologies. This can include policies such as requiring devices to be patched, requiring devices to be encrypted, or requiring devices to be registered with the network.
NAC solutions scan devices for known vulnerabilities. This information can be used to block devices with known vulnerabilities, quarantine devices until they are patched, or remediate vulnerabilities.
Networks are ever-changing environments that can scale up or down and NAC solutions must be able to pivot rapidly, offering customers easy-to-use scalability. When traffic increases, NAC tools must be able to manage it by scaling without affecting performance or compromising security.
Additionally, integration is essential in the modern digital era. NAC platforms and hardware must integrate with other security solutions, such as firewalls, intrusion detection systems, and antivirus software.
Profiling users and devices is another crucial component of NAC systems. They should offer visibility into performance, risks, vulnerabilities, and network status. Administrators can block unauthorized devices, quarantine infected devices, or remediate vulnerabilities by profiling users.
Reporting is also fundamental. It can be used to make data-driven decisions about the network, present compliance and security reports, and better understand users, credentials, certificates, and more.
NAC solutions can be highly advanced, therefore having solid, dependable customer support can make a big difference.
As a rule of thumb, NAC vendors do not disclose pricing online. Their products, services, solutions, and licenses can also be complex. To understand the costs, and whether they align with your company’s budget, you’ll need to reach out to each vendor’s sales team and do your research.
Choosing the best NAC software for your business depends on several factors, including your organization’s size, industry, and security needs. Before taking the leap, consider what NAC solutions are the best for your business size and network demands.
Also take into consideration your industry. Some vendors offer specialized NAC technology for healthcare and IIoT for manufacturing. The number of users, contractors, and guests on your network will also be a defining factor.
No matter which NAC solution you choose, it is important to ensure it is properly implemented and configured. Do your research, get quotes from multiple vendors, make sure the service and products align with your business goals, and consider your needs and compatibility.
NAC stands for Network Access Control. Companies offering NAC solutions usually sell software, licenses, hardware, cloud platforms, and virtual machines to create a security framework that helps organizations control who and what can access their networks.
NAC solutions typically use a combination of policies, enforcement mechanisms, and profiling tools to assess the security posture of devices and users before granting them access to the network.
Policy enforcement in NAC ensures that devices and users comply with the organization’s security policies.
Policy enforcement is an essential part of NAC because it helps to protect the network from unauthorized access, malware, and other threats. By enforcing security policies, users can ensure that only authorized devices and users can access the network.
The number of devices connecting to a network has increased exponentially in recent years. This creates a problem, as the digital attack surface of companies keeps increasing, giving cybercriminals more chances to find vulnerabilities.
Knowing which devices and users are connected also allows administrators to manage traffic and privacy and gain critical insight into a network. Companies can enforce security and authentication by identifying and profiling users and devices, preventing malware infections, and shutting down unauthorized users.
From GDPR to the Payment Card Industry Data Security Standard (PCI DSS), the Health Insurance Portability and Accountability Act (HIPAA), and other national and international laws, NAC solutions can help companies stay compliant with regulations by enforcing security policies, preventing unauthorized access and providing visibility.
Additionally, some NAC technologies offer compliance reporting capabilities that companies can leverage when presenting reports to authorities.
There are a few reasons why NAC solutions rarely provide pricing online. But most importantly, NAC technologies vary greatly depending on the needs of an organization, including the type of network, if they need hardware or software, and how many users and devices the network has.
Many NAC solutions are sold as part of a larger security suite, which includes other security products such as firewalls, intrusion detection systems, and antivirus software.
While NAC technology can run vulnerability scanning and malware detection, you still need threat detection. Threat detection solutions can help to identify and respond to threats that have already bypassed NAC controls. Furthermore, NAC solutions work together with threat detection technologies providing a multilayered approach to network security.
NAC can help to improve the security and performance of a network in several ways, including:
NAC can be complex and challenging to implement.
Some of the challenges of NAC include:
We looked into the best-performing vendors and alternatives to write our review and evaluate the top NAC solutions and features. We examined sites that compile aggregate data based on verified user reviews. We also reviewed demos on vendor sites, test-drove the software when possible, and scoured through the official sites of the featured vendors to evaluate their features, customer service, user-friendliness, price, and scalability.
Driven by the global digital transformation that followed the post-pandemic era, NAC solutions have become vital privacy and security solutions. NAC technology manages and monitors devices, enforces policies, identifies security weaknesses and leverages automation and AI to make your networks better and safer.
If you are looking to gain visibility in your network, reduce data breaches, enforce policies, reduce costs, and increase performance and security, NAC solutions can help you to achieve these goals.
For more tips on improving your network security profile, here’s a quick guide to conducting a network security audit at your organization.


Ray is a Content and Communications Specialist with more than 15 years of experience. He currently works at Publicize and as a contributing writer for TechRepublic, eSecurityPlanet, and ServerWatch in addition to Enterprise Networking Planet. His work has also been published in Microsoft, Venture Beat, Forbes, Entrepreneur, The Sunday Mail, FinTech Times, Spiceworks, Dice Insights, Horasis, the Nature Conservancy, and other leading publications.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.