When it comes to enterprise data security and regulatory compliance, consistency is half the battle—one reason that automation is becoming increasingly important to information security. Unfortunately, cloud computing complicates matters, particularly for organizations that have adopted more than one public cloud application. Application security varies between vendors, making centralized, uniform activity control and policy enforcement elusive goals. Redwood City-based cloud security vendor FireLayers aims to make those goals much more attainable with its flagship FireLayers Cloud Application Security Gateway, announced today.
How FireLayers delivers consistent cloud application security
Hosted either by FireLayers or in an organization’s own private cloud, the proxy-based Cloud Application Security Gateway sits between users and whatever cloud applications the enterprise has configured it to protect. Users must go through the proxy to get to the applications. “There’s no way to go around us and still get to the cloud application on the other side,” FireLayers co-founder and CEO Yair Grindlinger told me.
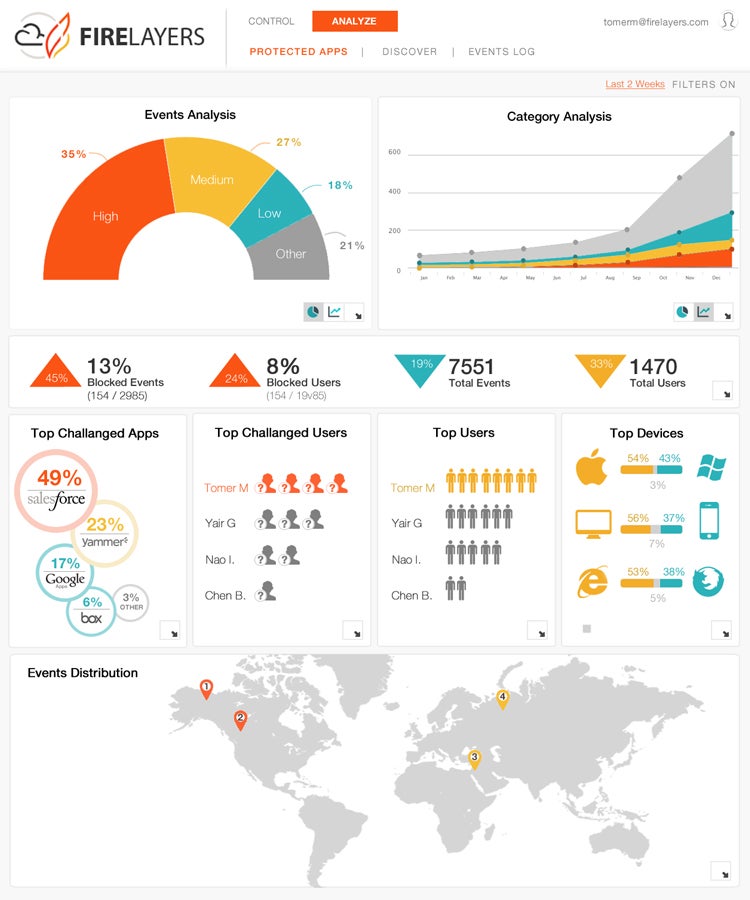
FireLayers Cloud Application Security Gateway dashboard
On the other side of that proxy, FireLayers offers tools for organizations to set and enforce policies “down to the single command level,” according to a FireLayers statement. Individual sessions can be allowed or denied based on such factors as SSL, OS, and browser versions and IP address. For additional security, the FireLayers Cloud Application Security Gateway technology can also create tokenized session IDs to protect sessions from hijacking by hackers or malware. And the gateway can control “any command in any cloud app,” the company claims, including homegrown and customized applications in addition to turnkey public cloud apps.
FireLayers accomplishes this without relying on native APIs, a choice that may make the technology more adaptable. Configuration involves the scanning of the application in order to catalogue all its possible commands; once those commands are discovered, controls, policies, and rule sets can be implemented as well as added to FireLayers’ growing shared database. That database already includes pre-defined controls, policies, and rule sets for a number of popular public cloud applications, including Office 365 and Google Apps.
Integrating with other security tools
The Cloud Application Security Gateway’s open architecture enables integration with other components of an enterprise data security stack. Organizations can use the gateway to connect any of their cloud applications with their existing DLP solutions, for example, extending DLP into public cloud deployments. In fact, DLP integration may turn out to be one of the technology’s strong suits: Grindlinger was CEO of PortAuthority and knows the space well.
“There are a few really great DLP solutions, and we don’t want to compete with them,” he said. Instead, interoperability is key, which is why FireLayers supports the standards-based XACML protocol for interoperable access control.
Among the other technologies with which the FireLayers Cloud Application Security Gateway can connect are antivirus and malware protection, SIEM, and encryption.
“As a cloud gateway, we should be open,” Grindlinger said.
Breaking away from the cloud encryption gateway concept
Speaking of encryption, the FireLayers Cloud Application Security Gateway’s application- and command-based approach to security breaks from the recent trend of data-centric cloud security gateways. When asked about cloud encryption gateways, Grindlinger focused on their limitations. File encryption is easy, he pointed out, but functionality is key in cloud applications, and encryption of database content within cloud applications while preserving application functionality remains a challenge. Very few vendors can do it. CipherCloud, whose brand of cloud data encryption retains search and sort functionality in Salesforce, Office 365, Gmail, and AWS, comes to mind, and Grindlinger credits the vendor as “by far the most advanced company in the market when it comes to structured data,” but granular data encryption within cloud applications remains a niche play, he said. Still, FireLayers does acknowledge the importance of encryption as part of an overall cloud data security strategy.
“As the policy, you can define that a certain type of data should be encrypted in the cloud, and we can make sure that that data doesn’t go to the cloud unencrypted,” Grindlinger explained.
Unsolved: The shadow IT cloud security challenge
One area where enterprises may find that the FireLayers Cloud Application Security Gateway falls short is shadow IT. Unauthorized use of cloud applications can lead to significant security vulnerabilities or compliance violations. Since the FireLayers gateway must be configured to fit specific cloud applications, its key utility will likely lie in the protection of corporate data and the monitoring of user activity within IT-sanctioned services, rather than end user-adopted apps. FireLayers is just getting started, however. The company promises that it will follow up its flagship solution with more cloud security, compliance, and IT governance tools in future.
Header photo courtesy of Shutterstock. Screenshot courtesy of FireLayers.