

Image: Maksim Kabakou/Adobe Stock
Symmetric and asymmetric encryption are the main encryption types. Learn what each of them mean and discover examples of how they’re used now.
Encryption is a critical component of modern information security that transforms data into an unreadable format, safeguarding it from unauthorized access. The process involves turning readable data, known as plaintext, into an unreadable format called ciphertext using a specific algorithm and a key. Only those who possess the correct key can decrypt the ciphertext back into plaintext and read it.
There are two primary types of encryption: symmetric and asymmetric.
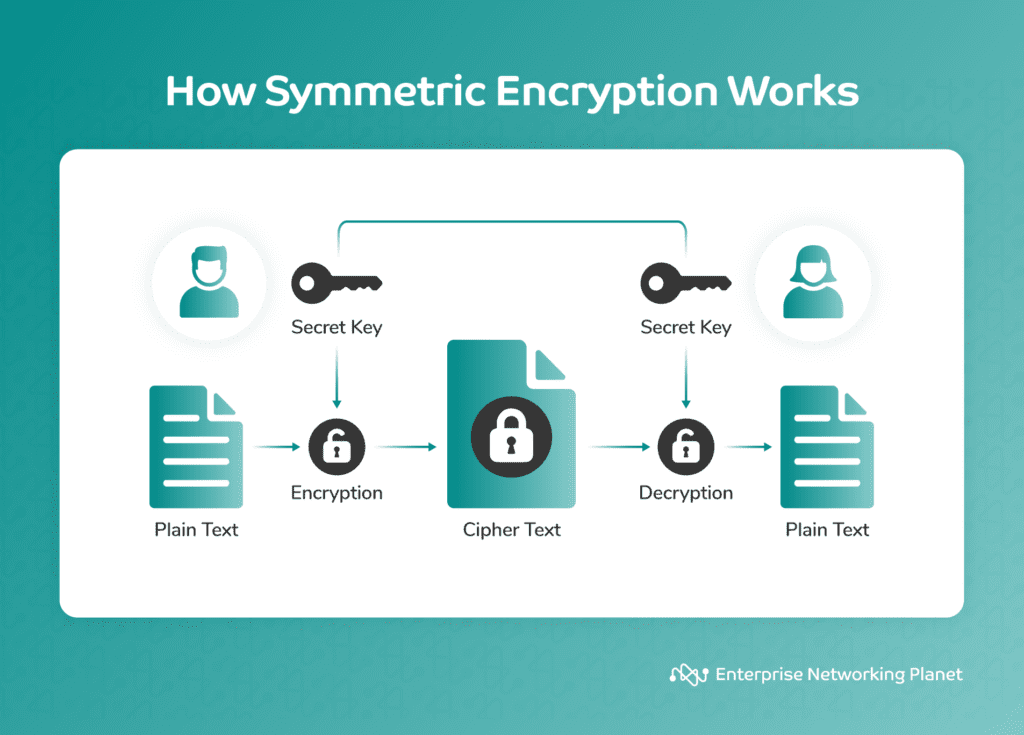
Symmetric encryption, also known as secret key encryption, involves the use of the same key for both encryption and decryption. It is fast and efficient, making it ideal for encrypting large amounts of data.
While this encryption method promotes speed and efficiency, it is less secure than asymmetric encryption because it uses a single key for both encryption and decryption. This makes it easier for hackers to break the code.
Symmetric encryption is the ideal choice for rapidly encrypting large amounts of data. It plays a key role in the Advanced Encryption Standard (AES) used by the U.S. government to encrypt classified information. It is also suitable for parties already sharing a secret key, especially when speed and efficiency are of utmost importance.
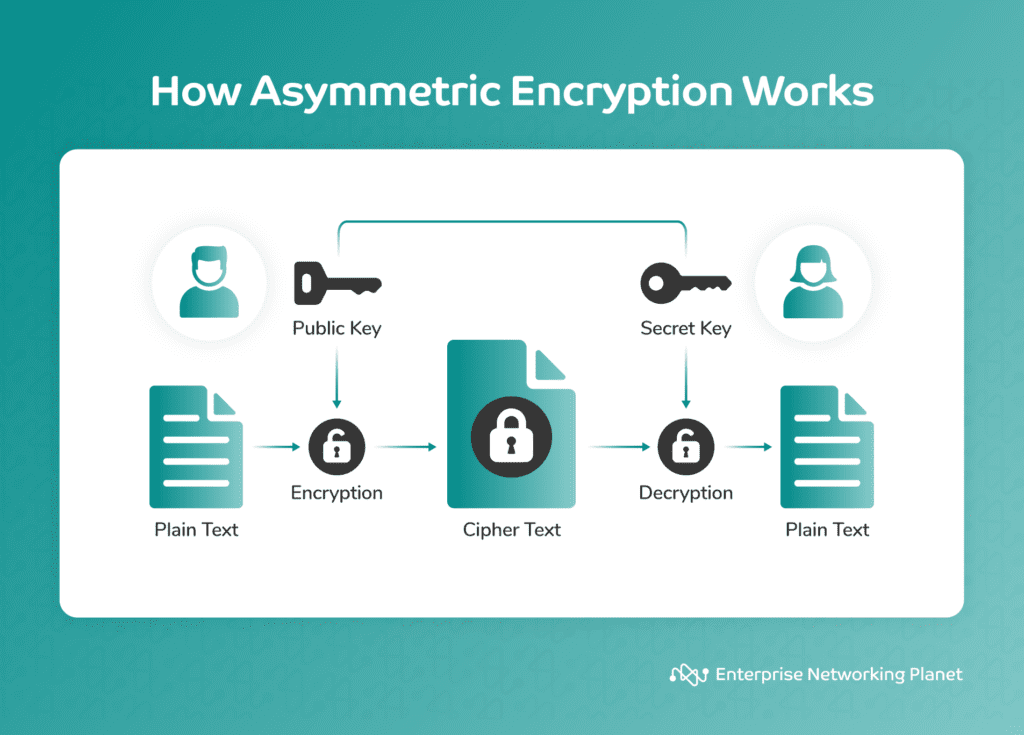
Asymmetric encryption, also referred to as public key encryption, employs two distinct keys: one for encryption, which is public, and another for decryption, which is private. Entities may use this encryption to protect data and key exchanges over open, insecure channels. They also use it to authenticate and ensure data integrity.
This encryption is slower and less effective compared to symmetric encryption, but offers heightened security due to the public key’s shareability while keeping the private key confidential.
Asymmetric encryption is suitable for situations that require secure key exchange over an unprotected medium, like the internet. It finds common usage in secure email (PGP), secure websites (HTTPS), online transactions, and digital signatures.
This encryption provides a solution for two parties to communicate privately without the need to share a pre-established key.
Let’s look at the most popular encryption algorithms for symmetric and asymmetric encryption.
Symmetric encryption algorithms include AES, DES, 3DES, Blowfish, and Twofish.
AES is prevalent in secure communications, data storage, and various encryption tools. It uses block ciphers with key sizes of 128 bits, 192 bits, or 256 bits.
Used in:
Users widely relied on DES, a symmetric encryption standard, in the past. However, it has become less secure than AES and is vulnerable to brute-force attacks. It uses a 56-bit key, and most have replaced it with more secure algorithms.
Historically used in:
3DES is a more secure variant of DES. It applies the DES algorithm three times in succession with different keys, providing stronger encryption.
Used in:
Various applications have used Blowfish, a symmetric-key block cipher known for its simplicity and speed. However, it’s less common today because more secure alternatives are available.
Used in:
Some security-conscious applications have used Twofish, another symmetric-key block cipher, mainly as an alternative to AES. However, it did not achieve as wide adoption as AES.
Used in:
Asymmetric encryption algorithms include RSA, ECC, DH, ECDH, DSA, and EdDSA.
RSA is a widely used public-key encryption algorithm for secure data transmission. It relies on the mathematical properties of large prime numbers.
Used in:
ECC delivers strong security with relatively small key sizes, making it suitable for resource-constrained devices like smartphones.
Used in:
This mechanism enables two parties to craft a shared secret key, even over an unsecured channel. This shared secret key forms the cornerstone of their secure communication.
Used in:
ECDH combines Diffie–Hellman with elliptic curve cryptography, offering reliable key exchange with strong security.
Used in:
DSA is an asymmetric algorithm used for digital signatures to verify data authenticity and integrity.
Used in:
EdDSA is a more modern elliptic curve-based algorithm, known for its effectiveness and security in digital signature applications.
Used in:
Symmetric and asymmetric encryption each play unique roles in data and network security.
Symmetric encryption excels in speed and efficiency, making it the go-to choice for encrypting large volumes of data and tasks like data storage and high-speed network communication.
Despite its slower speed, asymmetric encryption offers a robust security framework with its key distribution mechanism, proving essential for secure email, digital signatures, secure web browsing, and secure communications over untrusted networks.
The decision between symmetric and asymmetric encryption isn’t about which method is superior. Instead, it’s about choosing the right tool for the job to ensure optimal data security. This choice hinges on the specific security needs and operational requirements of a given system.
A well-designed security strategy might combine both encryption types to tackle diverse security challenges in the digital age. As security threats continue to grow, it becomes increasingly urgent to understand the strengths and weaknesses of these encryption methods. This understanding aids in making informed decisions about securing your organization’s sensitive information and communications.
Take the next step in your encryption journey and master encryption. Don’t miss out on our guide to the best encryption software to keep your data protected.
Liz Laurente-Ticong is a tech specialist and multi-niche writer with a decade of experience covering software and technology topics and news. Her work has appeared in TechnologyAdvice.com as well as ghostwritten for a variety of international clients. When not writing, you can find Liz reading and watching historical and investigative documentaries. She is based in the Philippines.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.