
3D rendering of an obsidian cube with Zero Trust label on a high tech background.
Explore the best zero trust security solutions to fortify your defense against cyberattacks. Learn about identity verification, continuous monitoring, and adaptive access controls.


Zero trust networking operates on the principle that trust should never be automatically granted, regardless of whether a user, device, or application is inside or outside the network perimeter. Instead, it emphasizes strict verification and continuous validation of every entity attempting to access network resources.
Given the increasing sophistication of cyber threats, the need for zero trust network access (ZTNA) solutions has become paramount. These solutions empower organizations to adopt a comprehensive security posture, reducing the potential attack surface and enhancing threat detection and response capabilities.
This article will explore the top eight ZTNA solutions that are empowering organizations to fortify their defenses against cyberattacks in 2023.
The following table contains some of the features found in zero trust networking solutions and their pricing details.
| DDoS protection | Access control | MFA | Cloud readiness | Starting pricing | |
|---|---|---|---|---|---|
| Cloudflare | Yes | Yes | Yes | Yes | Free, or $7/mo per user |
| Akamai | Yes | Yes | Yes | Yes | Contact Akamai for a quote |
| Appgate | Yes | Yes | Yes | Yes | Contact Appgate for a quote |
| Palo Alto Networks | Yes | Yes | Yes | Yes | Contact Palo Alto for a quote |
| Unisys Stealth | Yes | Yes | Yes | Yes | Contact Unisys for a quote |
| Cisco Duo | Yes | Yes | Yes | Yes | Free, or $3/mo. per user |
| Illumio | Yes | Yes | Yes | Yes | Contact Illumio for a quote |
| Perimeter 81 | Yes | Yes | Yes | Yes | $8/mo. per user |
Jump to:
The following section explores our top pick for best zero trust networking solutions, including their features, pricing details, benefits, and drawbacks.

Best overall
Cloudflare’s Zero Trust network solution offers a unified and flexible platform that simplifies setup and operations and guarantees a better end-user experience. The solution has a broad threat intelligence feature that protects against ransomware and phishing attacks by reducing users’ attack surface.
In order to ensure consistent and high-speed protection for all data, Cloudflare inspects all traffic in a single pass. Users can also obtain, activate, and authenticate every access request with FIDO-compliant security keys. This guarantees an extra layer of security as these keys cannot be intercepted or stolen by an attacker once they have been issued.
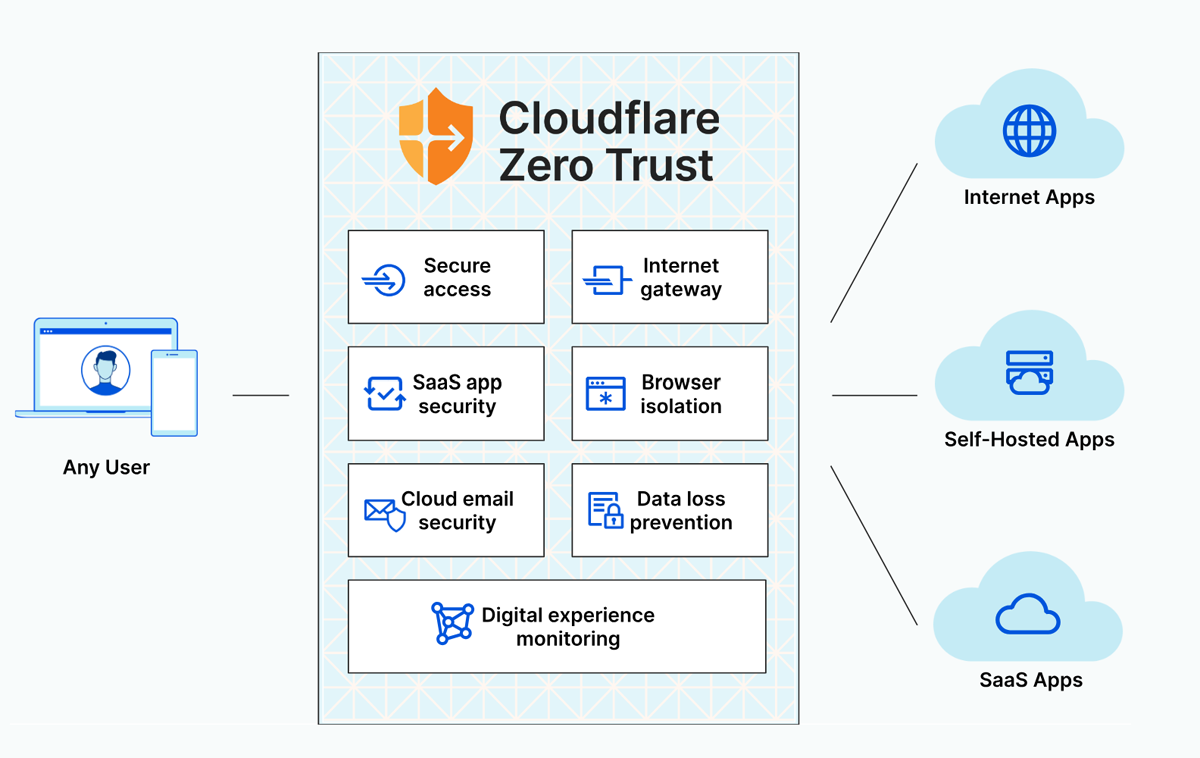
Cloudflare zero trust packages come in Free, Pay-as-you-go, and Contract tiers.

Best for flexibility and control
The primary ZTNA solution offered by Appgate is the Appgate SDP. It has independent gateways and decentralized architecture through which users can connect directly to various resources, including legacy systems, virtualized workloads, and cloud instances. This flexibility ensures efficient and secure connections to different types of environments.
Additionally, Appgate SDP ensures enhanced security by making networks invisible through the implementation of single packet authorization (SPA). It also continuously monitors and automatically adjusts access privileges in response to changes in context and risk levels.
With Appgate SDP, secure access is only granted based on a comprehensive evaluation of each user’s identity, device, and contextual risk.
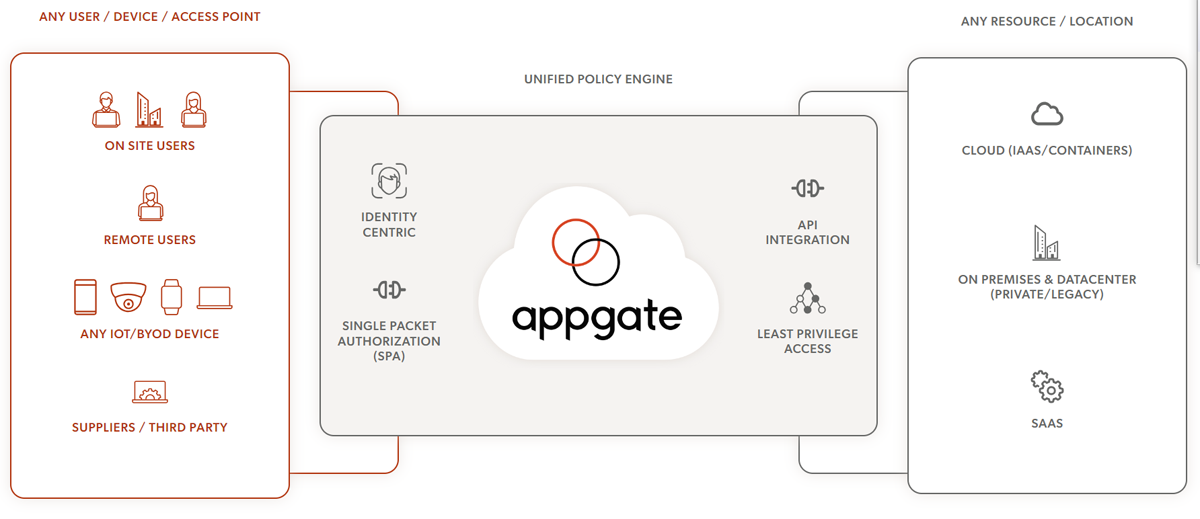
Appgate does not provide pricing details on its site, but third-party reports have placed it on the higher end, at around $100 per month per user. Interested organizations can reach out to them for a quote.

Best for wide coverage
Akamai’s zero trust solution is designed to provide multi-environment security from on-premises or cloud, applications, legacy systems, or SaaS to on-site or remote employees. Akamai is popular for its visibility capabilities and in-house threat-hunting services. Their visibility solution and best offering is Guardicore, which helps users to enforce network segmentation principles. This feature also provides users with security alerts and visuals of activities in their IT network.
Apart from the Guardicore feature, Akamai’s other zero trust capabilities include Enterprise Application Access, which helps protect workforce devices. There is also a compliance feature, which helps users to simplify compliance with regulatory standards such as HIPAA, PCI-DSS, and SOX; a threat-hunting service; and Akamai MFA.
Pricing varies depending on the specific requirements of your organization. Prospective users must contact Akamai directly for accurate pricing information.

Best for companies with hybrid workforces
Palo Alto Networks significantly expanded its zero trust networking capabilities after it acquired several security companies from 2018 to 2020. By integrating these companies, Palo Alto created a comprehensive Zero Trust portfolio.
Palo Alto recently launched ZTNA 2.0, which is an upgrade to legacy ZTNA solutions. The current upgrade offers centralized visibility and management, which helps users to apply consistent policies and shared data for all users and all applications. ZTNA 2.0 combines least privileged access, continuous trust verification, and deep security inspection to protect users, devices, apps, and data. It also offers auto-discovery and onboarding of private applications, as well as support for apps in overlapped private networks.
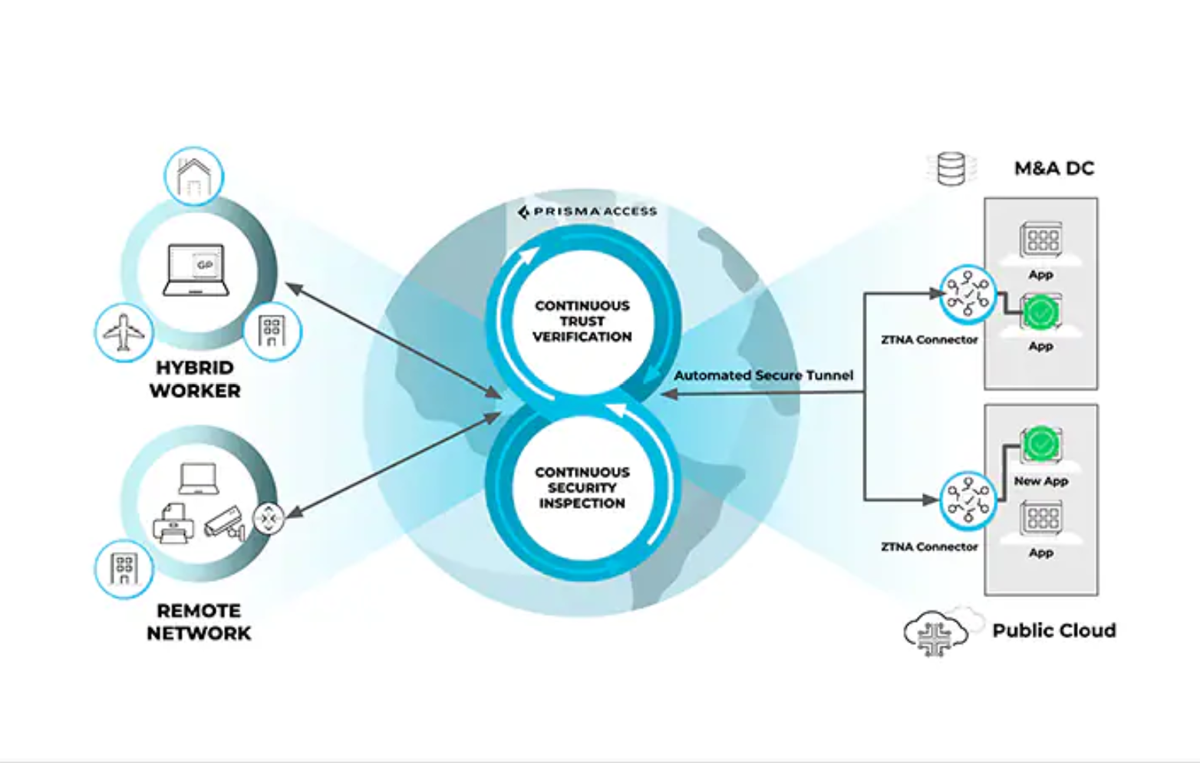
Palo Alto does not publicly release pricing information. Contact the company directly for a quote.

Best for advanced security options
Unisys Stealth focuses on enhancing network security using identity-based key management for encryption. It allows for secure communication between different groups within a network while ensuring that unauthorized parties cannot access or observe their workstations and servers. Instead of relying on IP addresses, encryption keys are assigned based on user or device identity. This approach ensures that access rights are tied to individual users, removing the dependency on network topology.
In addition, Unisys Stealth seamlessly integrates with enterprise identity management systems like Active Directory or LDAP, making the key distribution process transparent to users. They also utilize FIPS 140-2 compliant algorithms for encryption and key exchange, making it suitable for protecting sensitive data during transmission.
Unisys does not publish any pricing information for its services. Contact the vendor for a quote.

Best for easy setup
Cisco advanced into the zero trust networking market in 2018 when it acquired Duo Security, and two years later, they were named a leader in the 2020 Zero Trust Platform wave. Their framework breaks down zero trust architecture into three pillars: User and Device Security, Network and Cloud Security, and Application and Data Security.
They offer Push Phishing Protection, provide visibility into the health status of devices trying to gain access to networks, detect ongoing attack attempts and secure access to private resources.
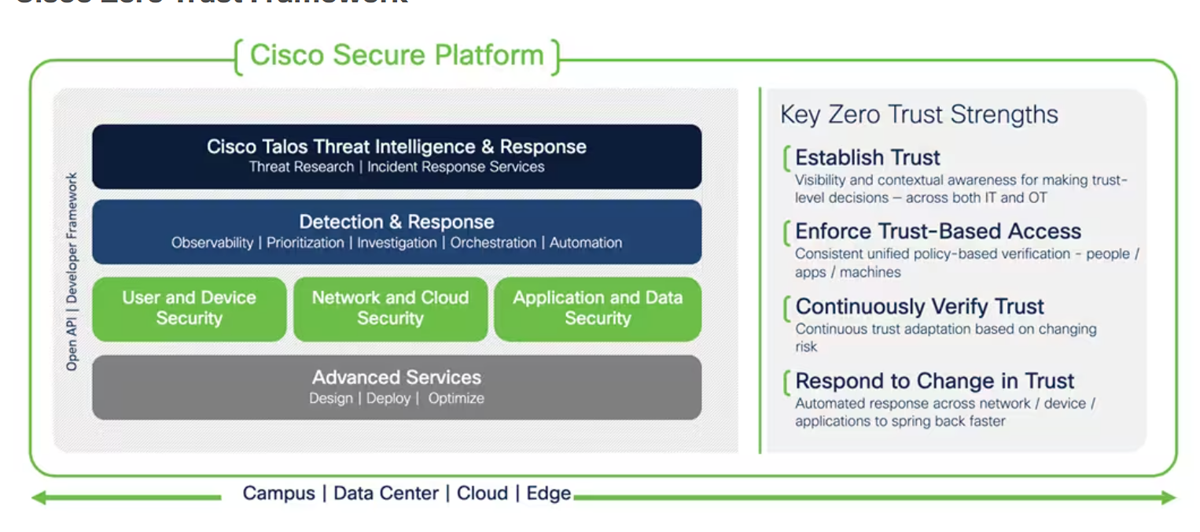
Cisco offers multiple pricing options, along with a 30-day free trial.

Best for segmentation
Illumio offers Zero Trust Segmentation (ZTS) which allows businesses to effectively control access to applications, gain valuable insights into vulnerabilities, and implement data segmentation policies to mitigate the risk of data breaches.
It achieves this through continuous visualization of workload and device communication that enables organizations to gain insights into their network environment. With this information, granular policies can be established, allowing only necessary and desired communication while minimizing potential risks. Additionally, Illumio’s ZTS capability automatically isolates breaches by restricting lateral movement within a network, whether it’s during an attack or as a preventive measure.
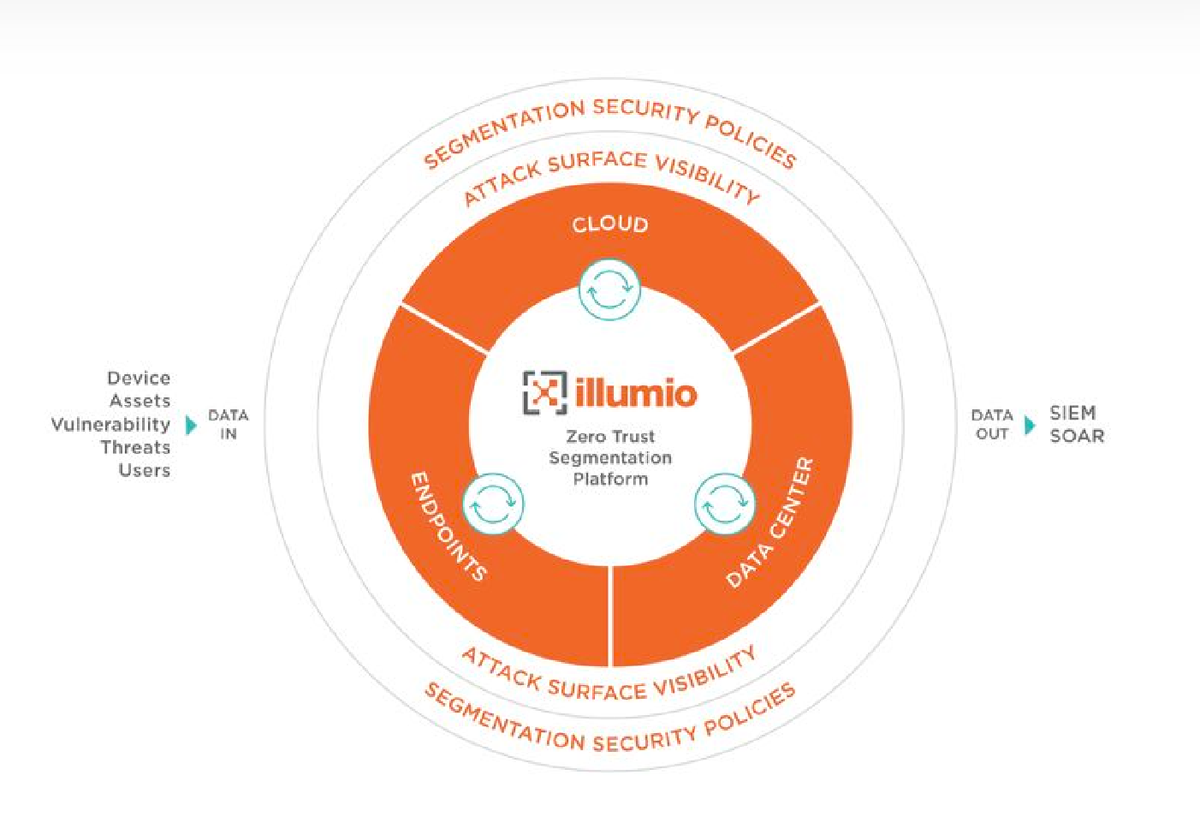
Illumio offers many live demos you can register for, but they do not release their pricing information to the public. You’ll have to contact them directly for a quote.

Best for extensive integration with other tools
Perimeter 81‘s ZTNA allows organizations to effectively manage and safeguard network access for all employees (both remote and on-site) while minimizing the expenses associated with traditional physical solutions. Their price point can be beneficial for small businesses, but larger organizations can discuss enterprise pricing with the Perimeter 81 team.
This solution offers network monitoring from a single dashboard. It has a unified and secure network that includes features like Firewall as a Service, Malware Protection, and Web Filtering. Additionally, with a network of over 50 locations around the world, businesses can easily expand without limitations.
Perimeter 81 offers four pricing options with a 30-day money-back guarantee on all plans.
Any quality zero trust networking solution should include MFA, least privilege access, network segmentation, adaptive access controls, and threat intelligence integration.
Zero trust networking solutions typically incorporate MFA, requiring users to provide multiple forms of verification, such as a password, biometric data, or a security token. This adds an extra layer of security by reducing the risk of unauthorized access, even if one factor is compromised.
ZTNA solutions by nature enforce the principle of least privilege access, which means that users and devices are only granted the minimum level of access required to perform their specific tasks. This limits the potential damage that can be caused in the event of a compromised account or device.
Segmentation — or, better yet, microsegmentation — involves dividing the network into smaller, isolated segments or zones. Each segment has its own security controls and policies, and access between segments is strictly controlled. ZTNA solutions implement this to prevent lateral movement of threats within any network and contain potential breaches.
The adaptive access controls feature dynamically adjusts access privileges based on various factors such as user behavior, device posture, and contextual information. This ensures that access rights are continuously evaluated and adjusted to align with the current security posture and risk level.
ZTNA solutions often integrate with threat intelligence platforms and security tools to gather information about emerging threats, vulnerabilities, and known malicious entities. This integration helps identify and block suspicious activities or connections, enhancing the overall security posture.
Selecting the right ZTNA solution is a crucial decision that can significantly impact your organization’s security and productivity. With so many options available on the market, it’s essential to navigate through the choices effectively.
To help you make an informed decision, consider key factors like scalability and performance, ease of use and management, service and support, and ability to deal with security breaches.
It is important to choose a solution that can scale effectively to meet your organization’s needs. Consider solutions that offer flexible architecture capable of accommodating an increasing number of users, devices, and network segments without compromising performance. Ensure the software supports redundancy and high availability measures to minimize downtime and maintain continuous protection.
Assess the software’s user interface for intuitiveness and ease of navigation, as it will be crucial for administrators to configure and monitor the zero trust environment effectively. Look for software that provides a centralized management console or dashboard that allows administrators to define, update, and enforce policies easily. Check if the software offers automation features for policy enforcement, device onboarding, and security event response to streamline operations and reduce manual effort.
Beyond the initial setup and implementation, it’s crucial to evaluate the level of service and support provided by the solution. Look for comprehensive customer service and support offerings, including access to knowledgeable support staff, training materials, active peer communities, and the possibility of dedicated account managers.
If your organization deals with sensitive data, it’s vital to assess how different companies have performed in major security breaches. Particularly, consider their ability to defend against DDoS attacks, which can severely impact network capabilities. Look for zero trust software solutions with a proven track record of effectively mitigating DDoS and other cyberattacks, providing you with the peace of mind that your data is safeguarded.
Zero trust security challenges trust at every level, unlike traditional network security models that assume trust within the network perimeter.
Zero trust security solutions reduce the risk of data breaches by implementing strict access controls and continuously verifying user identities and device integrity.
The selection process for the top eight zero trust networking solutions in 2023 involved comprehensive research and evaluation. We considered the availability of features that every quality zero trust solution should have for each selection, narrowing down our list to only those solutions that had everything on our list. Those solutions were then assessed individually based on vendor-provided information, product documentation, and customer feedback.
Adopting a zero trust approach can help organizations shift from a perimeter-based security model to a more granular and comprehensive approach that focuses on authenticating and verifying every user, device, and network component before granting access to resources.
While our review of top zero trust networking solutions provides all the key features needed in adopting a zero trust networking strategy, users are advised to do their own research in order to pick the solution that best meets their business needs.
If you’re working on establishing zero trust solutions on your network, be sure to explore all our ZTNA content on the pros, cons, and processes for setting up the technology at your organization.
For more in-depth looks at some of the solutions in this article and others, you can also see these product comparisons:


Franklin Okeke is a contributing writer to Enterprise Networking Planet, as well as an author and freelance content writer with over 5 years of experience covering cybersecurity, artificial intelligence, and emerging technologies. In addition to pursuing a Master's degree in Cybersecurity & Human Factors from Bournemouth University, Franklin is an entrepreneur with a passion for startups, innovation, and product development. His writing also appears regularly in TechRepublic, ServerWatch, and other leading technology publications.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.