

Main node with shield and check icon interconnected to different nodes with lock icons on a city background.
Learn everything you need to know about network-based firewalls, from how they work to their types, deployment, and benefits.
A network-based firewall is a crucial component of network security that protects private networks by blocking unauthorized traffic and giving organizations granular control over their infrastructure.
It examines network packets, applies predefined rules, and acts as a barrier between internal and external networks. A network firewall empowers individual and corporate users to enhance security and mitigate the risks of cyber attacks.
When properly configured, a network-based firewall secures sensitive data by allowing users to safely access the resources they need while keeping out hackers or malicious programs trying to get into the protected network. Additionally, administrators can set up rules to restrict access within the network, preventing users from running specific programs or reaching certain websites.
This article will explore what a network firewall is and its role in safeguarding against cyber threats. We’ll delve into different firewall types, their features, and deployment options so you can make informed decisions in taking proactive measures to protect your network from potential threats.
Network-based firewalls are an integral part of securing modern network infrastructures. These tools enforce firewall policies to control and monitor network traffic. They examine data within the Transmission Control Protocol/Internet Protocol (TCP/IP) communication layers, namely:
These layers guide data movement from its origin to its destination.
Network firewalls create a border between the private and external network, or the internet. They inspect incoming and outgoing packets to distinguish between normal and malicious traffic.
The operation of a network firewall also relies on Access Control Lists (ACLs). ACLs ensure precise control over traffic by authorizing or denying packets based on predefined criteria such as IP addresses, port numbers, and specific protocols.
In simple terms, incoming traffic goes through a firewall, which authenticates and evaluates it based on firewall policies and ACL rules. If a packet meets the allowed rules, it can pass through to the intended destination. If it matches a deny rule, the firewall blocks it from entering the network.
Here is a visual representation illustrating how a network-based firewall works:
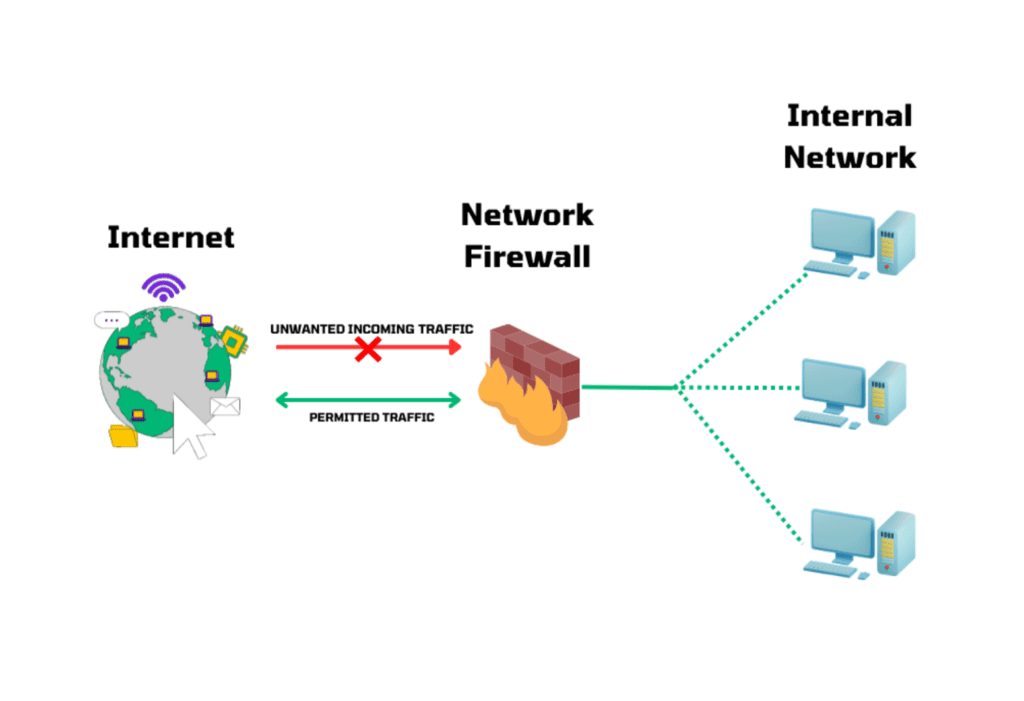
Understanding how network firewalls work and following best practices for setting up firewalls are essential in building an effective security infrastructure. By implementing the appropriate firewall rules, conducting regular audits, and collaborating with network professionals, organizations can amplify their cybersecurity defenses.
There are various types of network firewalls catering to different network security needs, such as application-layer, packet-filtering, and circuit-level firewalls. Here are some of the most commonly used ones, along with their key features.
Application-layer firewalls, also known as application-layer gateways (ALGs), offer upgraded security mechanisms tailored to individual applications.
Instead of relying solely on IP and port information, these firewalls operate at the application layer of the OSI network stack, performing deep inspection and filtering for specific application protocols.
By providing granular control and deep inspection capabilities, ALGs increase the overall security posture of networks and applications.
Packet-filtering firewalls analyze individual packets of data and make decisions based on preset rules. They primarily focus on information like source and destination IP addresses, port numbers, and protocols.
This type of network firewall is known for its simplicity, scalability, and efficiency in handling large volumes of network traffic. However, it lacks advanced insight into packet content and may not offer granular control over specific applications or user activities. It is also vulnerable to IP spoofing attacks.
Also referred to as a circuit-level gateway or transparent proxy firewall, this type of firewall gives control over network traffic at the session level. It applies security measures once a connection between devices is established. It monitors the handshake process and makes sure that the connection follows the firewall’s rules and policies.
The circuit-level firewall does not modify the data beyond what is necessary for authentication and identification. It facilitates secure communication between trusted devices and untrusted networks.
Proxy firewalls act as intermediaries between internal clients and external sources. They extend an additional layer of security by shielding the internal network from direct contact with external entities.
This type of network firewall enables deep inspections of application-layer traffic and supports user authentication.
On the downside, a proxy firewall comes with a performance overhead due to the processing and forwarding of network requests. Moreover, it has more complex configurations compared to other firewall types.
NGFWs combine the capabilities of traditional firewalls with advanced network security features to spot and block threats like malware, intrusion attempts, and suspicious activities. They incorporate deep packet inspection, intrusion prevention systems (IPS), and application awareness.
An NGFW also delivers application visibility and control and applies policies based on user identities, enabling precise access control.
However, configuring and maintaining NGFWs can be complicated and require additional performance resources.
A stateful inspection firewall does more than packet filtering; it also keeps track of network connections. It makes intelligent decisions about allowing or blocking packets by remembering established connections like source and destination IP addresses, port numbers, and connection status.
In addition, it is compatible with different network protocols and applications. One of the drawbacks of this firewall type, though, is understanding particular applications. It can be vulnerable to elaborate attacks that exploit protocol weaknesses or manipulate the firewall’s settings.
Organizations have several deployment options — including hardware, software, and service-based — to consider in choosing the best firewall to secure their network. These choices enable them to adapt their firewall strategies to meet unique requirements and network architectures.
A hardware-based firewall uses a physical device as a dedicated security appliance, protecting the internal network from external threats and filtering network traffic.
This device connects to different network segments and implements security policies. By placing it between the external network and the server, it works as a barrier against intrusions and evaluates incoming traffic for threats.
Hardware firewalls inspect all traffic, granting or denying access based on predefined rules. They have features like packet filtering, stateful inspection, intrusion prevention, and VPN support for more network security. They can handle high volumes of network traffic and reliably facilitate secure communication within the network.
Software-based firewalls are computer programs that inspect data going in and out. They track and control data on individual computers.
This firewall type offers similar features as physical firewalls and is customizable to detect suspicious activity. It protects against external threats and prevents attacks on other networks.
Some advantages of using software-based firewalls include lower costs, scalability, and remote deployment.
A Firewall-as-a-Service (FWaaS) is a cloud-based firewall solution that delivers advanced security capabilities from the cloud. It has access controls, threat prevention, and IPS features.
An FWaaS eliminates the need for on-premises hardware or software firewalls, as the service provider takes care of infrastructure maintenance and updates. As a result, businesses can focus on their core operations.
In the current technological landscape, network firewalls are an imperative element of a solid cybersecurity strategy, acting as the first line of defense against hackers and malware. These tools can deal with modern threats and expanding networks like cloud solutions. They safeguard networks, data, and resources from diverse vulnerabilities.
Without firewalls, networks become exposed to attacks and data breaches. Threat actors can steal sensitive information or disrupt operations.
To ensure full security, organizations should place firewalls between networks and the internet and establish clear policies and strategies.
Implementing a network-based firewall brings numerous advantages to an organization’s cybersecurity posture, including monitoring and logging, access control, and segmentation capabilities. Here are some of the key benefits of using network firewalls.
Security is the primary purpose of having a network firewall. Network-based firewalls bring a constant barrier against unwanted access and malicious activities.
Through monitoring and controlling incoming and outgoing network traffic, firewalls help prevent unauthorized individuals or software from accessing sensitive data and resources within a network.
Network firewalls maintain detailed logs of network activities like connection attempts, traffic patterns, and security events.
By continuously monitoring traffic and logs, firewalls deliver advanced network analysis, giving administrators a deeper understanding of network health and conditions.
Firewalls equip organizations with the means to define and administer access control policies, effectively managing who can access their networks and resources.
By preventing unauthorized entry attempts, firewalls bolster security, protect valuable assets, and minimize the risk of breaches.
Network firewalls are instrumental in preventing a wide range of threats and attacks. They block malicious traffic like viruses, malware, ransomware, and distributed denial-of-service (DDoS) attacks.
Using intrusion detection and prevention systems, firewalls build up security by uncovering and stopping suspicious activities and known attack patterns. They also control system entry points, blocking virus attacks and keyloggers.
Firewalls can divide a network into smaller subnetworks or segments, known as network segmentation. This allows organizations to control traffic between different areas of the network, limiting the impact of potential security breaches.
Network segmentation also strengthens monitoring capabilities, boosts performance by reducing congestion, localizes technical issues, and increases security.
Application control lets organizations track and manage specific applications on their networks. Network administrators can block unapproved applications, apply acceptable use policies, and reduce the risks associated with potentially harmful apps.
This leads to an improvement in network stability and a decrease in malware-related risks and costs.
With the rising prevalence of cybercrime, network-based firewalls are nonnegotiable in today’s enterprise, regardless of the size of the organization. They provide more than just protection against hackers by offering features such as collecting security data, automating protections, and resolving networking issues that impact productivity. On top of that, a reliable network firewall restricts access to unsafe sites, taking overall network security to the next level.
By investing in reputable firewall solutions, organizations can safeguard their digital assets, uphold data privacy, and protect their reputation in the modern digital environment.
Get more info and tips on firewalls with our in-depth coverage on everything you need to, from purchase to setup to maintenance.
Liz Laurente-Ticong is a tech specialist and multi-niche writer with a decade of experience covering software and technology topics and news. Her work has appeared in TechnologyAdvice.com as well as ghostwritten for a variety of international clients. When not writing, you can find Liz reading and watching historical and investigative documentaries. She is based in the Philippines.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.