Multifactor authentication (MFA) is a security measure that requires users to provide multiple forms of identification to access a system or account. MFA makes it more difficult for unauthorized users to access accounts even if they have stolen a password. It is a simple and effective way to protect accounts from being hacked.
Whether it’s for your personal online accounts or in a corporate setting like finance, healthcare, or insurance, MFA is a powerful tool to prevent unauthorized access, data breaches, and fraudulent activities. When you see that notification asking you to turn on MFA, it’s strongly recommended that you take advantage of this feature to add a significant layer of protection to your accounts.
MFA is a critical component of modern identity and access management (IAM) policies. Instead of the traditional username-password approach, MFA mandates users to present multiple verification factors for accessing resources like cloud accounts, applications, networks, or VPNs. These factors could include OTPs via SMS/email, tokens, or various other methods.
Table of Contents
Why you should activate multifactor authentication
Simple authentication methods that rely on a single factor, such as a username and password, are easily compromised by attackers. Cyber attackers can use a variety of techniques to steal credentials, like phishing attacks, password spraying, and brute force attacks. Once an attacker has obtained a user’s credentials, they can use them to gain access to sensitive information and systems.
Activating MFA significantly minimizes the risks related to network security vulnerabilities and unauthorized access. Without MFA, you expose yourself to a range of potential dangers like account takeover, data breaches, password vulnerabilities, financial loss, productivity loss, reputational damage, and phishing and social engineering.
Password exposure
Passwords are relatively easy to guess, steal, or crack through various means, such as phishing or social engineering attacks, brute force attacks, or by exploiting weak password choices. Without MFA, if a password is compromised, an attacker can gain unauthorized access to personal or corporate accounts and systems.
Account takeover
Using a password alone to secure an account leaves it open to compromise and takeover. If an attacker is able to obtain or guess the password, they will be able to access the account, which could lead to misuse. Attackers could impersonate the account holder, which could have harmful consequences.
Data breach
Attackers can use stolen credentials to infiltrate online accounts or systems, potentially exposing sensitive data such as customer records, financial information, and intellectual property. The absence of MFA makes it easier for attackers to carry out these breaches, ultimately resulting in the exposure of personal and business data, including financial details, confidential documents, and customer records.
Financial loss
Unauthorized access to financial accounts can result in a range of financial losses, including fraudulent transactions, fund theft, and unapproved purchases. Stolen credentials can further facilitate illegitimate transactions, like credit card fraud or unauthorized wire transfers. In addition, attackers can use stolen information to commit identity theft, which can have a devastating impact on the victim’s financial and personal life.
Productivity loss
Attackers can use stolen credentials to take systems offline, disrupt business operations, and cause a loss of productivity. Recovering from a security incident can be time-consuming and costly for the business.
Reputational damage
Security breaches and compromised accounts can damage personal and professional reputation, as well as online credibility and trustworthiness. Similarly, security incidents can harm a company’s reputation, making it difficult to attract customers and partners.
Phishing and social engineering
Attackers frequently use phishing and social engineering tactics to deceive users into revealing their passwords. MFA can help reduce the impact of these attacks by requiring multiple factors of authentication, including a one-time code or biometric scan, in addition to the password. This makes it more challenging for attackers to infiltrate the accounts, even if they have the user’s password.
How multifactor authentication works
The multifactor authentication process involves three key steps: login initiation, verification of additional factors, and authentication.
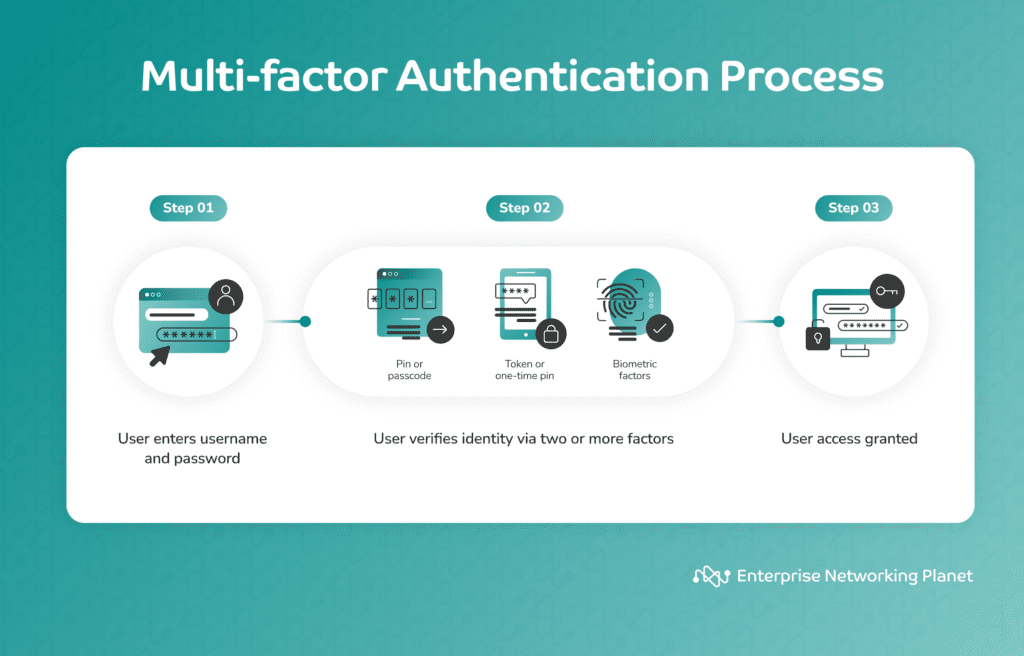
Step 1: User login initiation
MFA begins when a user tries to log in to an account or system, such as an email account, online portal, or corporate network. During this stage, the user usually enters their username and password, which serve as the first authentication factor. This step is common to most login procedures.
Step 2: Verification of additional factors
When MFA is enabled, the user must go through an extra step after entering their username and password. In this step, users are required to provide at least two additional authentication factors. These factors can be classified into four categories:
- Knowledge: something the user knows.
- Possession: something the user has.
- Inherence: something the user is.
- Location: somewhere the user is.
Step 3: Authentication
The system cross-checks and validates all of the given credentials. Access is granted upon successful verification, while any failed credentials result in access denial, thus safeguarding the account from unauthorized entry.
What are the benefits of MFA?
MFA substantially increases protection by mandating users to supply multiple forms of verification. This reduces the risks of password breaches and offers benefits like enhanced security, account takeover prevention, password-related attack protection, phishing mitigation, fraud prevention, secure remote access, higher productivity, improved reputation, and adaptability.
Enhanced security
MFA adds an extra layer of security to protect sensitive data and confidential information, including customer data, intellectual property, and proprietary information. It makes it much harder for attackers to get into accounts or systems illegally, even if a password is compromised.
Account takeover prevention
With MFA activated, the chances of an attacker successfully taking over an account are greatly reduced. This is especially imperative for accounts that contain sensitive information, such as financial or healthcare data.
Password-related attack protection
Employing MFA reduces the risk of common password-related attacks like brute force attacks, credential stuffing, and password phishing because even if an attacker obtains a password, they are unable to access the account without additional factors, such as a one-time code or biometric authentication.
Phishing mitigation
MFA can thwart phishing attacks because even if the account holder accidentally shares their password to a phishing site, the attacker won’t have the second factor needed to gain access.
Fraud prevention
Online banking and financial services commonly use MFA to protect users from unauthorized transactions. It adds extra protection via authentication before financial transactions can be executed. MFA ensures that everyone is who they say they are, preventing unwanted access.
Secure remote access
With the rise of remote and mobile work environments, MFA aids in securing remote access to corporate networks and resources. This is particularly vital for remote workers accessing sensitive company data.
Higher productivity
Implementing MFA can reduce the likelihood of data breaches and brute force attacks. It minimizes downtime and lets employees continue their work without interruption, increasing productivity.
Improved reputation
Utilizing MFA strengthens a company’s reputation. It sends a clear message to users that their privacy and data protection are paramount. This commitment to security can set the company apart from competitors, potentially attracting more customers and building brand loyalty.
Adaptability to evolving threats
MFA makes systems more adaptable to evolving threats by adding layers of security that can be updated as needed. This helps companies stay ahead of emerging threats and keep their security measures robust.
4 main types of MFA
Most MFA authentication methodology is based on one of four types of additional information: something the user has, something the user knows, something the user is, and somewhere the user is. A multi-factor authentication system is built by merging elements from two or three of these categories.
Note that some MFA systems also have backup or fallback methods in case the primary authentication method is unavailable. For instance, if a user cannot receive a one-time code on their smartphone, they may be given the option to receive it via email or SMS.
Something you have
This involves factors based on possession, such as a smartphone, hardware token, smart card, or security key. Users may need to enter a one-time code generated by an app on their smartphone or insert a physical token into their computer.
In many MFA systems, especially those using a mobile app or token generator, one-time codes are generated and are only valid for a short period of time. These codes add to security because they change frequently and are difficult for attackers to predict.
Something you are
Biometric factors fall into this category, such as fingerprints, facial recognition, or voice recognition. Users have to provide a fingerprint scan or look into a camera for facial verification.
Some MFA systems require advanced biometric methods like iris scan, retina scan, hand geometry, palm vein pattern, signature dynamics, keystroke dynamics, and DNA authentication.
Something you know
Knowledge-based factors can be used in addition to the initial password, such as a security question or PIN. Some MFA systems utilize a different piece of information that the account holder knows, like a PIN, specific question, or code.
Somewhere you are
Location-based authentication adds an extra layer of security by verifying a user’s physical location during login. It supplements traditional MFA factors such as passwords and tokens with geolocation data, allowing systems to authenticate users based on their expected or usual location. Unexpected login attempts from unfamiliar areas trigger additional security checks or access denials, bolstering security by adding context to authentication.
It is worth noting, though, that the effectiveness of location-based authentication relies on accurate geolocation data, which may not be infallible in all cases. Location-based authentication is often used in a zero-trust cybersecurity environment.
Real multifactor authentication examples
Every day, we might be engaging with MFA systems without even realizing it — on social media accounts, smartphones, cloud storage, online banking transactions, and company networks. Here are some real multifactor authentication examples:
Social media
Major social media platforms like Facebook, LinkedIn, and X offer MFA options to protect personal profiles. Users can link their accounts to authentication apps or receive codes via email or text messages.
Smartphones
Biometric MFA features like fingerprint recognition and facial recognition are commonly used to unlock smartphones and access personal data.
Cloud storage
Google Drive, iCloud, AWS, and Azure all use MFA to secure personal files, documents, and cloud resources. Users authenticate with their credentials and then use a mobile app or hardware token to submit a second factor of authentication.
Online banking
It’s common for personal online banking accounts to employ MFA. Users may receive one-time codes or use biometric authentication to access their financial information safely.
Company networks
Many organizations implement MFA to safeguard their corporate networks and resources. Employees typically need to enter their username and password and give two or more authentication factors.
Process for setting up MFA on most programs
The setting up process for MFA can vary depending on the specific service, platform, or application. However, the general steps involve enabling MFA, selecting its method, verifying setup, and testing.
- Enable MFA. The user initiates the process by logging into their account and proceeding to enable MFA within the account settings.
- Select the MFA method. The next step involves choosing a preferred MFA method, such as a mobile app, SMS, or email.
- Verify setup. The user follows the on-screen prompts to complete the verification process for their chosen MFA method.
- Test and secure recovery. After setup, the individual should perform a test login to ensure functionality and establish recovery options if necessary, strengthening overall security.
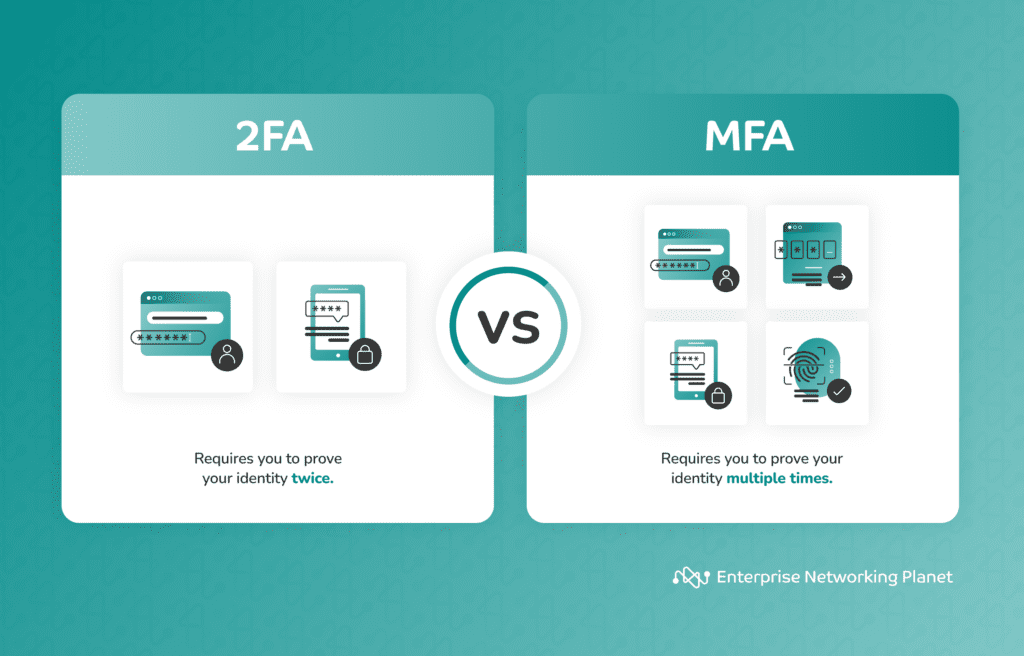
MFA vs. two-factor authentication (2FA)
Authentication strategies were initially designed to reinforce security while maintaining simplicity. Users were required to provide two security keys for 2FA processes to validate themselves as authorized users. Common forms of 2FA included a user ID and password or an ATM bank card and PIN.
MFA and 2FA are often used interchangeably, but they differ slightly. 2FA is essentially a subset of MFA as it mandates using only two authentication factors, whereas MFA can involve two or more factors.
To counteract hacking incidents and attackers who could obtain or bypass passwords and compromise ATM cards, companies and security vendors sought more robust user authentication methods involving additional security factors.
Future of multifactor authentication
The future of MFA is closely tied to adaptive MFA and artificial intelligence (AI). These advancements usher in an era where MFA adjusts intelligently to user behavior and context, elevating security while ensuring user convenience. AI and MFA integration promises robust protection against evolving threats, marking a significant shift in digital identity security.
Adaptive MFA
Adaptive MFA is an advanced authentication system utilizing AI and ML to boost security. It analyzes user behavior and contextual factors like location, device, and network to assess risk. If unusual activity is detected, it can prompt additional authentication steps. This approach offers a dynamic balance between security and user convenience.
Adaptive MFA also incorporates biometrics, enhancing identity verification during a session. It represents the future of authentication, facilitating context-aware, continuous authentication for improved security.
Incorporating AI into MFA
Integrating AI into MFA systems is a major advancement in security technology. AI-driven MFA continuously learns from user behavior and adapts authentication requirements in real time to address emerging threats. This is done by assigning risk scores to events and dynamically adjusting authentication factors based on predefined business policies.
For example, low-risk scenarios may grant access with just a username and password, medium-risk situations may prompt additional SMS code verification, and high-risk behaviors may lead to access denial.
In addition, AI introduces several critical elements to MFA, including behavioral biometrics, which analyzes individual patterns in user behavior through continuous monitoring. Risk-based authentication driven by AI evaluates the risk associated with each authentication attempt, taking into account factors such as user location and device type. These AI-powered advancements refine security, adaptability, and user-friendliness, positioning AI as a key force in the future of MFA and making it a transformative addition to MFA systems.
Bottom line: MFA is the key to preventing unauthorized access
MFA is the key to preventing unauthorized access and comprehensive digital security. It plays a vital role in securing a network.
MFA stands as the first line of defense, establishing simple yet effective security measures that guarantee that even if one layer is breached, the system remains secure. By implementing MFA, individuals and organizations are not only protecting their own interests but also upholding a commitment to data integrity, privacy, and the trust of their clients and users.
MFA isn’t just a security option; it’s a security imperative. If you want to keep your accounts secure, MFA is a must-have.
If you want to learn more about different types of network security authentication, read our guide on using authentication for network security.