Controlling and managing the security of endpoints on an enterprise network is usually a complex and thankless task that requires the deployment of multiple tools. Enterprise security products vendor ESET aims to eliminate that complexity with a flexible management solution for endpoint security management. ESET Remote Administrator (ERA v6) offers multiple deployment scenarios, ranging from […]
Controlling and managing the security of endpoints on an enterprise network is usually a complex and thankless task that requires the deployment of multiple tools. Enterprise security products vendor ESET aims to eliminate that complexity with a flexible management solution for endpoint security management. ESET Remote Administrator (ERA v6) offers multiple deployment scenarios, ranging from legacy 32-bit Windows servers to the 64-bit Windows Servers of today to self-contained virtual appliances that can run under a number of hypervisors and onsite, remotely, or in the cloud.
ERA v6 is the management half of ESET’s endpoint security solution, and is used to provision, control and policy-enable ESET’s complete anti-malware and security suite on enterprise endpoints, including mobile devices and most anything else that connects to the network. In short, ERA v6 aims to ease the management of dozens, hundreds, or thousands of endpoints using ESET’s endpoint security products.
The ERA agent, a small application that runs on endpoints and enables endpoints to be fully managed and protected by ERA v6, tightly integrates ERA v6 with endpoints. This tight integration is critical, as ERA v6 wears multiple hats so that a network security administrator doesn’t have to. Case in point: ERA v6 combines everything from client software deployment (agent and AV), endpoint updates, policy enforcement, and security control management into a single management console, which also acts as fully instrumented dashboard.
Other advantages offered by ERA V6 include:
ERA v6 supports multiple installation scenarios, leverages browser-based consoles, and offers unified endpoint security management. Embracing the growing demand for enterprise-level virtual appliances is a good move, as evidenced by the ease of installation associated with the company-provided OVA (Open Virtualization Appliance) file, which can be imported directly into a virtual server environment such as VMware (vSphere, Player, Workstation), Oracle Virtual Box, ESXi, or Microsoft Hyper-V.
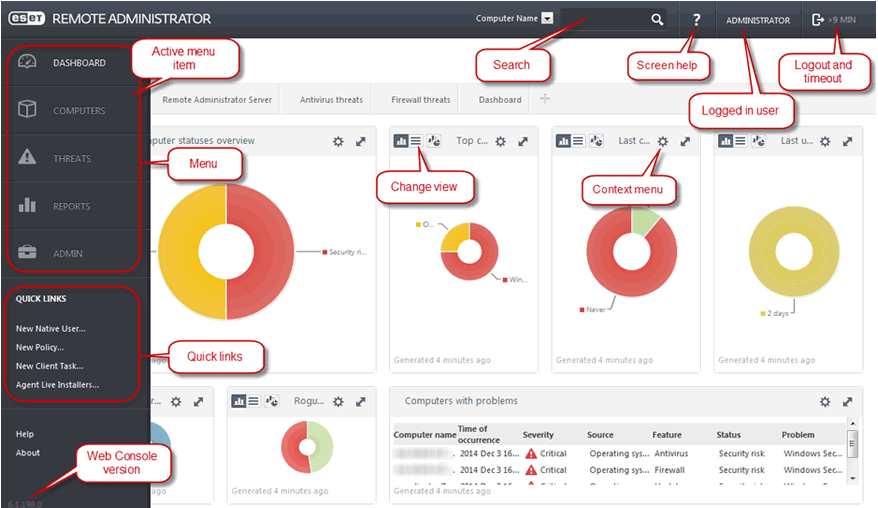
ERA v6 Main Console
The OVA file contains a fully functional CentOS 6.5 operating system and all of the ERA v6 software, allowing administrators to quickly create a virtual server instance of ERA v6. This eliminates the need for a dedicated server or enterprise-level ESXi implementation, provides the ability to use a desktop OS to host the hypervisor, and allows administrators to deploy ERA v6 on a non-server OS.
For those not wanting to venture down the virtual appliance route, ESET also offers wizard-based installation for Windows and Linux, which proves even simpler than OVA-based installation, auto-installing perquisite elements, such as SQL server. However, it is still a good idea to have .Net and JAVA pre-installed on the target management server system.
Once installed, administrators can launch the ERA v6 management console using a browser and the IP address provided during the installation process. The console offers users guided configuration steps and wizard-driven capabilities to further ease initial setup. Wizards, interactive help, and guided processes are offered throughout the product and are available for most any process.
As stated earlier, ERA v6 requires that the ERA agent be installed on endpoints to enable manageable security. In the past, pushing agent software out to an endpoint required several manual steps, and sometimes interaction with the end user, with the worst-case scenario involving need to send a technician out to physically install the agent on the endpoint.
ESET attempts to eschew some of the manual steps of agent installation by offering a feature called “Server Assisted Agent Installation,” which provides the local installer with the needed certificates from the ERA server. Beyond that, the help file offers several different scenarios and options to ease the installation of the agent. Administrators can also use a feature called the ERA Agent Live Installer, which pushes out a preconfigured Live Installer package from the ERA server in the form of a batch file, which can be run as part of a login script or using other automation technologies. It can even be emailed as a link to the end user. Finally, administrators can conduct a remote installation, which can be a major time saver on enterprise networks.
Remote installation is executed via the ERA management console’s Server Task menu as a function of the Agent Deployment wizard, which is then used to identify target systems. The administrator will need to provide the suitable credentials for the target endpoints, which should not be a problem on a managed network, especially a Windows network using Active Directory.
Speaking of Active Directory, it is important to note that ERA v6 offers full integration with AD, allowing the product to query critical information. AD integration further simplifies deployment as well as management of security settings on various PCs throughout the enterprise.
Beyond the basics outlined above, ERA v6 offers several critical features to secure enterprise networks. First and foremost is the product’s ability to administer ESET Endpoint v6 security products. ERA v6 offers full control of the settings, policies, updates and deployment of security on the endpoint, while also providing the tools to monitor and report on those endpoints.
As security management tools go, ERA v6 brings to the table several other features that are quickly becoming necessities for security administrators today. Of particular note is the rogue system detection capability, which looks for and reports on unprotected systems connecting to the network. That proves critical on today’s networks, where spyware and malware can infect complete networks when a compromised system connects.
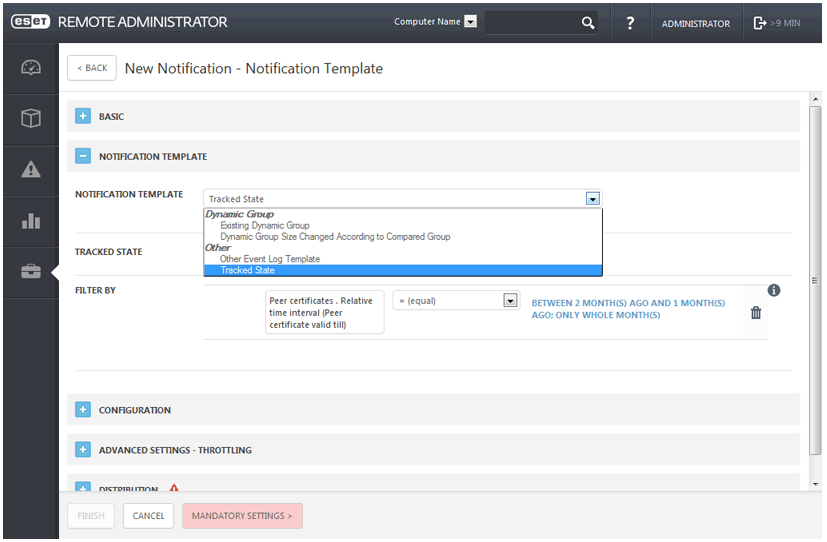
ERA v6 Notifications
Advanced reporting features are also readily apparent in the product. Administrators can use the integrated report writer to build custom reports if the hundreds provided do not meet their specific needs. Reports can include graphical elements, such as charts and diagrams. Numerous filters and sort options are also part of the reporting engine.
Arguably one of the most important features is the ability to create custom policies and define dynamic groups. Administrators can use the product’s wizard based tools to create and enforce policies that include everything from security settings to software deployment to most anything one can imagine. Furthermore, policies can be applied to specific machines, groups, and domains, or even executed based upon Boolean logic.
While full automation is nice to have in a network security product, nothing beats staying informed. Here, ERA v6 offers a notification system that uses a wizard to define what events should be reported to administrators and how those notifications are delivered. For example, a SIEM (Security Incident Event Management) system can be used to send notifications can sent via email, or other methods.
Conclusion
ERA v6 brings together all of the needed management components in an easy-to-use Web console that allows administrators to focus on the issues that matter and not waste precious time configuring desktops, while still ensuring that endpoints are fully protected from the ills of malware.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.