What’s on your network and how vulnerable is it to a hacker attack? Having a clear picture of this is a vital part of effective network administration, and one way to build up such a picture is by network mapping using a port scanner.
Port scanning is the art of sending packets onto the network and analyzing what comes back – and what doesn’t. By sending packets to specific ports and IP addresses it’s possible to build up a picture of the IP addresses of devices that are connected, what OSes they are running, what ports they have open, and the services running on those ports. (Of course there are other ways of doing this, but since port mapping is one of the first types of reconnaissance a hacker is likely to perform, doing your own port mapping will give you a clear idea of what hackers may find out.)
There are many open source port mappers, the best known one of which is called Nmap (short for network mapper.) Nmap is available for Linux, Windows, Solaris and other platforms, from http://insecure.org/nmap/ . It’s a very flexible scanner with stealth scan options designed to evade intrusion detection systems (IDS), and by using these you can get practice in spotting the signs of intrusion attempts in your logs.
In this article we’ll be looking at some of the more straightforward uses of Nmap. The examples used are based on Nmap 4.20 running on Linux, but the same commands should work on any other platform. If you read our article about building a portable security tool with the ASUS Eee PC and Ubuntu, Nmap is an excellent candidate for immediate installation.
Getting Started
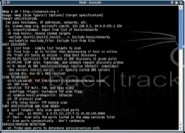
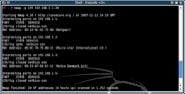
Start Nmap in a terminal window by simply typing nmap and you’ll see a long list of options as in figure 1.
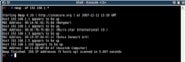
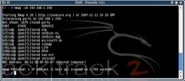
Once you’ve got the hang of the basics it’s worth experimenting with some of these, but to get started with a very quick indication of the machines on your network, type nmap –sP 192.168.1.*.
The –sP option makes Nmap perform a ping scan on all the IP addresses in the specified IP range (in this case 192.168.1.1-255), listing the hosts which respond, as in figure 2.
By default Nmap actually performs a ping scan before doing any other type of scan to establish which IP addresses are actually in use, ignoring any addresses which don’t reply to the ping. This means that if any remote hosts or anything between you and the remote hosts blocks these pings then Nmap will not be aware that they exist, and won’t attempt to interrogate them further. Fortunately you can get around this by using the –p0 option, which forces Nmap to scan any addresses you specify, regardless of whether they respond to a ping.
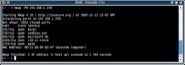
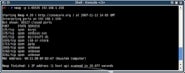
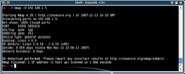
If you know you have a host on your network at 192.168.1.150 that is not responding to a ping, you can still investigate it using nmap –P0 192.168.1.150. (See figure 3) By default Nmap only scans a subset of all the available ports, so to investigate a machine more rigorously you can use the –p option to specify the ports you want to scan – for example all ports in the range 1-65535: nmap –p 1-65535 192.168.1.150 (See figure 4)
The –p option is also useful if you want to investigate machines on your network with a specific port open, such as port 139 (Netbios session service):
To restrict your scan of port 139 to a subset of your network, simply type in an IP address range: nmap –p 139 192.168.1.1-20 (See figure 5)

UDP Scanning
As well as various TCP scans, nmap can be made to perform a UDP scan using the –sU option to get further port information: Nmap –sU 192.168.1.150 (See figure 6)
It’s worth noting that UDP scanning works in the opposite way to TCP scanning. Since a TCP session is initiated by the three-way handshake, nmap’s default SYN scan can tell if a TCP port is open when it receives a SYN/ACK packet in response to its SYN packet. UDP sends no such an acknowledgement – the only response it is likely to receive is an ICMP_PORT_UNREACH error packet from a closed port. So no response indicates that a UDP port might be open, but just to make things more complicated, no response could also simply mean that the UDP or ICMP packet got lost (or filtered). Nmap retransmits packets that may have got lost to cut down on false positives, but the bottom line is that when Nmap reports an open/filtered UDP port, this may not actually be the case.
It’s also worth noting that non-Microsoft systems limit the number of ICMP Port Unreachable messages generated in a given time period, so scanning these systems can be very slow indeed.
Continued on page 2: OS Identification and GUI Front-Ends
OS identification
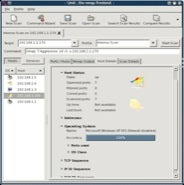
Variations in different vendors’ TCP/IP stacks mean that it’s possible to identify – or have a good stab at identifying – the OS running on each device on the network by analyzing the packets received from them. Nmap can do this for you using its own OS-identification engine if you specify the –O option: nmap –O 192.168.1.5. (See figure 7)
Graphical Front-Ends
If you don’t like using command line programs and remembering the various options, the good news is that a number of Nmap front-ends are available, including NmapFE and the more flexible and arguably easier to use UMIT
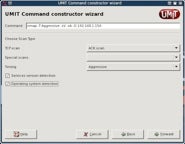
With UMIT you can enter a target IP range, and choose a preset scan from a drop down box. If none of these suit your needs the Command Wizard allows you to build a scan by clicking boxes in a series of forms. As you choose the various components of your scan an Nmap command is slowly built up so you can see the command line options corresponding to the choices you make.
The custom scans you build using the wizard can be saved for reuse later.
The results are presented both graphically – by host or by service – and in a terminal window within the GUI. (See figure 9)
Port scanning is an important way of getting a handle of what’s on your network, and is also a key way for hackers to scout out any vulnerabilities. Nmap is a very important security tool, and the more you pay around with it and explore its features, the more you’ll know about you network and the work that needs to be done to secure it.
So do yourself and your organization a favor: download a copy sooner rather than later, and have at it!