Windows Security
- Virus-Hunting Knoppix Gives Windows Machines the Once Over
- Identify and Mitigate Windows DNS Threats
- Securing a Windows Server? Time to Talk SCAT.
Stuck for a definition? Look it up at Webopedia:
Security management on a Windows machine can be a pain. Even in a simple environment with only a couple of workstations running a small number of applications, just keeping up with the latest patches, vulnerabilities, and best practices can eat a healthy portion of the sys admin’s time. Now what if you have 50 workstations? Or 100? Patch Tuesday starts feeling like the end of the world as you know it.
The Microsoft Baseline Security Analyzer (MBSA) can help. With MBSA, you can scan an entire subnet of workstations for missing security updates and common vulnerabilities from the comfort of your desk. After scanning, MBSA gives you not only a report of the issues found on each machine, but also step-by-step instructions for fixing them.
MBSA isn’t included with any Microsoft product out of the box, but you can download it for free at http://www.microsoft.com/technet/security/tools/mbsa2/default.mspx. After you install it, you can immediately begin scanning workstations and servers on your network through either the very simple GUI or via the command-line (Mbsacli.exe).
Whether you’re scanning a single computer or all the machines on the network, the available options are identical. For instance, you can choose to check for Windows, SQL, and/or IIS administrative vulnerabilities, weak passwords, and security updates. MBSA requires a current version of the Windows Update Agent and Windows Installer on each scanned machine, but MBSA can install or update both of those if you choose.
If you use Windows Server Update Services (WSUS) for patch management, you need to decide whether you want MBSA to use your managed WSUS server to check for updates or if it should use Microsoft Update. If you choose a local WSUS server, MBSA’s reports will only reflect missing updates that you’ve specifically approved in WSUS and will ignore other missing updates. If a scanned machine doesn’t isn’t assigned to a specific managed server, the scan will fail.
Ready, Set, Scan
Kicking off a scan from the GUI is simple. To scan a specific computer, just click the “Pick a computer to scan” link from the main menu, type in the name or IP address, select the aforementioned scanning options, and click “Start scan.” The scan will begin immediately, but the length of time required will depend on which options you selected and the installed software.
Scanning a group of computers is just as simple. Just click “Pick multiple computers to scan” from the main menu instead, then enter either the domain name of the target workstations or the IP address range. Choose the appropriate options, click “Start scan,” and you’re set.
As mentioned, command-line junkies have a separate tool available. Mbsacli.exe is installed in C:Program FilesMicrosoft Baseline Security Analyzer 2 by default and gives an administrator more granular control over the scanning process. For instance, using the /nd switch, an admin can tell MBSA not to contact any Microsoft Websites during the scanning process, simulating an offline scan. Use mbsacli.exe /? to see a full list of available parameters, or check out http://msdn2.microsoft.com/en-us/library/aa302360.aspx for a partial list of switches.
Keep a couple of things in mind before you start scanning. First, the account used to perform the scans needs to have administrative access to both the scanning workstation and the machines on the business end of those scans. If you’re using the GUI, you might need to open it using the Run As command to choose an appropriate account. With the command-line tool, you can use the /u and /p switches to specify the username and password for an administrative account.
Second, the current version of MBSA as of this writing (2.0.1) does not support vulnerability scans of Windows Vista. While you have the ability to install the software and kick off the scans on Vista (though not specifically mentioned in the license agreement), Microsoft says you’ll have to wait for the next version for full support. Version 2.1 is in beta now and scheduled for a third quarter release. For more information, check out http://support.microsoft.com/kb/931943/.
Make Sense of the Results
MBSA’s reports are the bread and butter of the application. After a scan is complete, you can view the resulting reports by clicking “Pick a security report to view” in the GUI. The tool maintains a list of all the scans performed by your machine, and you can sort them by date, name, IP address, and assessment. Click on the Computer Name to view the specific report.
The reports will vary depending on the options selected and the software installed, but the general layout is the same for all. At the top of the report, you’ll see the name and IP address of the scanned machine, the time and date of the scan, the MBSA version used to perform the scan, the security update catalog used, and the general scan assessment.
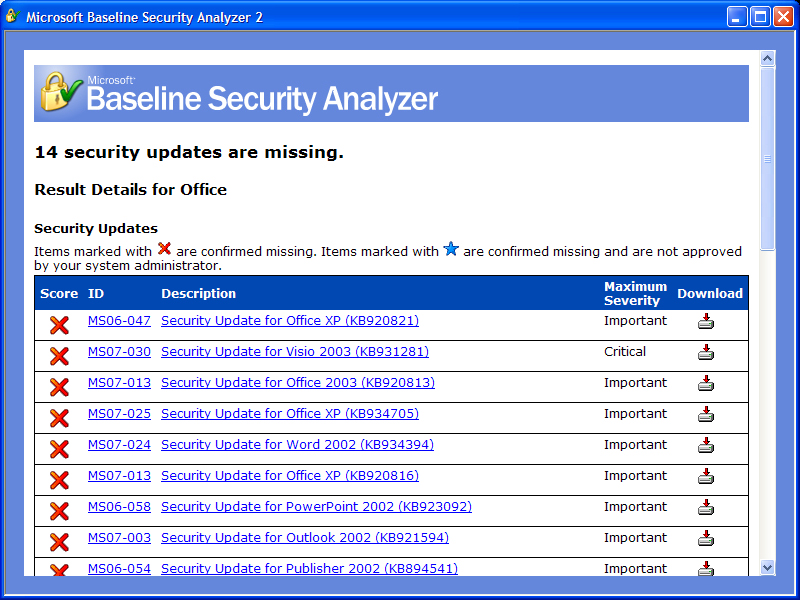
Below the general information, MBSA gives a list of the various scan results. The Security Update Scan Results allow an administrator to see a list of missing updates for various installed Microsoft products. It includes general information on what scanned items and information on how to remediate any issues found.
Figure 2. MBSA Shows Missing UpdatesThe “Result details” link is easily the most valuable part of the MBSA reports. Using that link, you’ll see a specific list of missing updates, along links to information on the updates. Better yet, you can also download the required patches directly from this window. If there are many missing patches, however, you might be better off using Windows Update to download the patches en masse rather than using these one-off links to install them piecemeal.
After the Security Update section, MBSA lists various other Administrative Vulnerabilities found on the scanned machines. Those might include lists of accounts with weak passwords, lists of shares, or other vulnerabilities common to specific applications. As with the Security Updates, MBSA provides specific information for each vulnerability through a link on the report, so administrators can start correcting those problems immediately. Given the number of patches and vulnerabilities affecting every operating system and application on the planet, administrators owe it to themselves to make their lives easier by making regular MBSA scans a core part of their security strategy.