
Image: jijomathai/Adobe Stock
IAM tools control and authorize employee access to data, software, and networks as needed. Compare top IAM software to choose the best one for your business.

Identity and access management (IAM) tools are software solutions that manage digital identities and their access to resources in an organization. They help organizations to control and manage user access to critical information and systems.
With the constantly rising complexity of IT environments and as cyberthreats continue to increase, choosing the right IAM tool becomes even more high-stakes.
To help you make such an important decision, here are our picks for the top 8 IAM tools and software in 2023:
Before diving into individual reviews, let’s compare these IAM tools based on key features that are most relevant to potential users.
| SSO | MFA | RBAC | Adaptive authentication | Compliance management | Starting price | |
|---|---|---|---|---|---|---|
| Okta | Yes | Yes | Yes | Yes | Yes | $2/user/mo. |
| JumpCloud | Yes | Yes | Yes | Yes | Yes | $2/user/mo. |
| Auth0 | Yes | Yes | Yes | Yes | Yes | $23/mo. |
| Microsoft Entra ID | Yes | Yes | Yes | Yes | Yes | $6/user/mo. |
| Ping Identity | Yes | Yes | Yes | Yes | Yes | $3/user/mo. |
| SecureAuth | Yes | Yes | Yes | Yes | Yes | Contact sales for quote |
| OneLogin | Yes | Yes | Yes | Yes | Yes | $4/user/mo. |
| CyberArk | Yes | Yes | Yes | Yes | Yes | Contact sales for quote |

Best for an extensive network of integrations
Okta channels the power of the cloud to offer flexible access to applications regardless of device and time and enforce robust security protocols. It does this through a powerful and extensible platform that focuses on identity. Okta excels in providing a wide range of integrations and robust multi-factor authentication (MFA) features. It’s a top choice for organizations that require extensive network integrations.

| Pros | Cons |
|---|---|
| 7,000+ integrations. | Cumbersome device switching. |
| Robust MFA. | Can be complex for users with simple IT needs. |
| Adaptive security policies. | High cost for small businesses. |
Okta’s pricing covers two tiers, Workforce and Customer Identity Cloud. The former offers a range of products whose prices range between $2 to $15 per user per month while the latter offers three products; B2B plans starting at $130 monthly, B2C plans starting at $23 monthly, and enterprise plans that require you to contact Okta sales.

Best for cloud-based directory service
JumpCloud is revolutionizing the directory service landscape by offering a cloud-native solution. It eliminates the need for on-premises Active Directory and LDAP servers, providing a unified platform for user management. Businesses looking to streamline their directory services without the hassle of maintaining physical servers will find this one particularly intriguing.
| Pros | Cons |
|---|---|
| Cloud-native directory service. | Limited built-in reporting tools. |
| Extensive APIs and integrations. | Learning curve may be steep. |
| Zero trust security model. | Costly for organizations with limited budgets. |
JumpCloud offers a free version for up to 10 users, with premium pricing plans like A La Carte at $2, SSO Package at $7, Core Directory Package, at $11, JumpCloud Platform at $15 and PlatformPlus at $18, all per user per month billed annually.

Best for customizability and flexibility
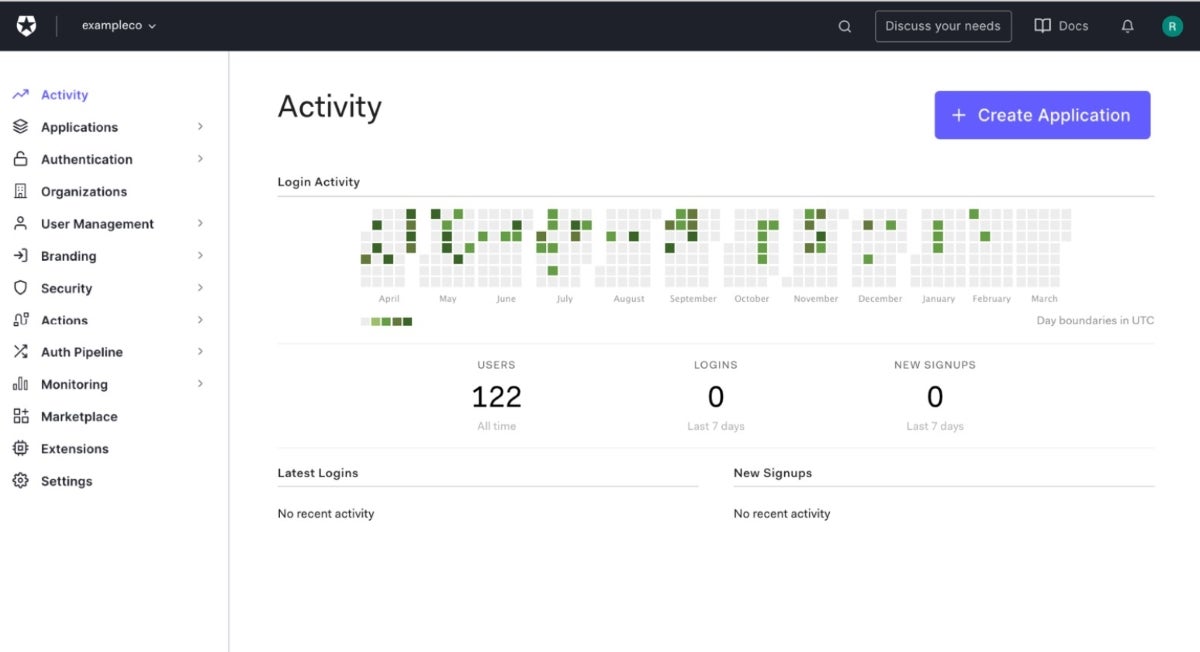
Auth0, an independent product within Okta, stands out for its high level of customizability that gives businesses the flexibility to tailor their authentication processes. With a rich set of APIs and SDKs, it’s a developer-friendly platform that’s adaptable to complex use cases. The extensive documentation makes it easier for the platform to meet your organizational needs.
| Pros | Cons |
|---|---|
| Highly customizable and flexible. | Deployment can be complex. |
| Rich set of APIs and SDKs. | Limited language support. |
| Extensive documentation and support. | A challenge building multi-tenant applications. |
Aside from a free plan, Auth0 premium plans are based on B2C, B2B, and B2E use cases. B2C ranges from $23 to $240 per month for 1,000 monthly active users; B2B is between $130 and $800 per month for 500 active users, while B2E requires you to contact Auth0 for a quote.
Best for Microsoft ecosystem
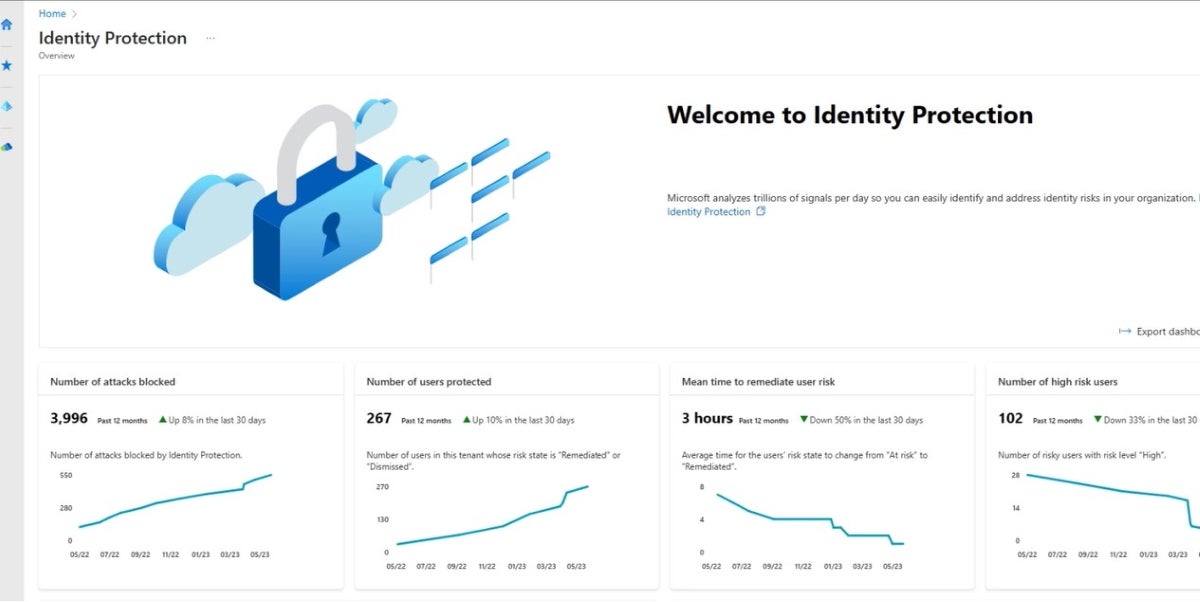
Microsoft Entra ID, formerly Microsoft Azure Active Directory, is an enterprise-level identity service that offers seamless integration with other Microsoft products. If your organization is already invested in the Microsoft ecosystem, Entra ID is an ideal choice, providing a cohesive and streamlined user management experience. It also offers robust security features, making it a thorough solution for identity and access management.
| Pros | Cons |
|---|---|
| Seamless Microsoft integration. | Complexity in non-Microsoft environments. |
| Robust security features. | Licensing can be confusing. |
| Highly mature and scalable solution. | Higher cost for premium features. |
In addition to a free plan, Entra ID’s pricing starts at $6 per user per month for its P1 plan, $9 per user per month for P2, and $7 per user per month for the Governance plan.

Best for a balance of user experience and security
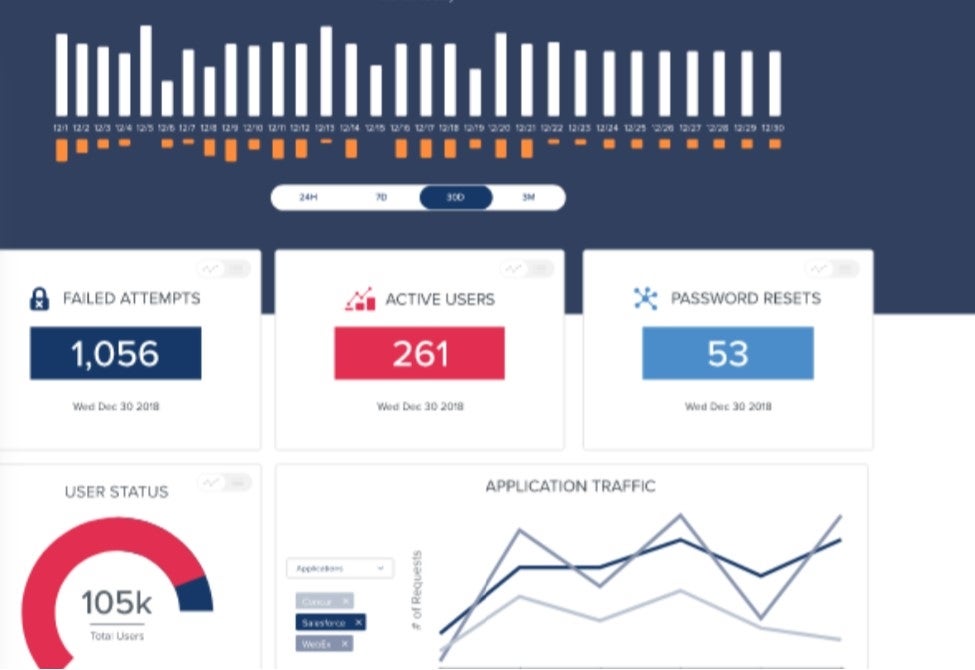
Ping Identity focuses on providing both a secure and user-friendly experience through an intelligent platform. It offers solutions like SSO and MFA without compromising on user convenience. Users can even design workflows through Ping’s drag-and-drop capabilities. For a balance between robust security and ease of use, Ping Identity is a strong choice.
| Pros | Cons |
|---|---|
| Robust security features. | Setup can be complex. |
| Adaptive risk management. | Pricing can be complicated. |
| Extensive third-party integrations. | Very technical documentation. |
PingOne for Customers’ pricing starts at $20,000 per year while PingOne for Workforce Starts at $3 per user per month.

Best for adaptive authentication
SecureAuth IdP supports flexible and secure authentication experiences for workforce, customers, and partners. It excels in adaptive authentication, offering a dynamic approach to security that adjusts based on various risk factors. SecureAuth’s Identity Platform is designed to reduce friction for legitimate users while stopping attackers in their tracks, which makes it a worthy consideration for organizations that value flexible yet robust security measures.
| Pros | Cons |
|---|---|
| Adaptive authentication risk checks. | Learning curve may be steep. |
| Supports multi-cloud deployments. | Advanced features may need more technical capabilities. |
| Lots of options for MFA methods. | Limited support for certain features. |
For SecureAuth pricing information, you’ll have to contact their sales team as it’s not publicly listed.

Best for simplified access management
OneLogin is an IAM tool that seeks to simplify the complex access management landscape by focusing on ease-of-use and quick deployment. This makes it ideal for businesses that want to get up and running quickly without compromising on security. Additionally, its unified access management platform streamlines the user experience across all devices.

| Pros | Cons |
|---|---|
| Easy to use and deploy. | UI can be unintuitive. |
| Unified access management. | Occasional latency issues reported by users. |
| Strong MFA options. | Limited customization options. |
For the Advanced and Professional tiers of its Workforce Identity product, OneLogin’s pricing starts at $4 and $8 per user per month respectively. However, for the Customer Identity product, contact sales for pricing information.

Best for IDaaS and privileged access management
CyberArk is a leader in privileged access management, making it a go-to solution for dynamic enterprises that need a security-first approach to identity security. Organizations that need to manage many privileged accounts and sensitive data will find CyberArk to be of interest.
| Pros | Cons |
|---|---|
| Strong privileged access management. | High cost of ownership. |
| Detailed auditing and compliance reports. | Complex to set up and maintain. |
| Enterprise-level security. | Limited MFA options. |
While it does not list its pricing publicly, CyberArk invites prospective users to sign up for free trials and demos for a feel of the product and talk to CyberArk experts for pricing information.
When selecting an IAM solution, you should always consider the features that align with your organization’s needs. Some key features to look out for include SSO, MFA, RBAC, adaptive authentication, and compliance management.
With SSO, the login process is made easier as users can use one set of credentials to access multiple services. This improves user experience while reducing the risk of password-related breaches.
MFA adds an extra layer of security by requiring multiple forms of verification before granting access. This makes it that much harder for unauthorized users to gain access.
RBAC allows administrators to set permissions based on roles within an organization. This ensures that users have appropriate access to the resources they need, and not the ones they don’t — thereby enhancing compliance and security.
Adaptive authentication adjusts the authentication process based on risk factors like user behavior, device, and location. This provides a healthy balance between security and user convenience.
Compliance management features help organizations adhere to legal and regulatory requirements. This is crucial for businesses in sectors like healthcare, finance, and government, where data protection regulations are stringent.
Choosing the right IAM software goes beyond just comparing a list of features. There are a variety of other factors you’ll want to take into consideration:
Above all, your choice will be guided by your use case and your distinct needs.
To deliver the comparison of the eight tools listed above, we first established the features that should be part of a great IAM tool today.
In looking at the feature sets of the tools, we compared how each tool approaches each feature, with a focus on how robust each tool’s security features are, as IAM’s key function is to enhance security.
We then assessed the user experience of the tools, which was greatly assisted by demos and trials as well as feedback from verified user reviews.
Finally, we considered the cost of each tool as cost is a major purchasing factor. All these put together gave us a balanced evaluation of IAM software.
IAM solutions can include a variety of different elements all working together to guard and manage access based on user identity, but most include the features listed above, such as SSO, MFA, RBAC, and adaptive authentication.
A centralized IAM solution is easier to manage but may create a single point of failure. A decentralized system can offer more robust security but may be more challenging to manage. The choice will ultimately come down to your business’ infrastructure and needs, such as the size and skill of your IT department, your budget, and any particular industry considerations such as compliance, risks, and regulations.
No, IAM (Identity and Access Management) is a broader term that includes various features like SSO and MFA. PAM (Privileged Access Management) is a specific element of IAM and focuses on managing privileged accounts.
To have oversight over access to your organization’s resources, IAM tools are key. The right one will depend on what your organization needs, including the level of security required, the size of your organization, and your budget. By considering the comparisons in this guide, you can make an informed decision.
For a more general understanding of network security, read our network security guide and learn about all the types of network security solutions you can implement for a complete, holistic defense.

Collins Ayuya is a contributing writer for Enterprise Networking Planet with over seven years of industry and writing experience. He is currently pursuing his Masters in Computer Science, carrying out academic research in Natural Language Processing. He is a startup founder and writes about startups, innovation, new technology, and developing new products. His work also regularly appears in TechRepublic, ServerWatch, Channel Insider, and Section.io. In his downtime, Collins enjoys doing pencil and graphite art and is also a sportsman and gamer.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.