Last week we took a diveinto the whys and wherefores of VLANs (Virtual LANs) on Linux, and established some terminology in order to stave off any possible failures to communicate. This week we’re going to use our inexpensive but excellent smart Ethernet switches to create some port-based VLANs. These are the easiest, because all configuration is done on the switch. Next week we’ll wrap up this series with a howto on Tag-based (IEEE 802.1Q) VLANs. These require network gear that supports VLAN tags, and you’ll need to configure routing and all client hosts. They’re more work to set up, but you can do more with them.
Port-Based VLAN
This is the easiest VLAN to create. Remember to label your cables, and all will be well. Suppose your network looks like this:
broadband modem
router/firewall
8-port switch
12345678
lan hosts
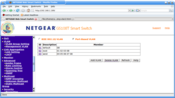
This artistic ASCII network diagram represents a simple network; this could be any home or small business network. It shares a single broadband Internet connection, which connects to a router/firewall, which goes to an eight-port Netgear GS108T smart switch. (Of course you may use any smart or managed switch that you like.) Figure 1 shows what configuring three port-based VLANs looks like on the Netgear control panel.
So now you have three subnets on a single switch, Default, East and West:
broadband modem
router/firewall
east west default
123 4567 8
East and West cannot communicate with each other, but they share Internet. The way to share an Internet connection with all VLANs on this switch is to have a port common to each VLAN, and plug the router/firewall into this port. On the Netgear it doesn’t matter — you could use any port for the common Internet port. The administration manual recommends Port 8, but any of them will work. Be sure to read your own administration manual, because VLAN 01, or whatever the default VLAN is for your switch, may be encumbered with some hard-coded functionality.
When is a Switch Like a Router?
Port-based VLANs are specific to their switches, and cannot cross multiple switches. However, you can make a smart switch function like a router. Let’s say that three ports are not enough for VLAN East; you want to connect more hosts. You could buy a bigger smart switch. Or you can uplink a second switch to one of VLAN East’s ports, like this:
broadband modem
router/firewall
east west default
123 4567 8
| 2nd switch
12345678
Now East can have nine members. The second switch can be a smart switch, dumb switch, or even a hub. (If you have the budget for it, stackable switches are nice and tidy.) When you uplink switches this way, be sure that the upstream switch is the VLAN-configured switch. Everything connected to the second switch is a member of East; you can’t divide it between East and West. West can be expanded in the same way. Don’t try to set up VLANs on the second switch, unless you enjoy driving yourself crazy with things that don’t work.
Port-based VLANs allow ports to belong to multiple VLANs, which gives you some nice flexibility. For example, you can make every switch port a member of a separate VLAN, and connect a second switch to each port to connect multiple hosts. So using our example 8-port smart switch, you could create seven separate VLANs that share only an Internet connection. Or you could assign port 7 to a shared printer, and have 6 separate VLANs that cannot talk to each other, but do share a printer and Internet.
Let’s look at how to share a printer across multiple VLANs. In this example we’re using a 16-port switch, so we’re not quite so squished:
broadband modem
router/firewall
01 east west north south 05
1 234 5678 9 10 11 12 13 14 15 16
printer
If you make ports 1 and 16 common to all four VLANs, all four VLANs will have Internet and share the same printer. The VLAN port assignments look like this:
VLAN ID Ports 01, default 1,16 02, east 1,2,3,4,16 03, west 1,5,6,7,8,16 04, north 1,9,10,11,12,16 05, south 1,13,14,15,16
If the rowdy girls in West get out of hand and abuse their Internet or printing privileges (they’re a wild bunch, so probably both) all you do is remove ports 1 and 16 from the West VLAN, and there’s not a darn thing they can do about it. Actually, if they downloaded the dnsniff suite of switched-network sniffing and auditing tools before you changed their VLAN memberships they’ll still be plenty of trouble. But you can disable their switch ports, or even yank the physical plugs, so you’re still in charge. The movie “Colossus: The Forbin Project” should be required viewing for everyone in any kind of technology field, as a lesson in the importance of always having physical plugs to pull.
What if you want west and north to communicate with each other? Put them on the same VLAN. There is one additional useful option, and that is to create master IT port, so that you as the master of the network can easily go anywhere you want on the network. Add one more port to the default that is not used by anyone else, like port 2 in this example:
VLAN ID Ports 01, default 1,2,16 02, east 1,3,4,16 03, west 1,5,6,7,8,16 04, north 1,9,10,11,12,16 05, south 1,13,14,15,16
Any PC connected to switch port 2 has access to the entire network. But port 2 is not a member of any other VLAN, so this keeps all control in VLAN 01.
Additional Routed Subnets
Now take a look at our next beautiful ASCII network diagram. This shows a common scenario even in very small networks- a second routed subnet, which is the wireless network segment. To make the diagram easier to read I’m using a separate wireless access point, but the WAP could also be integrated into the firewall/router:
broadband modem
|
router/firewall
| |
| |________WAP-192.168.2.0/24
|
east west default
123 4567 8
192.168.1.0/24
If you had routing enabled between 192.168.1.0/24 and 192.168.2.0/24 before you created your East and West VLANs, nothing has changed- all the hosts in East and West can still communicate with your wireless hosts. Because to your router, East and West are still a single subnet. This is a limitation of port-based VLANs &emdash; there is no information added to the packets to identify them as belonging to a VLAN, so once they leave the switch it’s as though the VLANs do not exist. So you still need to pay attention to addressing, and not have any duplicate IP addresses in your various VLANs.
Routing VLANs
Tag-based (IEEE 802.1Q) VLANs are more flexible and are routable, just like ordinary physical subnets. Next we’ll learn how to set them up, how to route them, and how to configure Linux clients.