
Image: Skórzewiak/Adobe Stock
Encrypting your DNS is an essential part of cybersecurity. Discover what it is, why it matters, and how to check and adjust your own DNS settings.

DNS is the abbreviation for the “Domain Name System” and is essentially the phonebook system of the internet. It translates domain names such as “xyz.com” — human-readable queries that we type into browsers — into numerical IP addresses such as 154.6.147.47 (IPv4) or 2001:0db8:85a3:0000:0000:8a2e:0370:7334 (IPv6). The system is what allows internet users to access any of the billions of web pages daily — and DNS encryption ensures that any data they exchange remains private and secure.
This article will explain how encryption works, its benefits, and how to know if DNS encryption is configured on your browser and computing devices.
In the nascent days of the internet when it was referred to as Advanced Research Projects Agency Network (ARPANET), address translation was achieved via a simple text file known as HOSTS.TXT. However, with the rapid growth of the internet, it quickly became apparent to researchers that the addressing system was finite. This scenario led to the birth of the modern DNS in 1983.
Initially, DNS was not built with network security in mind. And there is good reason for this — after all, there was no e-commerce, online banking, or pervasive data theft like we have today. Its original design was simply meant to address the problem of address scalability.
However, upon the realization of the internet’s potential and the dangers an insecure DNS posed, computer scientists scrambled to find a solution. The result was multiple standards and practices, the DNSSEC (Domain Name System Security Extensions), being retrofitted into the system to make it more secure.
Almost four decades after the invention of the DNS, two DNS encryption protocols were developed: DNS over TLS (DoT) and DNS over HTTPS (DoH).
DNS encryption works by converting plain text DNS information into an encrypted version that only two parties engaged in the exchange of data — the DNS client (i.e., your browser or network devices) and the DNS resolver — can decipher.
DoT is a security protocol created in 2016 to encrypt and protect DNS queries and responses using the Transport Layer Security (TLS) channel that secures HTTPS websites.
In this type of DNS encryption, the DNS resolver server authenticates itself to the client device through a certificate ensuring that no third party can impersonate the server. This authentication process guarantees the integrity and confidentiality of DNS traffic.
The main purpose of DoT is to enhance user privacy and security by preventing man-in-the-middle attacks, which could compromise or eavesdrop on DNS traffic. DoT operates over what is known as the user datagram protocol (UDP). It adds a layer of TLS encryption to secure DNS queries. The typical port for DoT is port 853.
While DoT provides security features, it’s important to note its potential limitations in jurisdictions with restricted freedom of speech. Enabling DoT encryption may inadvertently attract attention from authorities. Thus, it might not offer the intended protections against hostile or authoritarian regimes. Despite these considerations, supporters of the DoT protocol argue that it is better suited for addressing human rights concerns in challenging environments.
Introduced in 2018, DoH is another protocol designed to make DNS queries more secure. Unlike DoT, DoH utilizes port 443 for HTTPS connections. It allows DoH clients and resolvers to connect to a DoH server that hosts a query endpoint.
Similar to DoT, DoH also relies on TLS for encryption. However, since it operates over HTTPS it seamlessly integrates with existing web infrastructure. This makes it less noticeable and potentially harder to block or filter in restricted environments.
To understand the importance of DNS encryption, it can help to examine the top risks of unencrypted DNS. Some of the original security threats identified by the Internet Engineering Task Force include:
Other, more contemporary risks include:
The benefits of DNS encryption are numerous for enterprises, small and mid-sized organizations, and even individuals. These benefits extend from financial and identity protection to superior defense against a variety of cyberattacks.
According to a 2023 report by IDC, the average financial impact of DNS attacks has escalated to $1.1 million per incident. DNS encryption serves as a financial safeguard by reducing the risk of costly data breaches and unauthorized data access.
Radware’s threat advisories indicate a rise in DNS flood attacks, which aim to overwhelm DNS servers with high volumes of requests. DNS encryption adds a layer of security that makes it more challenging for attackers to manipulate or intercept DNS traffic, helping to protect against such sophisticated attacks.
DNS encryption ensures the integrity and confidentiality of DNS data. This is particularly crucial due to the emergence of advanced HTTP and DNS DDoS attacks employing techniques previously exclusive to nation-state actors. By encrypting DNS queries, organizations can be assured that they are interacting with the intended servers.
DNS spoofing and man-in-the-middle attacks are common techniques used in advanced DNS attacks, whereby the client is directed to a facsimile of the intended web page, where they then enter important data such as passwords or payment information. DNS encryption effectively mitigates the risks associated with these attacks by ensuring that DNS queries can’t be intercepted, read, and redirected by malicious actors.
As DNS attacks continue to evolve in complexity and scale, DNS encryption offers a proactive measure to secure DNS queries. It is not just an optional feature but a necessary component in a comprehensive cybersecurity strategy.
The reputational damage following a DNS attack can be devastating for enterprises. DNS encryption helps in maintaining the trust and credibility of an organization by ensuring the security and integrity of its DNS queries.
Most modern web browsers, like Chrome, Firefox and Edge have a feature that lets users customize their DNS encryption settings. Typically you can find these settings by going to the “Settings” menu and then selecting “Privacy and Security.” It is important to note that the exact steps might be slightly different depending on the specific browser you are using.
For operating systems such as Windows 10 and newer versions, macOS, and Ubuntu, it’s often possible to configure DNS encryption settings at the system level. This means you can secure your DNS queries beyond web browsing activities. To adjust these settings it’s best to refer to your operating system’s documentation or support resources for detailed instructions.
Both Android and iOS smartphones have built-in support for DNS encryption. You can usually access these settings through the network or privacy options on your device.
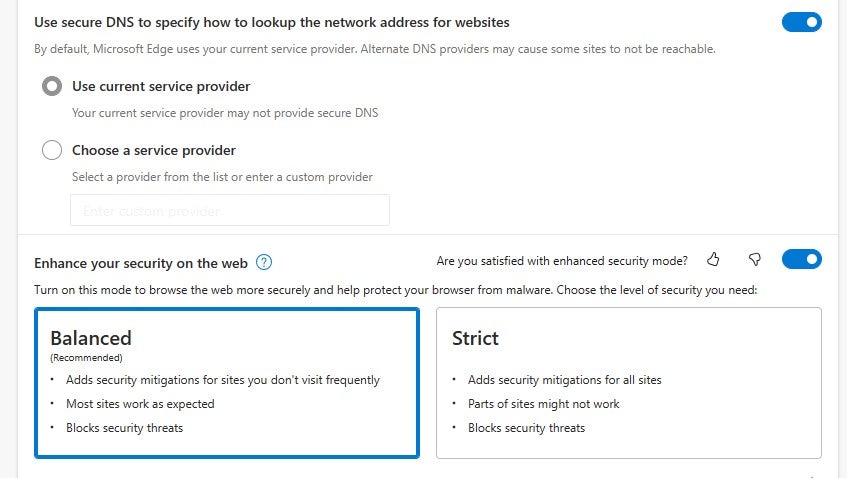
Google Chrome supports DoH and allows users to enable it manually. However, it is important to mention that Google Chrome employs a unique approach to DoH implementation. It doesn’t automatically switch to DoH but rather checks if the user’s existing DNS provider supports DoH. If it does, Chrome upgrades the DNS queries to DoH while retaining the user’s chosen DNS provider. This ensures a seamless transition to more secure DNS queries without altering user settings.
To manually check and activate DoH in Chrome:
Chrome comes preconfigured with several DoH providers such as Google DNS, Open DNS, and CloudFlare.
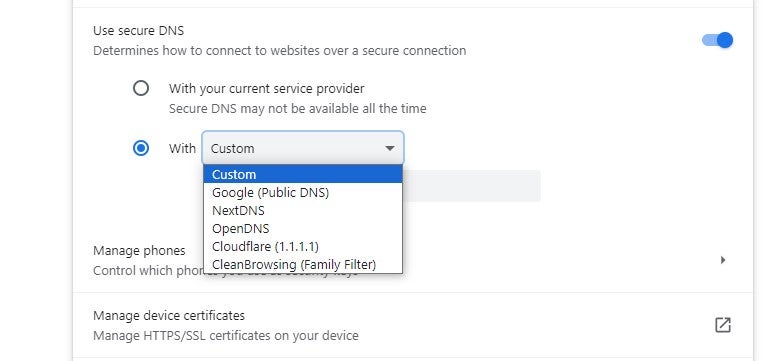
Edge also allows users to manually configure DoH. To do so:
Note that Edge is also preconfigured with several DoH providers.
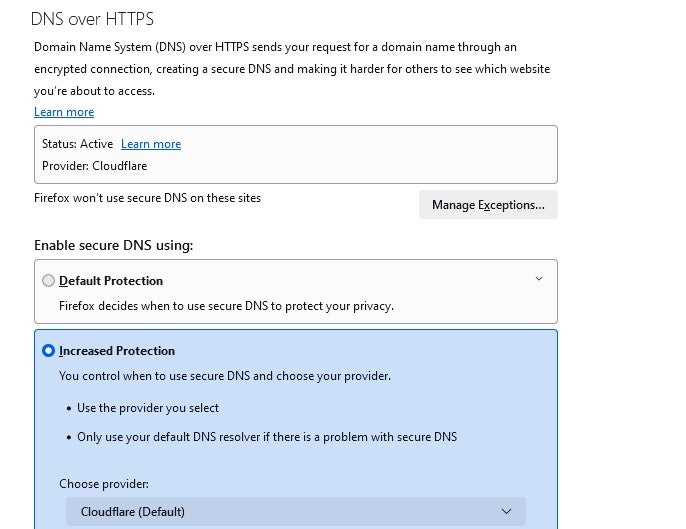
Mozilla Firefox was one of the first browsers to implement DoH and even made it the default for users in several countries. You can enable or disable it through the browser’s settings under “Network Settings.” When you choose increased protection, Firefox defaults to a specific DoH provider, Cloudflare, although users can change this in the settings.
Users can enable DoH in Opera through the browser’s settings under the “Privacy & Security” section. This allows users to either use the default DoH provider or input a custom one. To check your DNS encryption settings:
Opera also uses Cloudflare by default for DoH.
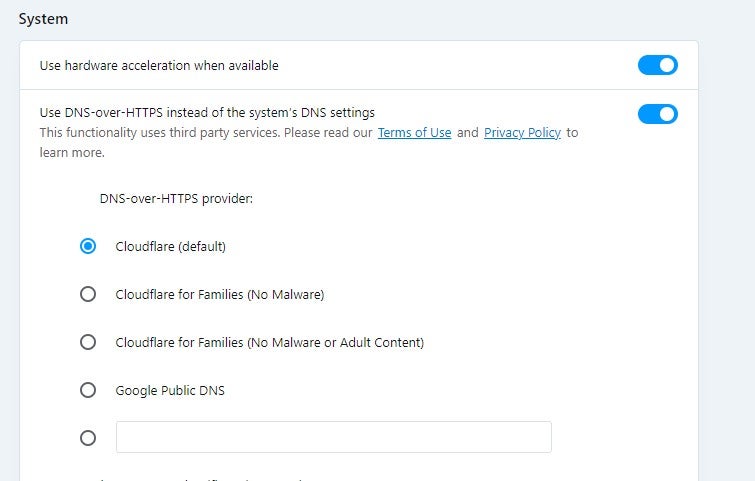
Implementing DoH at the OS level ensures that all applications benefit from DNS queries, extending security beyond just web browsers. However, setting it up may require technical expertise.
In Android you can implement DNS encryption by using either DoT or DoH. Starting from Android 9 (Pie) the OS comes with built-in support for DNS over TLS. This means that all DNS queries made from the device can be encrypted, regardless of the app generating those queries.
To enable this feature users can navigate to Settings >. Internet > Advanced > Private DNS.
From there they have several options to choose from, including automatic selection (where Android will try to use DoT with your current DNS server), turning it off completely (which disables DoT), or entering the hostname of a DNS server that supports DoT.
With iOS 14, Apple introduced support for DNS. Users now have the option to use either DoH or DoT to encrypt their DNS queries.
Configuring the settings for DNS encryption on iOS is not as straightforward as it is on Android. Generally, these settings are configured through profiles that are often installed via mobile device management (MDM) solutions or manually set up using a configuration profile.
Some third-party apps also provide methods for setting up encrypted DNS on iOS devices. After installing a profile or setting up an app, the DNS settings are applied throughout the system, providing a layer of security that benefits all apps.
DNS encryption is an indispensable security measure in today’s cyber landscape. It offers a robust defense against various cyberthreats, including DNS spoofing, man-in-the-middle attacks, and data exfiltration. The adoption of DNS encryption protocols like DoT and DoH is increasingly becoming a standard best practice, not just an optional feature.
Given the escalating threats targeting DNS, as evidenced by recent cyber threat intelligence reports referenced earlier, implementing DNS encryption is not merely advisable but essential for any organization committed to safeguarding its network and data.
Don’t stop at DNS: get to know the best encryption software for protecting data across your network.

Kihara Kimachia is a writer and digital marketing consultant with over a decade of experience covering issues in emerging technology and innovation. In addition to appearing regularly in Enterprise Networking Planet, his work has been published in many leading technology publications, including TechRepublic, eSecurity Planet, Server Watch, Channel Insider, IT Business Edge, and Enterprise Storage Forum.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.