Threats aimed at corporate entities and enterprises are rapidly evolving, with targeted attacks becoming the norm and Advanced Persistent Threats (APTs) the bane of many an enterprise security administrator. What’s more, APTs have been further fueled by the rise of Advanced Evasion Techniques (AETs), which help APTs bypass firewalls, security appliances, and endpoint security products.
McAfee, a wholly owned subsidiary of Intel, aims to quell today’s security concerns by combining a plethora of security technologies (IPS, IDS, AV, NGFW, etc) with Advanced Evasion Protection, which the company claims can stop attacks delivered by obfuscation techniques, securing enterprise networks against intrusions, APTs and much more.
While that may be an almost unbelievable claim, McAfee’s NGFW software, now in version 5.7, backs it up.
Hands on with McAfee’s Next Generation Firewall (Versions 5.6 and 5.7)
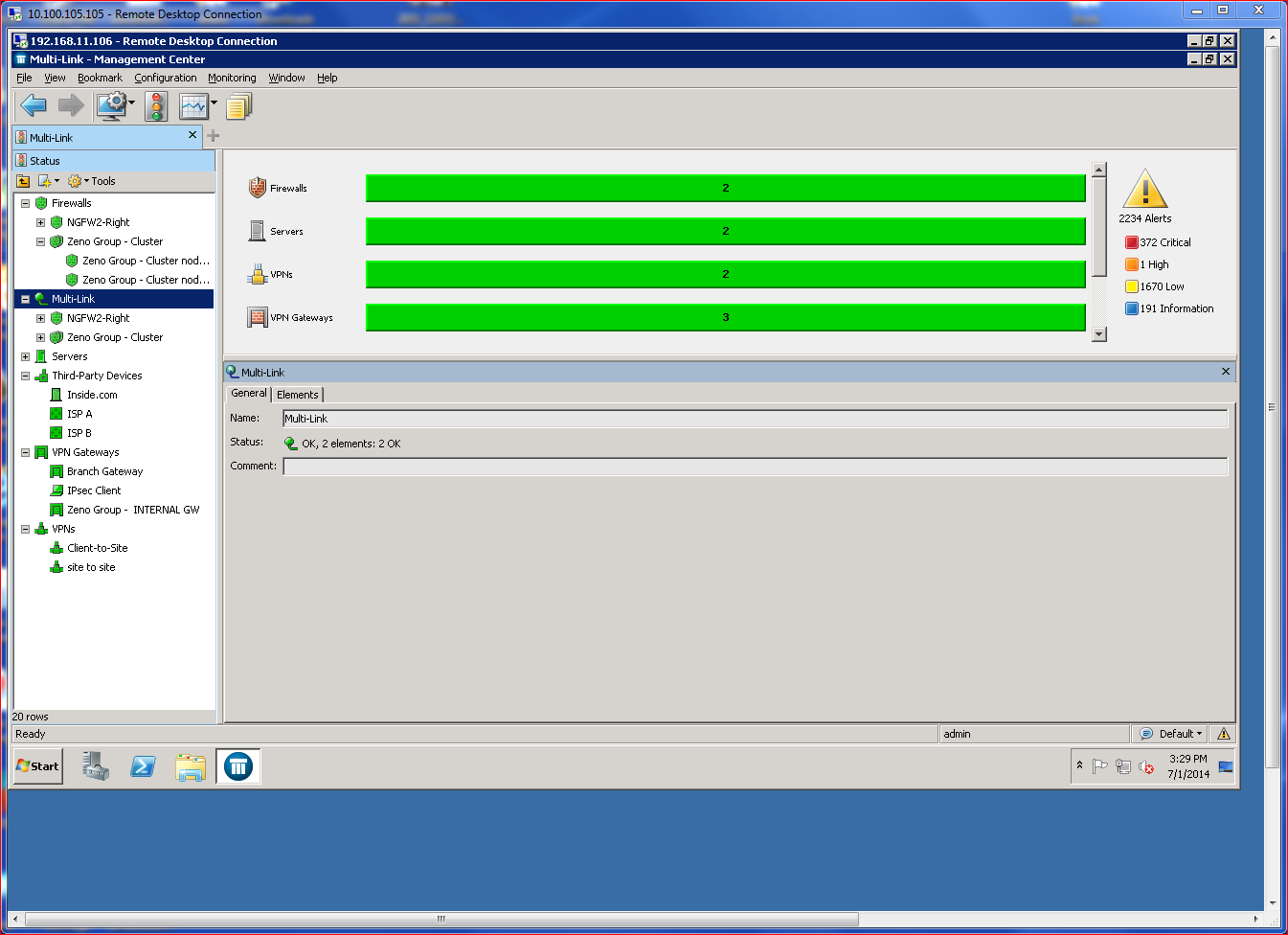
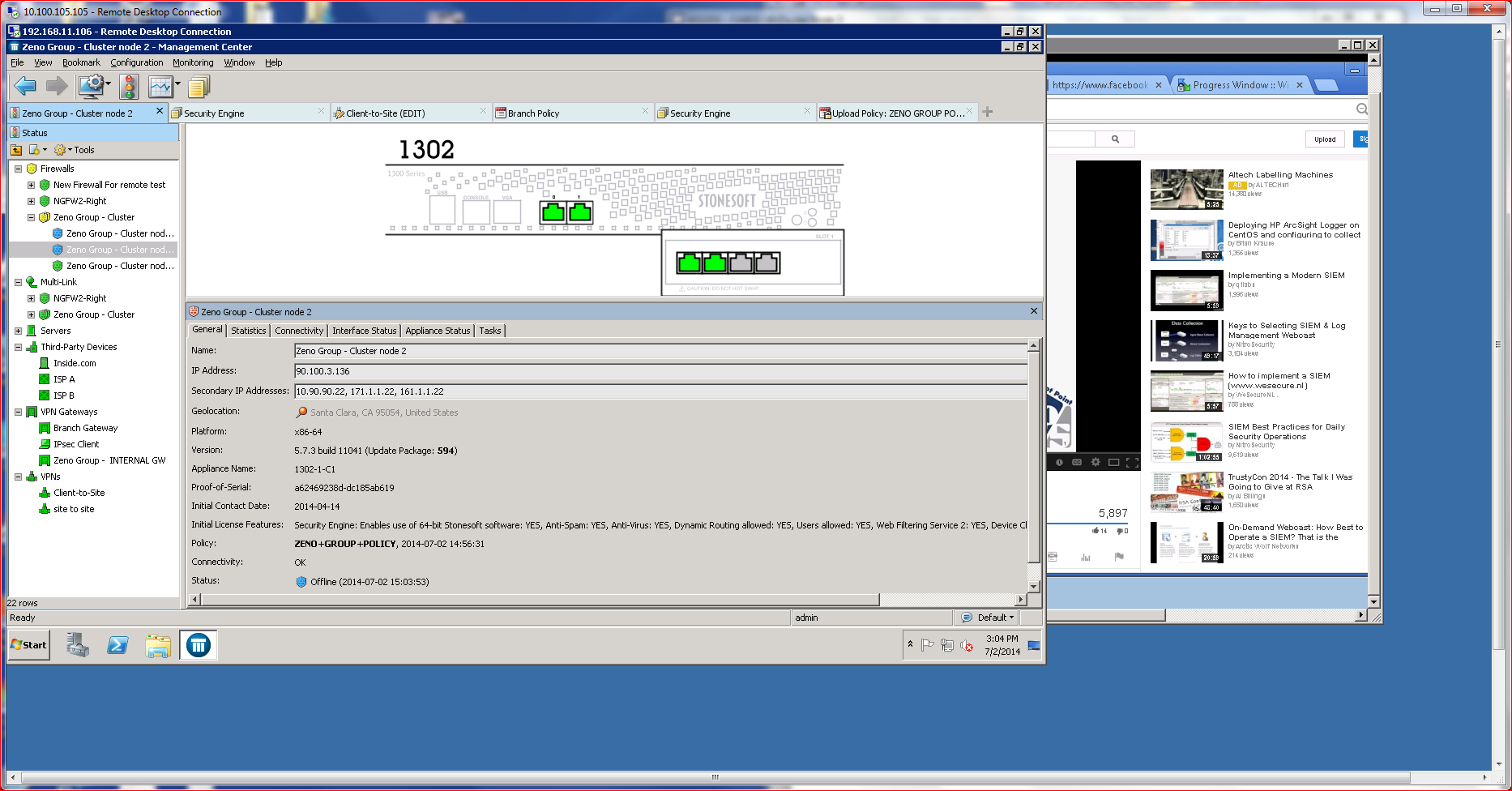
I put McAfee’s NGFW software through its paces at the company’s Santa Clara, CA, headquarters using a test lab that consisted of multiple distributed Next Generation Firewalls controlled by the company’s Security Management Center (SMC). SMC works as the conductor for centralizing control and policy distribution among the whole family of McAfee NGFWs regardless of physical locations, giving a holistic view of all security in a distributed network.
One of the first tests I performed exercised the SMC’s ability to remotely add a new firewall to the test environment. The process highlighted the ease of use and robustness of SMC.
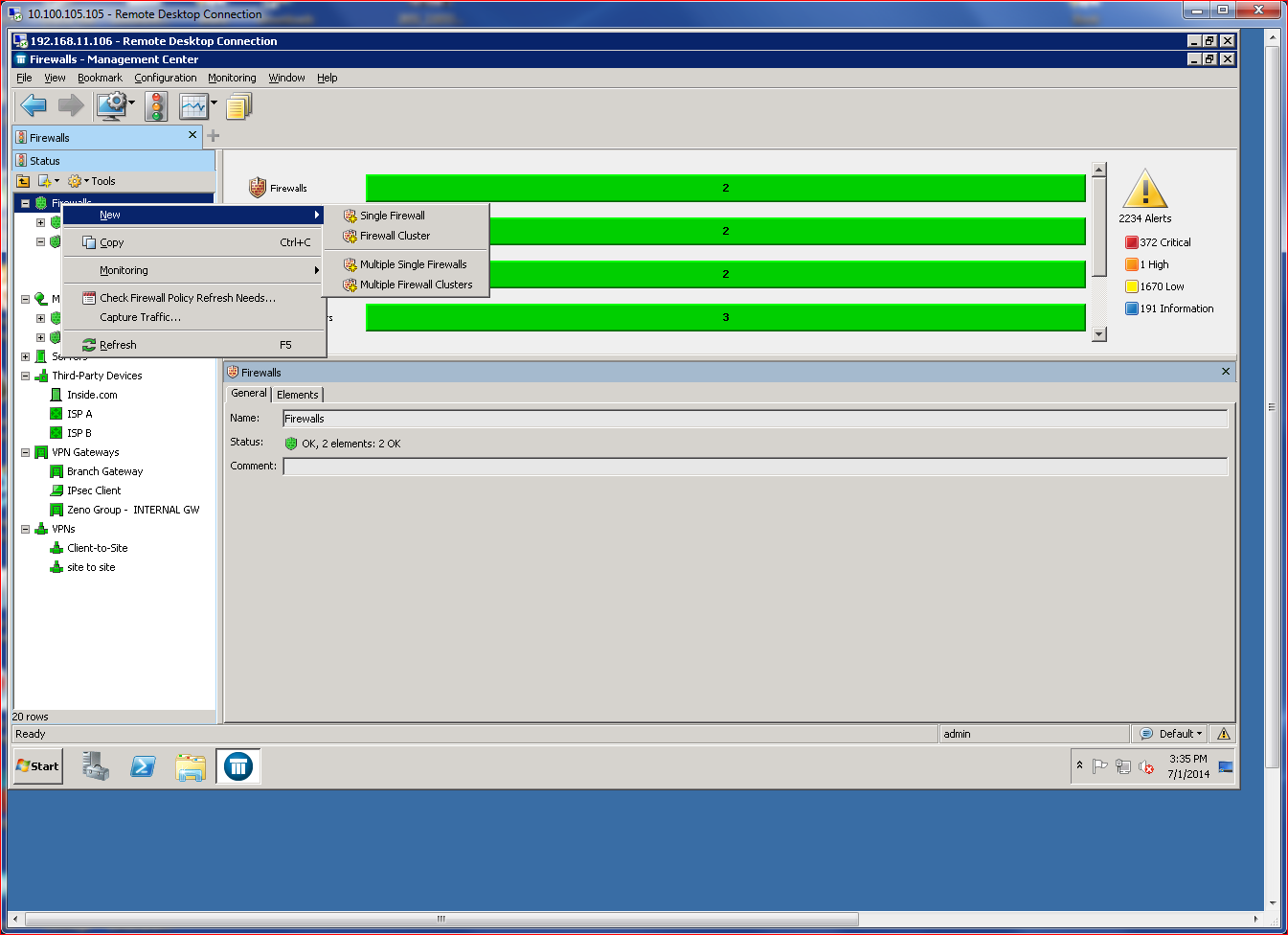
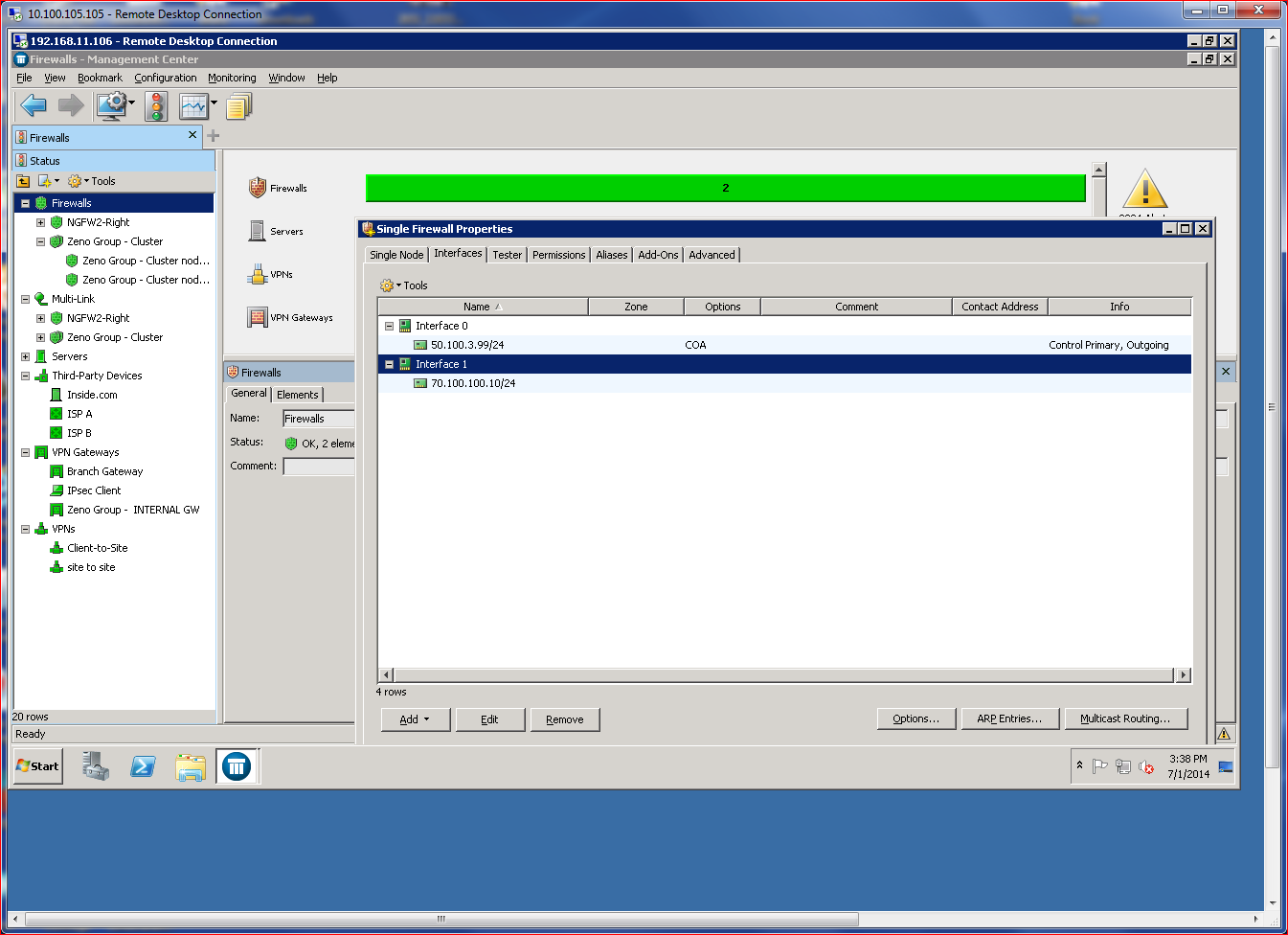
Adding a firewall can be done using three different methods, two of which are very simple (cloud configuration delivery or USB-based configuration file) and one that requires a bit more hands-on interaction. I chose the latter method, launching an “add firewall” wizard from the SMC management console. The manual configuration required that I input common network criteria, such as port definitions and IP address assignments.
The end result was a configuration file and single-use configuration password. After that process, I had to manually use the new firewall’s CLI to input some more basic information, such as IP information, and provide the temporary password to allow the firewall to connect with the SMC management server. The process was not at all difficult, just time-consuming. For busy administrators, I recommend using either the USB method or cloud-based configuration file delivery.
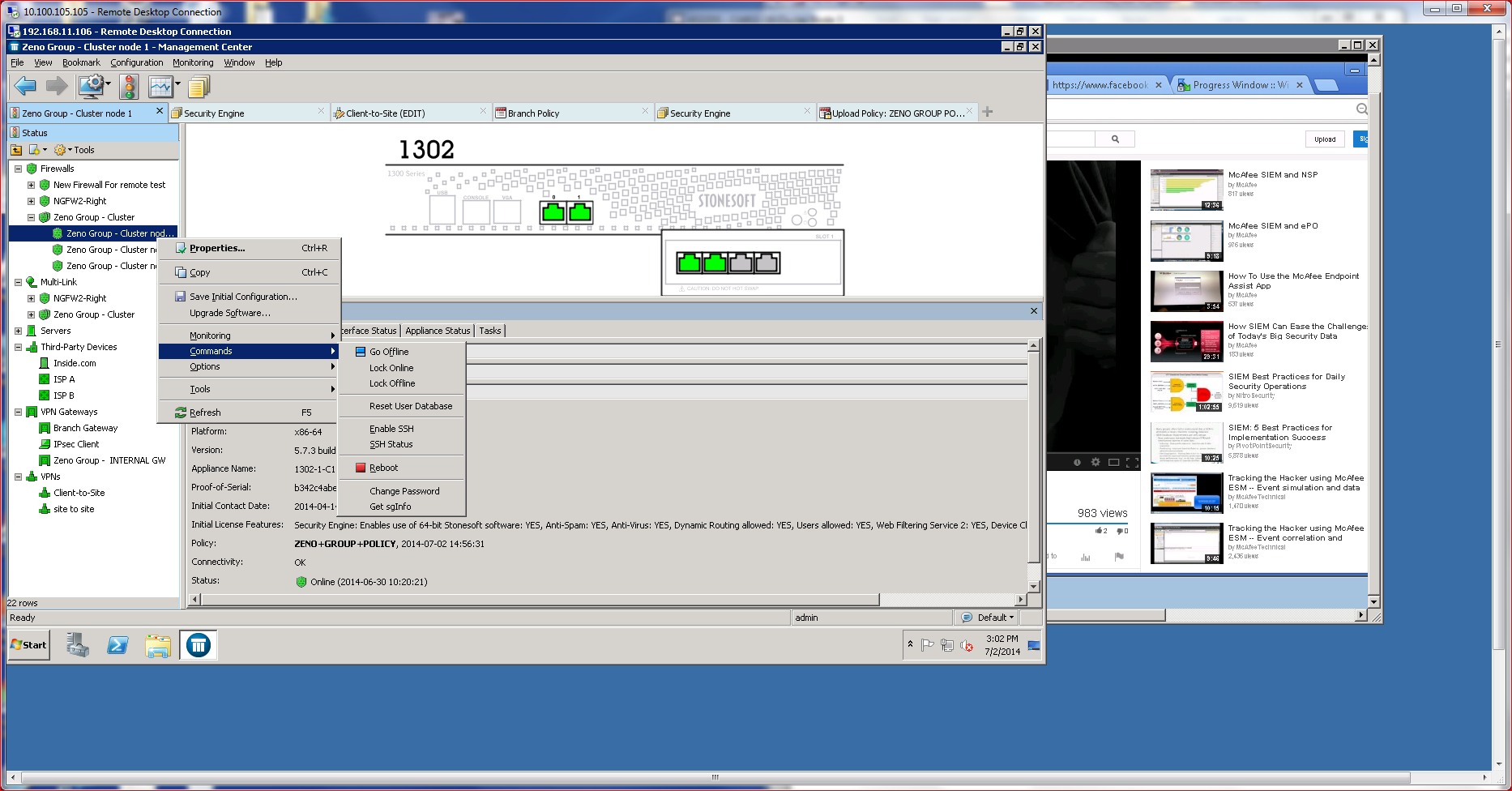
Once the firewall rebooted, SMC recognized it and allowed me to push down the initial policy, which brought the firewall online. This was the last time I had to use the CLI. All subsequent management tasks occur in the SMC GUI.
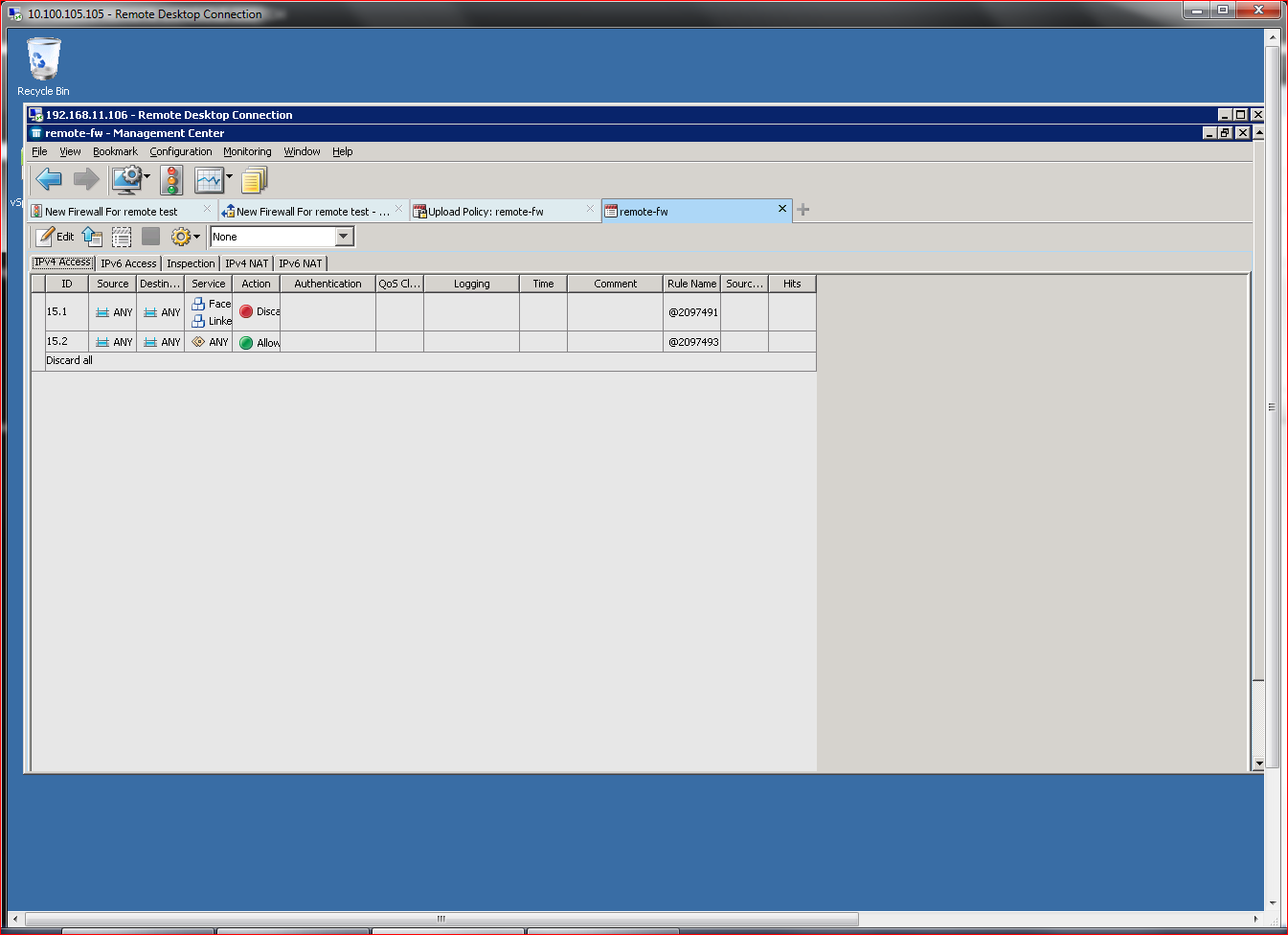
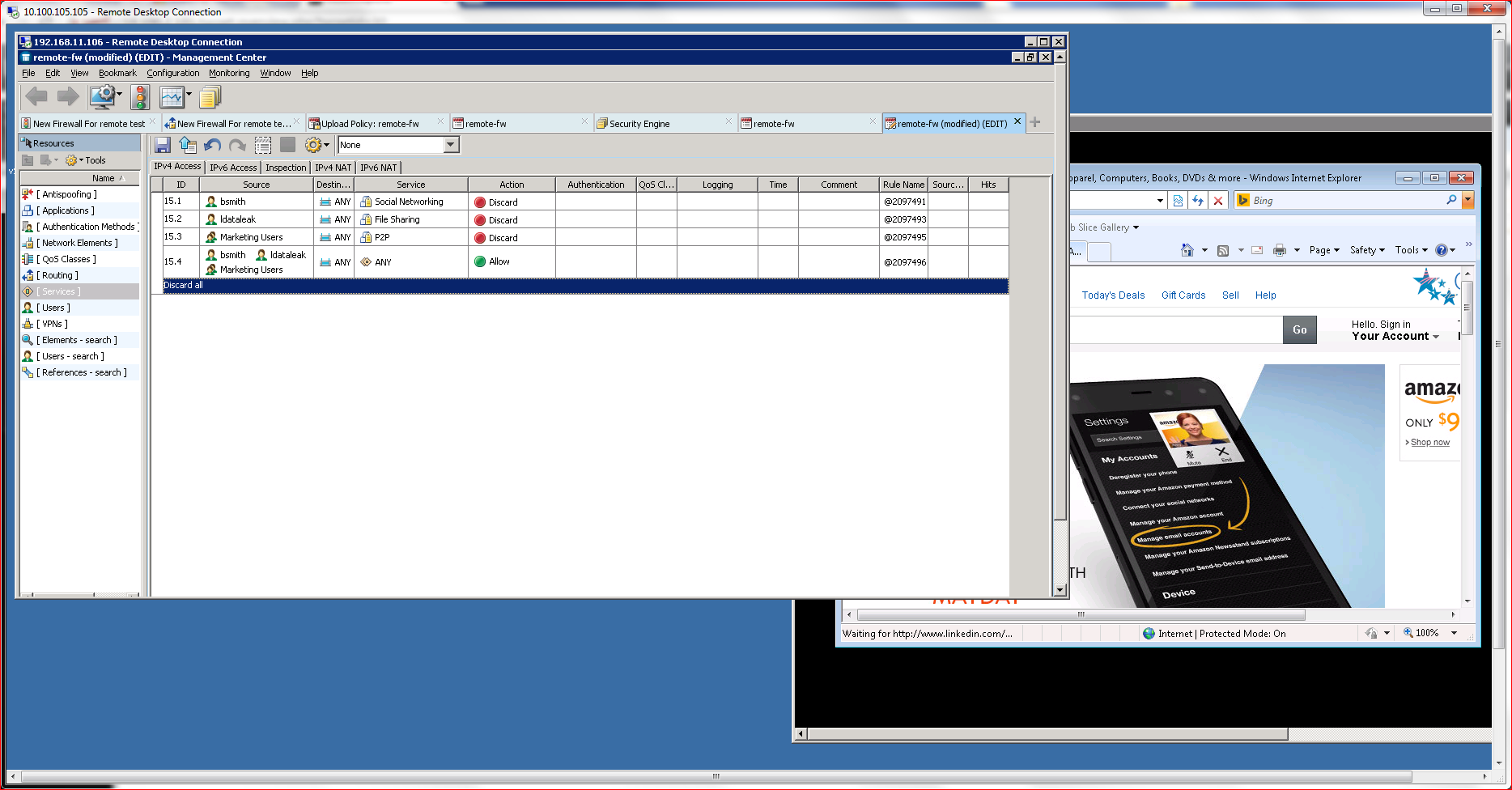
After initial configuration, the most important tasks involve defining policies, which control most everything in the firewall, including its usage and who/what can connect. Policies are the key differentiator between “dumb firewalls,” which rely on canned rules, and NGFWs, which offer granular control of individual connectivity elements.
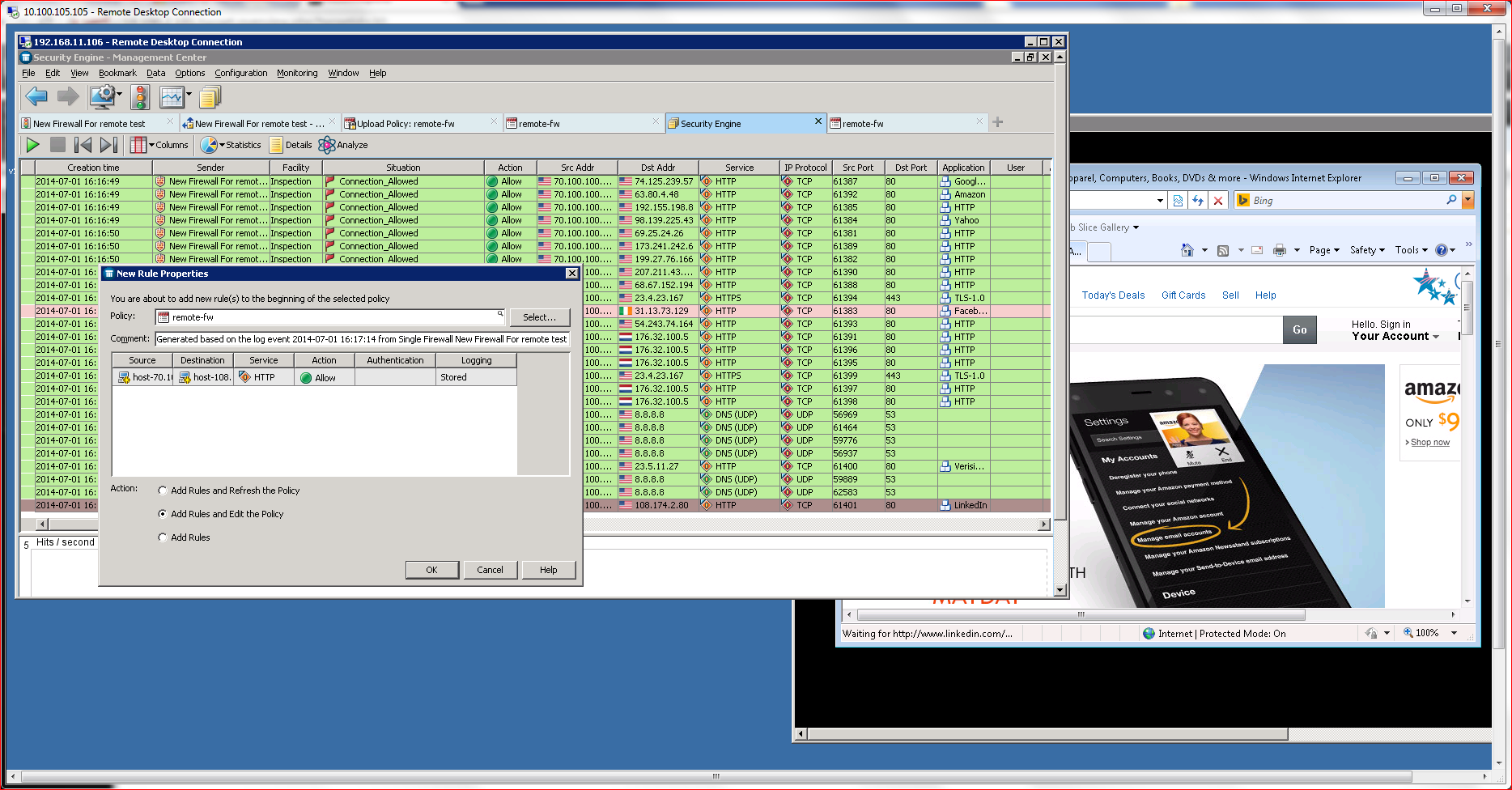
Policies are defined using the SMC management console, which offers a policy definition subsection. Policy definition is simple, and the product incorporates a validation engine to verify that policies make logical sense before they are deployed to the subject NGFW. The definition process also offers several pulldown menus and extensive help, enabling even novice administrators to quickly define standard policies for most use cases.
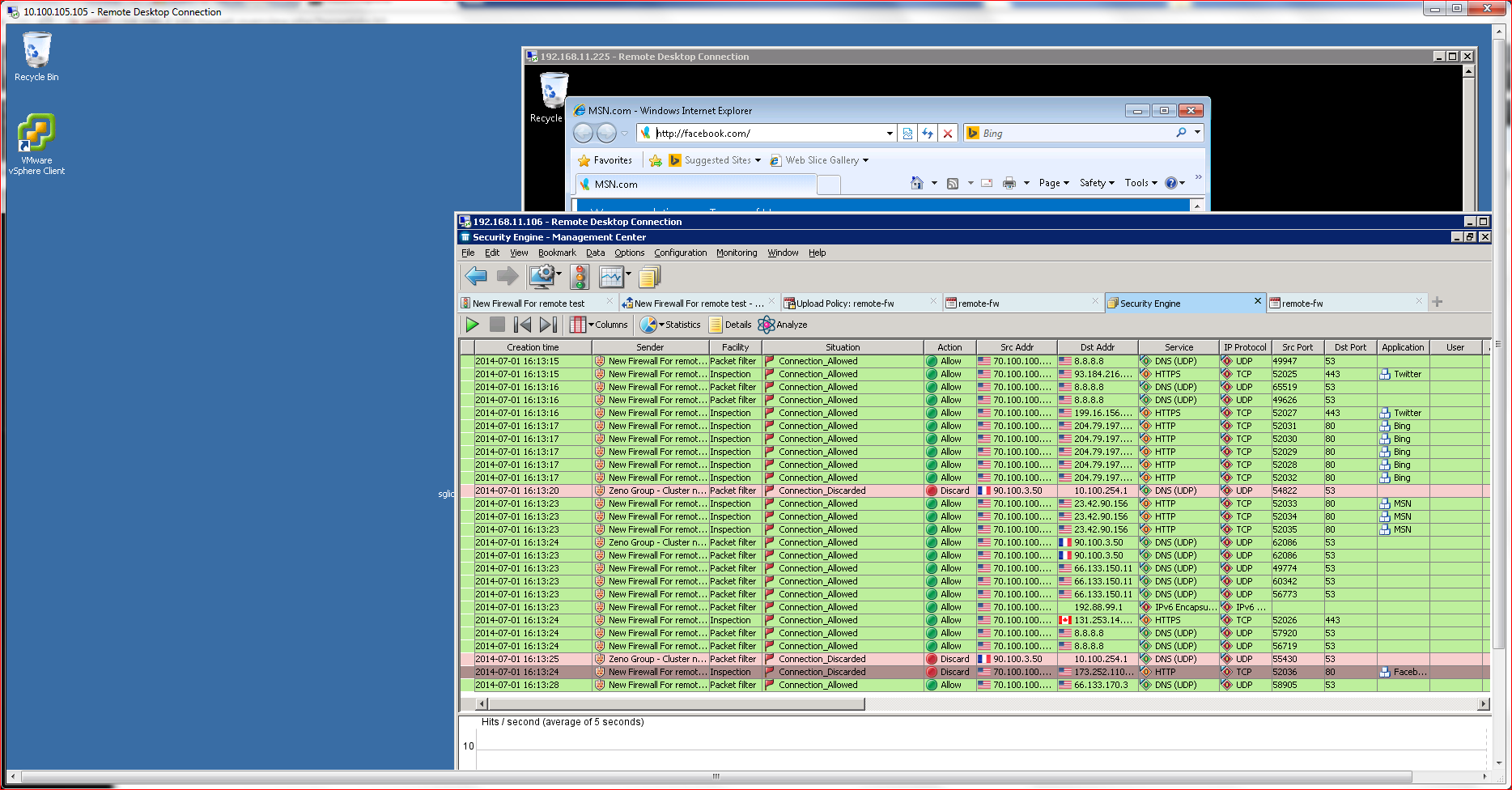
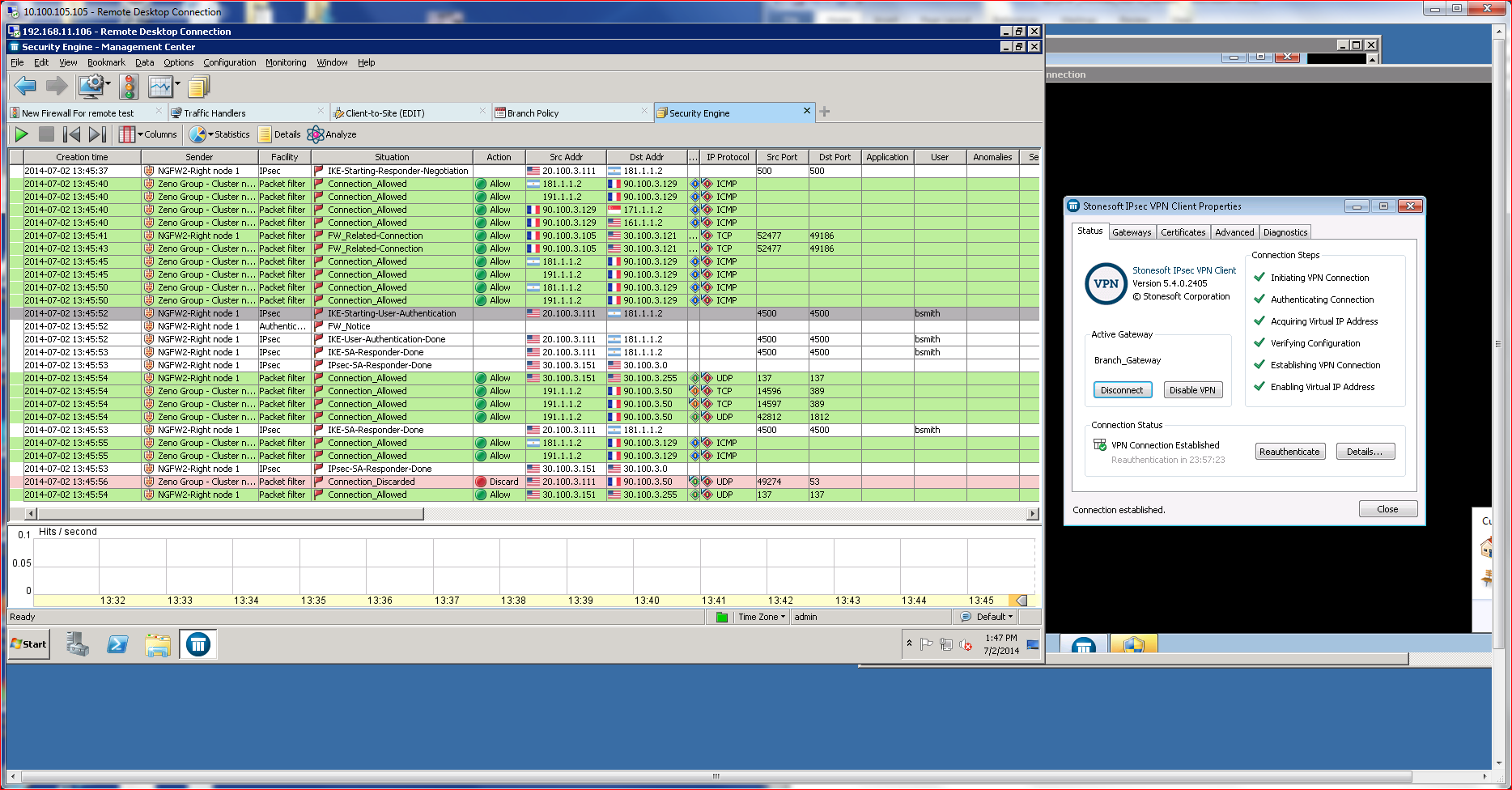
I was able to define a policy that blocked social media access with just a few mouse clicks and immediately deploy it to a target NGFW. Once the policy is deployed, an active logging system relays policy enforcement actions in real time, exposing the policy’s impact on users. One feature I found particularly useful here was the ability to right click on a log message and then redefine a policy. For example, when I saw that a user’s Facebook access was blocked, I was able to click on the event and add an exception to the policy to allow access.
Policies are fully granular and can be applied down to the individual user level, as well across a complete enterprise. Policies can also be nested, allowing administers to create site polices that can further be controlled using sub-policies, user-based policies, group-based definitions, and most any other authentication scheme.
McAfee’s NGFW family of products offers a full range of security capabilities, just like many of its competitors. These capabilities include intrusion detection and prevention, application-level security, deep packet inspection, unified management, policy creation and control, VPN support, and anti-malware technologies.
What differentiates McAfee’s NGFWs from the competition are three core capabilities that the company has mastered:AET blocking, Multi-Link deployment, and High Availability. We’ll discuss those on Page 2.
How the McAfee NGFW blocks AETs
Arguably one of the most critical capabilities of a NGFW is its ability to prevent malicious code from traversing the network. AETs have made that task especially challenging in recent years. AETs slip past traditional AV and anti-malware solutions by slicing and dicing malicious code to trick perimeter defenses. The code then reassembles at the endpoint. McAfee claims its Advanced Evasion Protection (AEP) feature prevents that from happening. My tests support that claim.
AEP works by combining raw processing power with multi-OSI layer analysis to fully reassemble payloads before allowing them to move onto an endpoint. McAfee accomplishes this by using horizontal packet assembly techniques to look at larger pieces of code. The vendor’s competitive advantage here comes down to that code examination. Competitors rely on ASIC-based processors, which use vertical segment analysis and therefore might miss the obfuscation techniques used for AETs.
To test the product’s AEP capabilities, I used an obfuscation tool known as Evader, to build an APT attack and attempt to pass it on to an endpoint using AETs. The McAfee NGFW effectively blocked every scenario I concocted.
McAfee NGFW Multi-Link technology
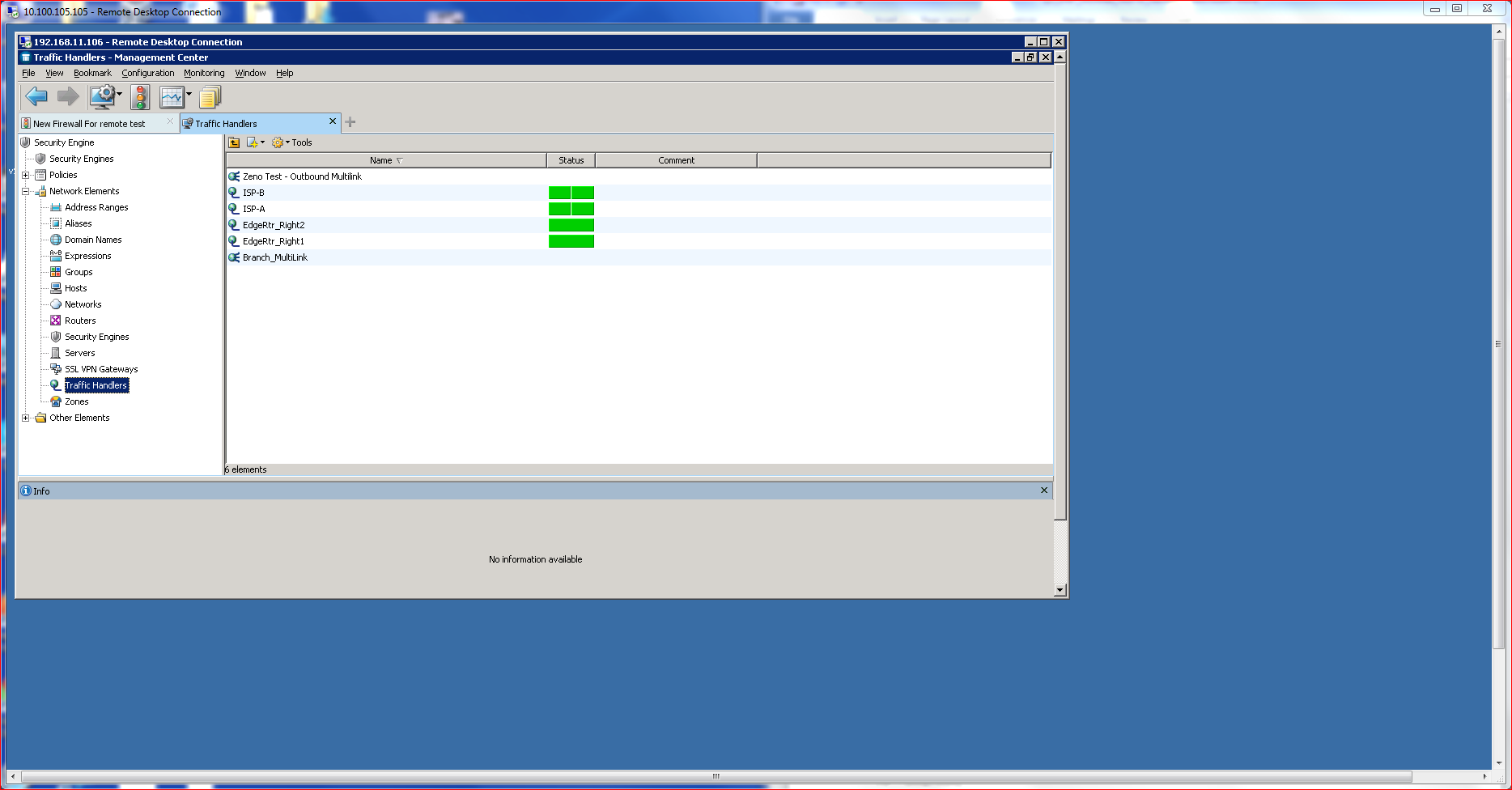
Some of the product’s other advanced capabilities leverage Multi-Link technology, which prevents single points of failure, handles load balancing, incorporates augmented VPN technologies, and supports slipstream product updates. Simply put, Multi-Link is the key McAfee High Availability (HA) solution. Larger, multi-site networks will benefit from the stronger links provided by Multi-Link.
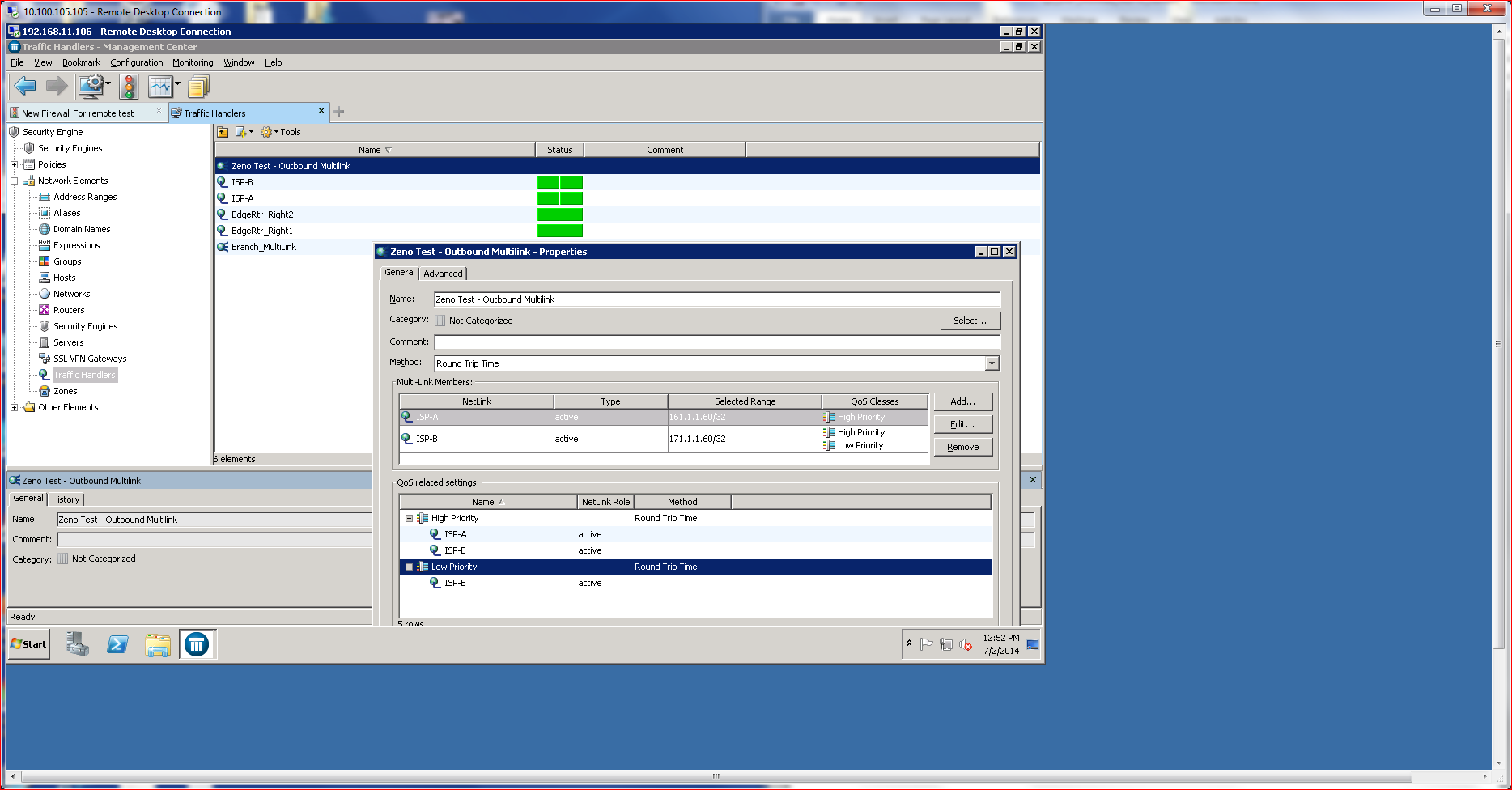
Deployed using the SMC, Multi-Link ties together multiple ISP connections that appear as a singular IP path to available resources. All I needed to know was some basic IP and ISP (Net Link) information to quickly make a Multi-Link Connection live. Each Net Link supports QOS/Prioritization, so a link can be assigned as high priority or low priority, which drives the HA algorithms. Choices include active/active or active/standby, which controls traffic routing. Load balancing can use round-trip time for determining the route, or a ratio calculation that assigns traffic based upon available bandwidth percentages. Optionally, load balancing can be disabled, making HA the priority.
Augmented VPNs on McAfee NGFWs
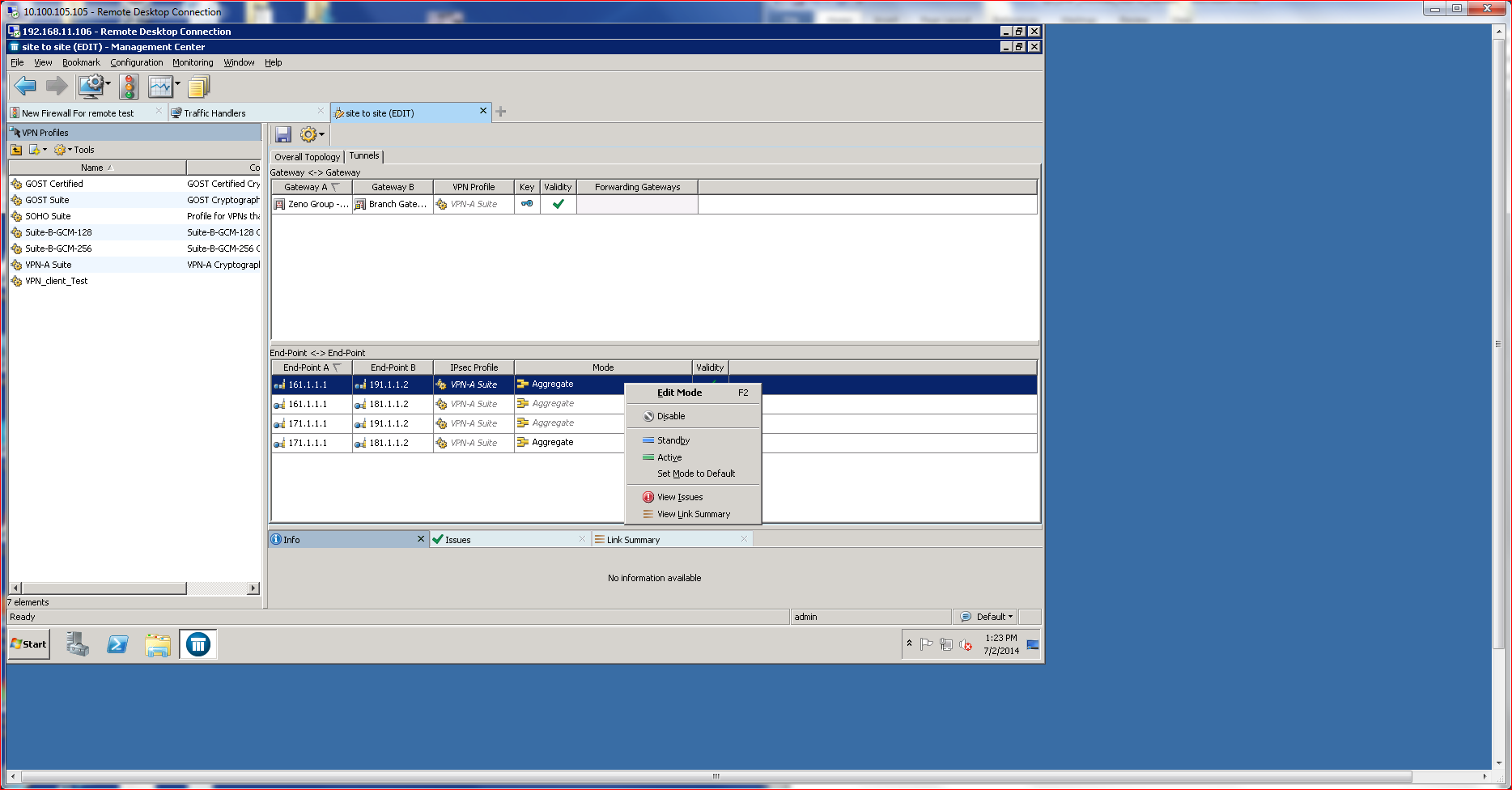
McAfee’s Multi-Link technology also empowers the capabilities of VPN connections, creating something referred to as an Augmented VPN (aVPN), which load balances VPN traffic across multiple connections. Thanks to the drag-and-drop capabilities of SMC, creating an augmented VPN can take under a minute. aVPN is built into the solution and offers additional security in the form of integrated IPSec support, which fortifies encryption.
The nifty thing about an augmented VPN is that VPN traffic can be aggregated across multiple Net Links (using Multi-Link), creating a high-speed, low-cost VPN tunnel for either endpoints or site-to-site communications that incorporates HA without any extra effort. Testing the augmented VPN showed that interrupting any Net Link did not disrupt the VPN traffic. The NGFW simply continued to aggregate the traffic over the available Net Links without any noticeable impact on the endpoint transmitting information.
McAfee provides their own IPSec client VPN software, which fully integrates with the VPN server capabilities and keeps logs filled with pertinent information for auditing, troubleshooting and general reporting. The logging also provides ample proof of how well the augmentation and policy enforcement works.
McAfee NGFW scalability
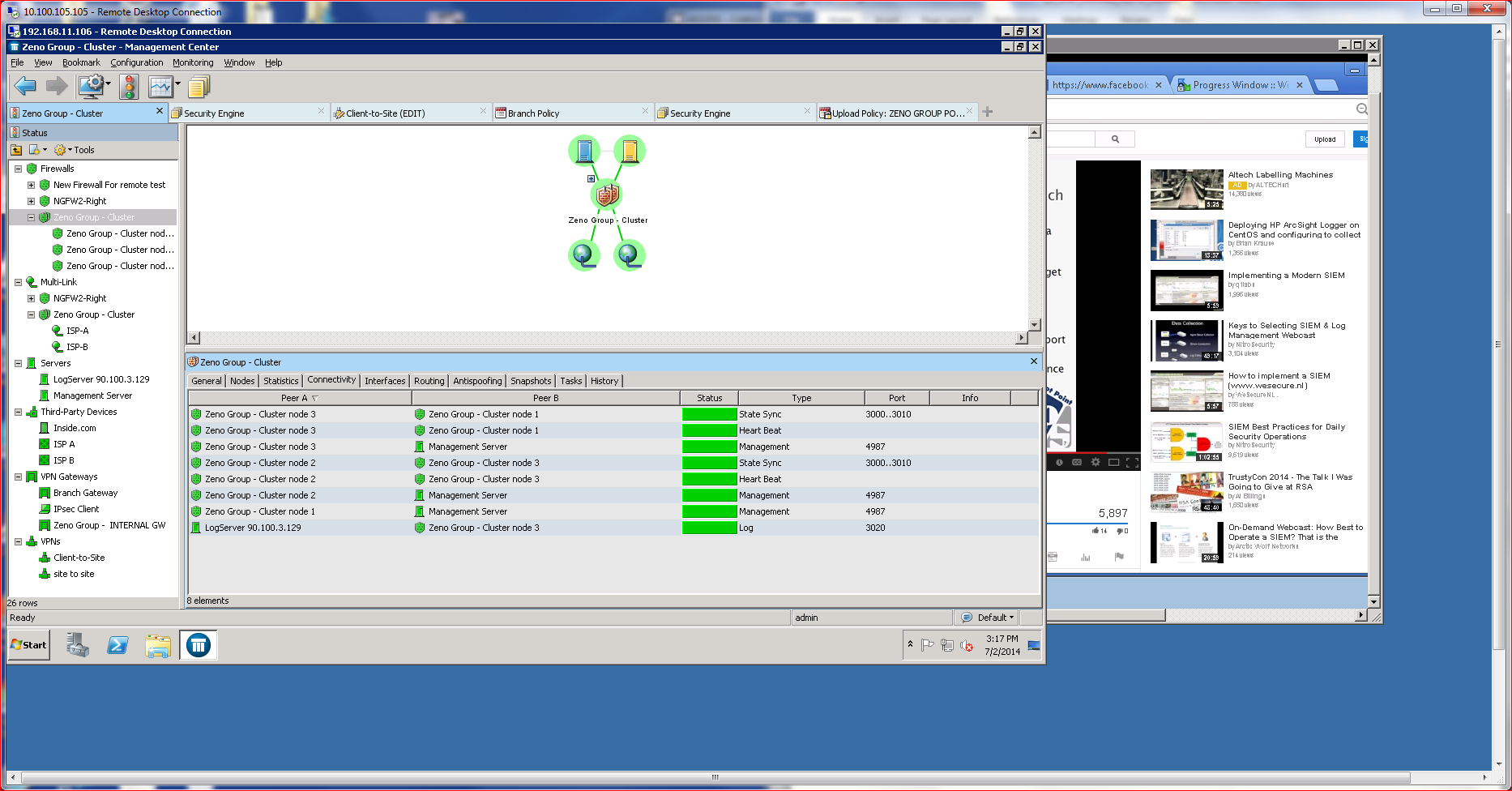
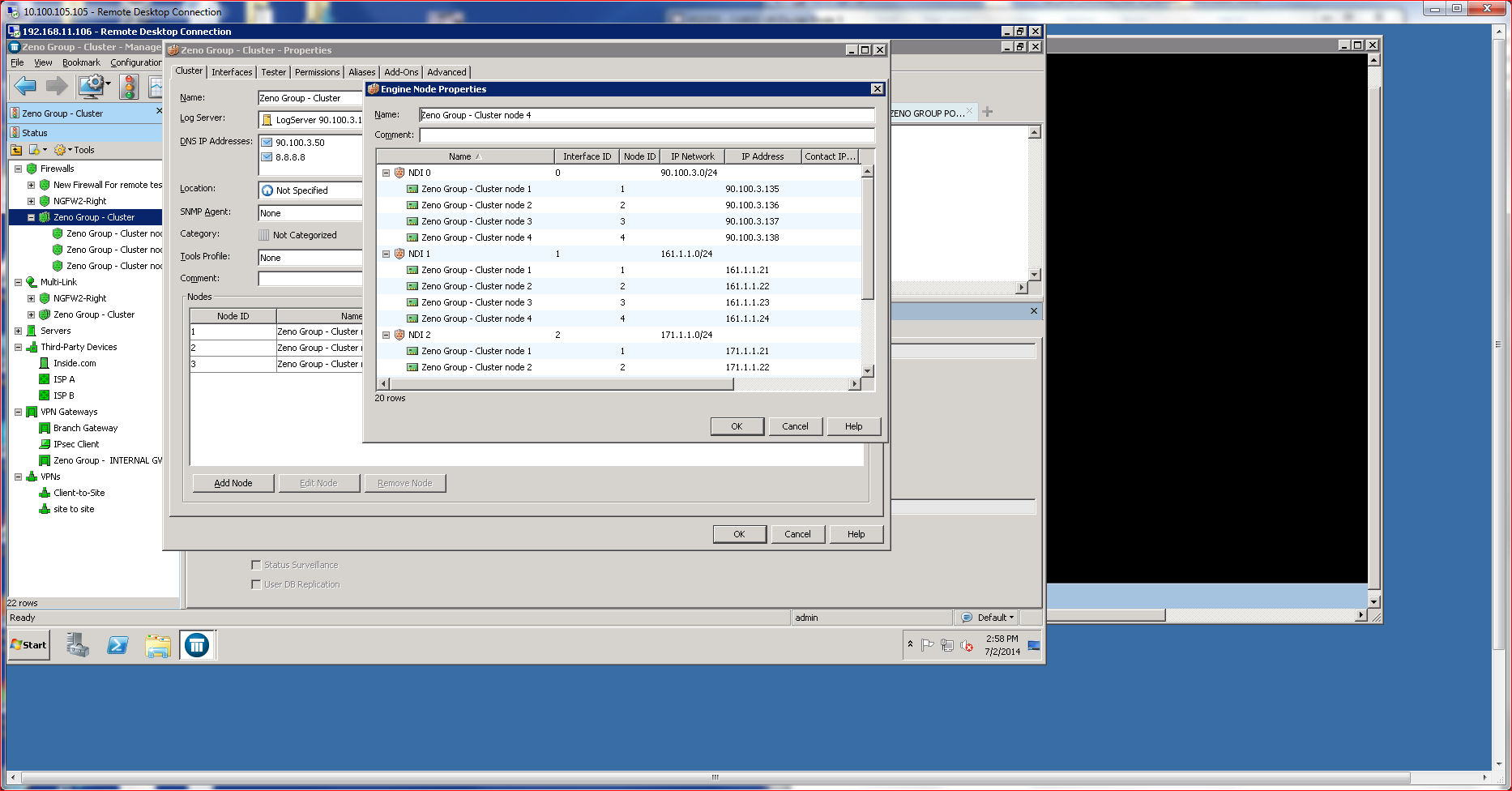
As enterprises grow, scale becomes an important consideration. Enterprises that grow faster than expected often find themselves in a conundrum when scale comes at a very high price. McAfee addresses scalability issues by incorporating a clustering capability that is both inexpensive and easy to deploy. What’s more, the clustering also offers significant throughput and speed advantages without introducing unnecessary complications.
One of the key elements of clustering is that adding, removing, reconfiguring and updating NGFWs can take place in real time and without interrupting operations. McAfee’s ability to cluster NGFWs that are running different versions of the core software (or even different models) is a key advantage, allowing updates to take place incrementally without service interruption. Failed updates are automatically rolled back and will never take other NGFWs down, making updates, patches and other changes a safe proposition.
Setting up a cluster required little manual configuration. Most of the process takes place using the SMC management console, which offers directed advice. Since I was not using USB or Cloud Configuration options, I did have to manually enter a configuration password using the CLI located on the NGFW that was being added to the cluster. NGFWs that are members of a cluster are usually referred to as “nodes.”
Operationally, I was able to shut down nodes, disrupting the cluster without apparent impact on the end client. To test that, I set up a client system to watch some Youtube videos and then manually disrupted nodes on the cluster. The HA/Load Balancing capabilities kicked in without a hitch. Traffic on the endpoint was not interrupted in any noticeable fashion.
What’s important to recognize about McAfee’s NGFW’s clustering capabilities—and McAfee’s NGFW overall—is that is very simple to deploy, easy to manage, and offers seamless operation, all key considerations for environments where availability is extremely important and endpoints should never experience disruption, such as retail, sales, financial and analytical environments.
Header photo courtesy of Shutterstock.