
Vector illustration of a lock icon embedded in circuit.
Curious about switching from a VPN to ZTNA? Gain clarity on these secure networking technologies as we break down their features and highlight the key differences.

As remote work continues to solidify its presence in our modern-day business environment, organizations are confronted with the critical task of providing secure access to internal network resources such as applications, databases, and servers for their remote workforce.
While traditional methods relied heavily on virtual private networks (VPNs) for remote connectivity, a growing trend towards zero trust network access (ZTNA) solutions is reshaping the landscape of secure network access. While both ZTNA and VPNs offer secure remote access, they differ in various aspects, making them suitable for different use cases.
So, which of these network access methods should you go for? This comparison piece will help you find out.
ZTNA provides individualized access to specific organizational resources, while VPNs grant remote users access to an entire network. To help you understand their differences, here is a quick comparison chart summarizing the key features.
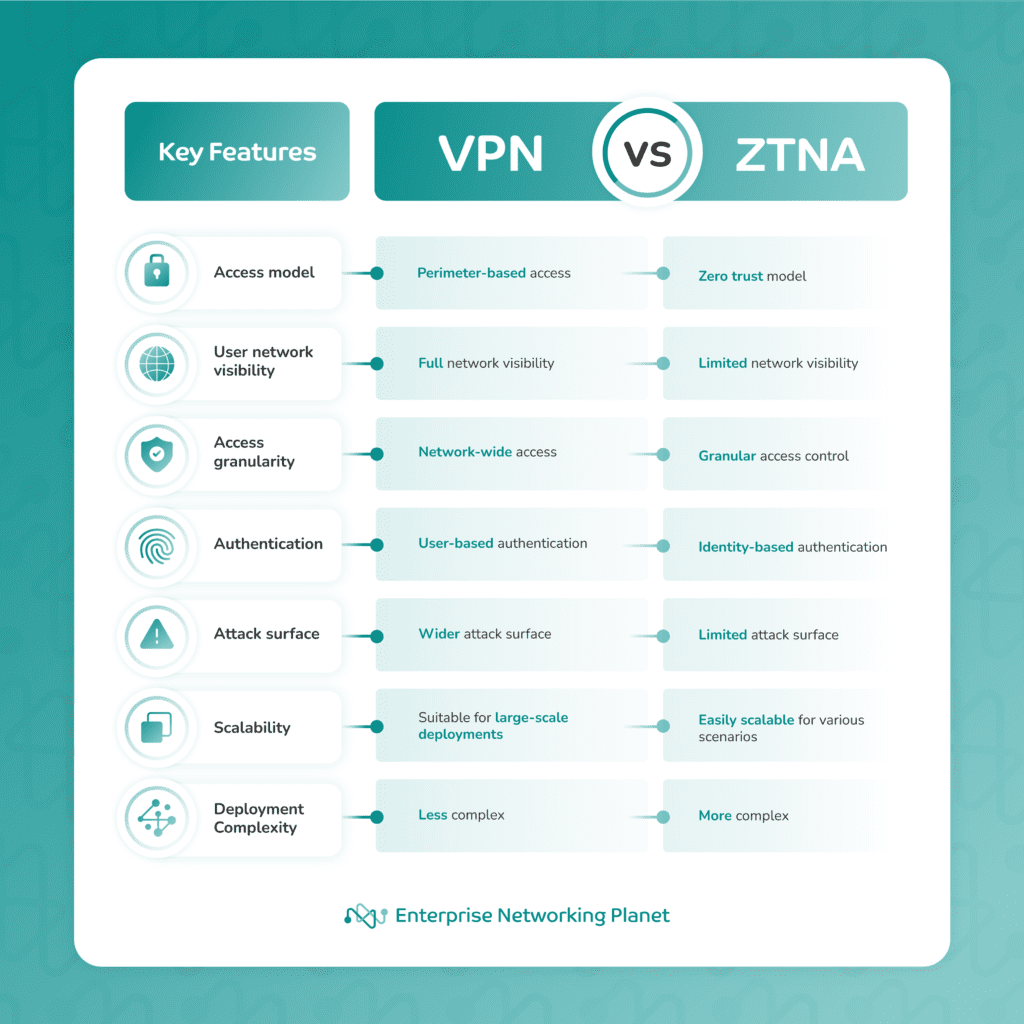
A VPN is a security solution that establishes a secure connection between the user’s device and the corporate network over the public internet. It creates an encrypted tunnel that protects data transmission from unauthorized access and interception.
VPNs have been widely used to provide versatile remote access, allowing employees to connect to their organization’s resources from anywhere, even outside the office premises.
ZTNA is a security framework that focuses on maintaining strict access controls based on user identity and other contextual factors. Instead of granting network-wide access, ZTNA follows the principle of “verify first, access later.”
ZTNA represents a more modern approach to network security and operates under a zero trust model, where user access is granted on a per-session and per-application basis. Instead of relying solely on network perimeter security like VPNs, ZTNA emphasizes identity-based authentication, granular access controls, and continuous monitoring.
This approach aims to minimize the attack surface and mitigate potential risks by only granting access to authorized users based on their identity, device health, and other parameters, such as time of access, device type, and network conditions.
Both ZTNA and VPNs offer great security options. The answer to which one you should go for at your organization depends on your specific budget, needs, and infrastructure.
While choosing either a VPN or ZTNA to protect your business’s network will be sufficient for many organizations, those looking to take the next step in network security may want to combine the two solutions.
Companies like Array Networks offer SSL VPNs based on zero trust principles, with granular controls so IT can secure access at the endpoint while providing specific, role-based permissions across the network. These sorts of dual solutions — also offered by ExpressVPN and Fortinet, among others — are ideal for businesses with enterprise-wide remote access needs, or for cloud service providers looking to offer the widest range of access options for their customers.
As business security needs continue to grow both more complex and stringent, expect to see more of these combined ZTNA VPN solutions appearing on the market.
Understanding the differences between ZTNA and VPNs is crucial before making any decisions about switching.
While VPNs have been around for many years, ZTNA represents a modern security approach under the zero trust model. ZTNA’s emphasis on identity-based authentication, granular access controls, and limited network visibility can significantly enhance security, minimize the attack surface, and better protect against evolving cyber threats.
Although both solutions have their merits, ZTNA stands out for organizations that prioritize robust security and have a lot of sensitive data to deal with. On the other hand, a VPN is ideal for organizations with less sensitive data and lower security risks, as well as organizations that want to provide full network access to their remote users.
Whichever solution you choose to go with, we’ve got you covered: read our guide to the best VPN services and the best ZTNA solutions available today.

Franklin Okeke is a contributing writer to Enterprise Networking Planet, as well as an author and freelance content writer with over 5 years of experience covering cybersecurity, artificial intelligence, and emerging technologies. In addition to pursuing a Master's degree in Cybersecurity & Human Factors from Bournemouth University, Franklin is an entrepreneur with a passion for startups, innovation, and product development. His writing also appears regularly in TechRepublic, ServerWatch, and other leading technology publications.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.