
Person's hands on computer keyboard with keys reading "Firewall Rules."
A firewall rule is a set of conditions that allows or denies network traffic. Learn more about firewall rules now.

When it comes to online security, firewalls are an essential tool for protecting data and networks from malicious cyberattacks. A firewall is a system designed to control access between networks, computers, and other systems.
Firewall rules are an important part of this security system, as they determine which network traffic will be allowed to pass through the firewall and which traffic will be blocked. By having a clear set of firewall rules, businesses can protect their systems from potential threats while allowing legitimate users to access the services they need.
Firewall rules are instructions that control how a firewall device handles incoming and outgoing traffic. They are access control mechanisms that enforce security in networks by blocking or allowing communication based on predetermined criteria. These criteria include source or destination IP addresses, ports, protocols, and services.
Depending on the type of firewall, the rules may also dictate which users or groups have access to specific applications or where certain data is allowed to travel within the network. For the rule to be effective, it must be explicitly defined and enabled in the firewall configuration.
A firewall evaluates each incoming and outgoing data packet against the firewall rules. If the packet matches one of the rules, the firewall allows the packet to pass through to its destination. Otherwise, it rejects and (if programmed to) reports it.
Firewall rules are configured as access control lists (ACLs), which are ordered lists of permissions defining traffic allowed or denied. A typical ACL includes an action (allow, deny, or reject) followed by conditions or parameters traffic must meet before the action is applied.
To ensure security, firewalls often use a “deny by default” policy, meaning that any traffic that doesn’t explicitly meet the criteria laid out in the firewall rules will be denied.
For a very simple example, you might have a rule that says, “Allow any traffic from IP address X to port Y.” When a packet arrives at the firewall, the firewall reads its source and destination. If the packet’s source is X and its destination Y, it passes through. If, on the other hand, its source is Z—or if its source is unidentified—and destination is Y, it is denied.
Firewall rules are stored in a firewall configuration file containing the rules and settings for a given firewall. The configuration file usually resides on the server running the firewall.
The configuration file is accessed and modified by the network administrator, who adds new rules or modifies existing ones as needed. These changes are then saved and applied to the firewall, so they can take immediate effect. Depending on the type of firewall, the rules may be stored in different locations, such as a registry or even an external database.
Firewall rules are applied top-down, meaning the firewall starts with the first rule created and runs through the full sequence in order of creation. SANS Institute’s firewall checklist recommends the following order when creating and setting up firewall rules:
To ensure the best security possible, it’s important to follow certain best practices when configuring firewalls, including documenting rules across devices, monitoring firewall logs, and implementing least-privileged access.
Document all firewall rule configurations and ensure these documents are updated frequently. This enables administrators to review the current setup and make any necessary changes if any threats or vulnerabilities are detected in the network’s security.
Documentation clarifies why the rule exists and the challenges it solves. That way, administrators can quickly assess whether or not the rule should remain active, which helps limit the risk of attackers finding a loophole. It also serves as an audit trail for compliance purposes.
Always start with a deny by default policy (also known as deny any/any), meaning deny all traffic unless explicitly allowed. This ensures new threats cannot penetrate the network unidentified. It’s better to accidentally block some legitimate traffic and then manually override than to allow through a potentially devastating threat.
Regularly monitoring firewall logs is essential to maintaining good network security. Logging allows administrators to track traffic flow throughout the network, look for suspicious activity, and troubleshoot problems. Monitoring firewall logs also provides insight into who is using the system and for what purpose.
By tracking activity levels, it’s easier to see if there’s a sudden increase or decrease in usage, which could indicate an attack has occurred. Depending on the complexity of the organization’s infrastructure, logs from individual components of the system, such as routers, servers, and switches, can be aggregated into one centralized place for analysis and alerting.
Grouping firewall rules to simplify the rule structure is vital to reducing complexity and optimizing the performance of a firewall. Grouping rules with similar characteristics like source or destination addresses, protocols, ports, or services will help minimize the number of rules required and make the overall ruleset easier to manage.
Additionally, segmenting the network into different zones and applying firewall rules to each of those zones can help control traffic flows, reduce the likelihood of unintended exposure, and improve the speed and performance of the firewall.
Configure firewalls to allow only certain applications and services, such as web browsers and mail clients, as opposed to every application that attempts to access the network. This provides an additional layer of security by restricting what applications can connect with the network.
Monitor mode is a rule configuration that lets administrators observe, but not block, network traffic before creating a firewall rule. It allows them to review the current network traffic, identify and allow necessary traffic, and create rules to allow or deny additional traffic.
When using monitor mode, administrators use IP addresses and ports to identify the traffic and ensure it’s necessary. Once the traffic is identified, administrators can compile a list of source IPs, destination IPs, and destination ports and begin categorizing the traffic to create appropriate firewall rules.
Restrict user access to the minimum privileges required to perform their tasks. This ensures that only those users who need access to a particular service or resource can gain it.
For example, if a user doesn’t require FTP access for their job duties, the administrator should configure the rule to prevent it. This rule configuration limits the risk of both accidental and intentional unauthorized access to sensitive information or resources.
Firewalls that have not been appropriately managed tend to become cluttered with redundant and unnecessary rules. Make sure to regularly check for and remove any unnecessary or overlapping rules that may be clogging up the system and causing confusion.
Just like any security measure, it’s vital to keep firewalls up-to-date with current threats. To do this, reviewing firewall rules and updating them regularly is essential. This includes ensuring all security policies remain consistent and all threats are handled quickly and effectively.
SANS Institute’s firewall checklist recommends blocking outbound traffic that uses the following ports:
| Service | Port | Port number |
| DNS Zone Transfers | TCP | 53 |
| TFTP Daemon | UDP | 69 |
| Link | TCP | 87 |
| BSD Unix | TCP | 512-514 |
| Small service | TCP and UDP | 20 and below |
| SMTP (except external mail relays) | TCP | 25 |
| NetBIOS in Windows NT | TCP and UDP | 135 |
| NetBIOS in Windows NT | UDP | 137 and 138 |
| IMAP | TCP | 143 |
| LDAP | TCP and UDP | 389 |
| Syslog | UDP | 514 |
| Cisco AUX port | TCP | 2001 |
| Cisco AUX port (Stream) | TCP | 4001 |
| Cisco AUX port (binary) | TCP | 6001 |
| Common high order HTTP ports | TCP | 8000, 8080, and 8888 |
Blocking these ports can help reduce the risk of malicious activity on a network by preventing unauthorized access to certain services. Additionally, many organizations block certain ports related to online gaming and peer-to-peer (P2P) file sharing to minimize bandwidth usage on their network.
Depending on the type of security system in place, there may be many different types of firewall rules that can apply. Some of the most common firewall rules include:
Firewall rulesets can be configured to block or allow traffic based on criteria such as source address, source port, destination address, destination port, and an indication of whether the traffic should be permitted or denied.
| Source address | Source port | Destination address | Destination port | Action |
| 192.168.1.2 | 80 | 10.10.10.20 | 22 | Allow |
| 10.10.0.0/24 | Any | 192.168.0.0/24 | 443 | Deny |
| Any | Any | Any | Any | Deny |
The above example firewall rules would permit traffic from 192.168.1.2 on port 80 to 10.10.10.20 on port 22, while denying traffic from 10.10.0.0/24 to 192.168.0.0/24 on port 443 and denying any incoming traffic from any source address and port.
By defining a set of rules, administrators can control which traffic is allowed and which traffic is blocked, thus providing an additional layer of security to their network.
pfSense is an open-source firewall and router distribution based on FreeBSD. It’s designed to be a firewall, virtual private network (VPN), router, and wireless access point (WAP). It supports many popular network technologies such as IPv4, IPv6, OpenVPN, Snort, and pfBlockerNG. It’s primarily used as a firewall and router to secure networks in commercial and enterprise environments.
Here’s how to create a firewall rule in pfSense.
Step 1: Log in to the pfSense web interface.
Step 2: Navigate to Firewall, then select Rules.
Step 3: Select the pfSense network device (e.g., WAN or LAN device) of your preference.
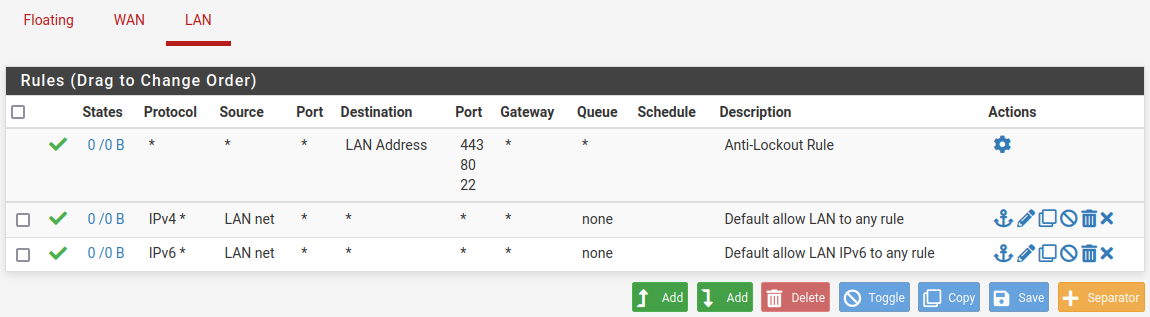
Step 4: Click the Add button to create a new rule. The Add button on the left with the up arrow will create the rule at the top of the list, while the Add button on the right with the down arrow will create a rule at the bottom of the list.
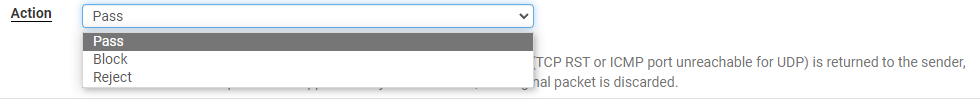
Step 5: Select an action to take when the rule is matched (pass, block, reject).
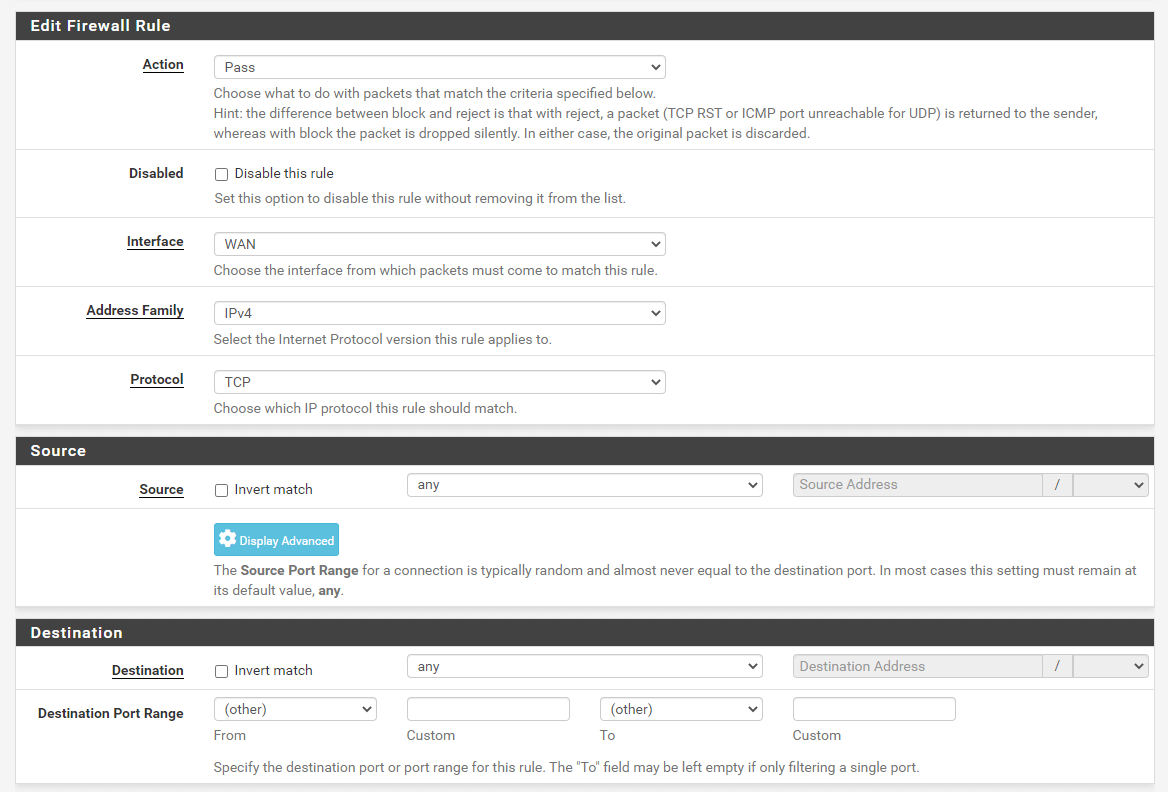
Step 6: Select the appropriate interface, protocol, and source and destination information.
Step 7: Select the appropriate logging options.
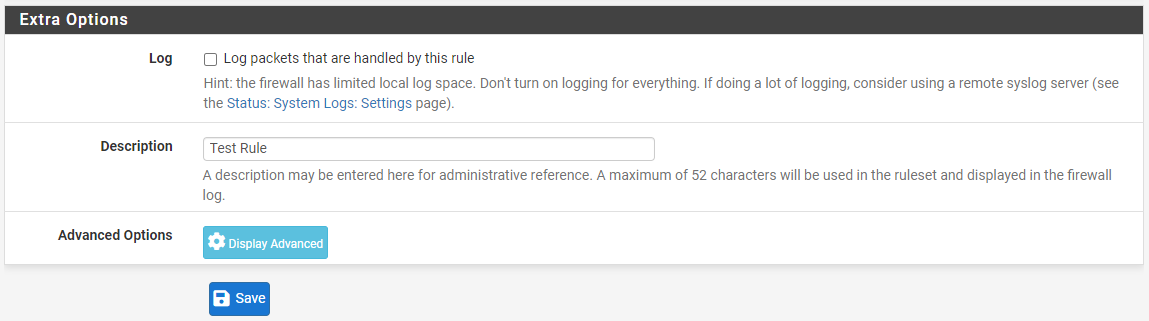
Step 8: Click Save. The new rule should now be visible in the list.
By understanding the different types of firewall rules and best practices for configuring them, you can ensure your enterprise networks are secure and functioning correctly. Consider the specific needs of your organization’s network and users, and ensure the rules are configured correctly and in line with industry standards.
When creating firewall rules, it’s also essential to consider their impact on overall network performance. Too many restrictive rules can cause latency issues, while overly permissive rules may create security vulnerabilities. Make sure you take care when configuring firewall rules and regularly review them to ensure they remain up to date.
Traditional firewalls are only the first step to a strong security posture for your network. A next-generation firewall will expand your protection across all layers.

Aminu Abdullahi is an experienced B2B technology and finance writer and award-winning public speaker. He is the co-author of the e-book, The Ultimate Creativity Playbook, and has written for various publications, including eWEEK, Enterprise Networking Planet, Tech Republic, eSecurity Planet, CIO Insight, Enterprise Storage Forum, IT Business Edge, Webopedia, Software Pundit, and Geekflare.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.