Secure Access Service Edge (SASE) is a cloud-based service that secures and accelerates network access for users and devices from any location. It does this by verifying user and device identities, applying security policies, and connecting users to the network over a secure connection.
SASE supports different kinds of network edges, including branch offices, remote workers, and Internet of Things (IoT) devices. It streamlines network management and lowers costs by replacing hardware with cloud subscriptions. Organizations can scale SASE up or down as needed.
The SASE framework provides a consistent and secure network experience for all users and devices, which is vital for businesses that need to be flexible and adaptable. SASE’s cloud-native design makes network management simpler and gives businesses the ability to deal with changing network security threats.
Table of Contents
How does SASE work?
SASE operates by delivering Software-Defined Wide Area Networking (SD-WAN) and security services at the network edge from a single cloud platform.
It uses a global network of points of presence (PoPs), which are physical locations that support network connectivity and security services. SASE intelligently steers the traffic to the nearest PoP, where it performs advanced security inspection directly in the cloud. It then verifies the identity of users and devices, enforces policy-based security, and enables secure access to applications in the cloud, data center, and SaaS environments.
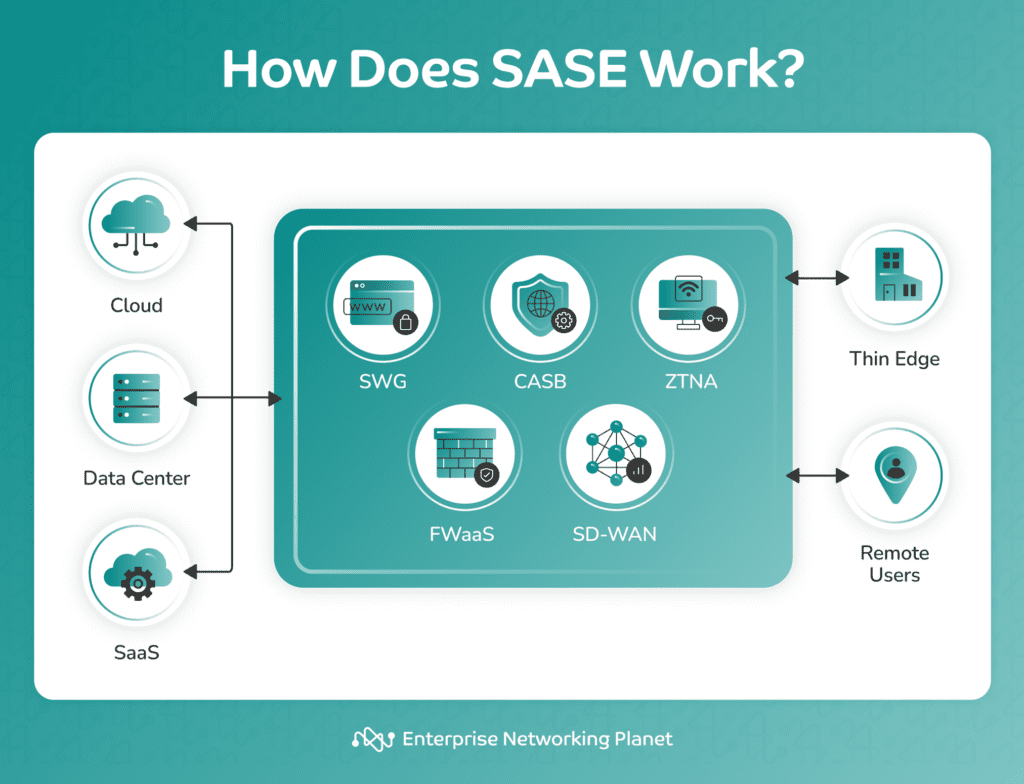
SASE supports different network edges, such as branch offices, remote workers, and IoT devices.
Core functions of SASE
SASE combines networking and security services to bring a unified, cloud-based approach to protecting users and data. Its core functions include network connectivity, security services, zero trust security model, cloud-native architecture, global PoPs, simplified management, secure remote access, cost efficiency, and scalability.
- Network connectivity: SASE facilitates secure and effective network connectivity, making sure that users and devices can access corporate resources, applications, and data from anywhere, whether they are in the office or remote locations.
- Security services: It incorporates a wide range of security services, like firewalls, intrusion detection and prevention (IDPS), data loss prevention (DLP), secure web gateways (SWG), and threat detection and response. It typically offers these services as software-defined functions in the cloud.
- Zero trust security: SASE follows the zero trust security model, which means that it does not trust any user or device by default, even if they are within the corporate network perimeter. Every access request is subject to authentication, authorization, and continuous monitoring to maintain the highest level of security.
- Cloud-native architecture: It is inherently cloud-native, leveraging the scalability, flexibility, and accessibility of cloud services. It eliminates dependency on on-premises hardware and allows organizations to scale resources up or down.
- Global PoPs: SASE vendors operate a network of global PoPs strategically located around the world. These PoPs help optimize network performance and reduce latency for users, regardless of their geographical location.
- Secure remote access: SASE has significant advantages for remote and mobile users by ensuring secure access to corporate resources and data, regardless of their location. It eliminates the constraints of location or device, making security accessible everywhere, around the clock.
- Simplified management: It consolidates multiple functions into a single cloud platform, simplifying network and security management. This reduces complexity, fine-tunes operations, and optimizes overall performance.
- Cost efficiency: SASE can lead to cost savings by eliminating maintenance and upgrade expenses for on-premises hardware. Your organization can also adopt a subscription-based pricing model, aligning costs with their actual usage. This is often more cost-effective than maintaining VPN hardware and software.
- Scalability: Organizations can scale their network and security resources effortlessly to accommodate changing business needs. This flexibility is crucial for dynamic modern organizations.
What are the components of SASE?
The SASE architecture achieves comprehensive network security and connectivity by unifying several key components, including SGW, cloud access security broker (CASB), zero trust network access, firewall as a service (FWaaS), SD-WAN, endpoint security, and unified management.
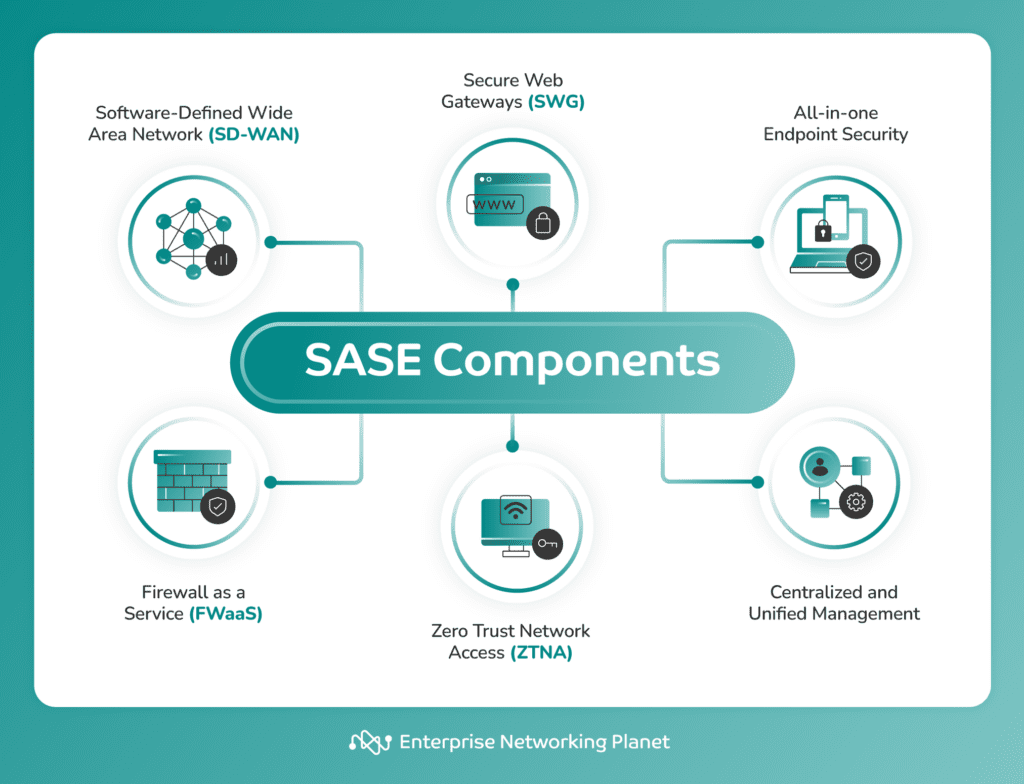
Secure web gateway (SWG)
SWG in the SASE architecture functions as a critical security gateway for web traffic, enabling organizations to enforce policies and defend against web-based threats. SWG safeguards users accessing the internet, whether from remote or corporate network locations, from malicious websites, malware, and other online risks.
Cloud access security broker (CASB)
CASB functions as a security gateway between an organization’s on-premises infrastructure and cloud-based services. Its role includes monitoring and enforcing security policies for cloud applications and services, guaranteeing sensitive data protection, and adhering to regulatory standards.
Within the SASE framework, CASB bolsters organizations’ security as they embrace cloud technologies. CASB also contributes to securing edge networks, as it ensures that cloud services are accessed securely and compliantly.
Zero trust network access (ZTNA)
ZTNA follows the zero trust security model to verify and authorize all users and devices, regardless of their location. ZTNA mandates a rigorous examination of every access request, demanding authentication and authorization from users and devices before permitting access to network resources. This approach helps to defend corporate resources by restricting access only to authorized users.
Firewall as a Service (FWaaS)
FWaaS delivers firewall capabilities in the cloud, allowing organizations to enforce security policies, filter traffic, and protect against threats at the network perimeter. FWaaS guarantees meticulous inspection and filtration of traffic entering or leaving the network, reinforcing security in a distributed and cloud-centric network architecture.
Software-defined wide area networking (SD-WAN)
Software-defined wide area networking (SD-WAN) enables intelligent network routing and optimization. It enables efficient traffic routing over the best available network path, reducing latency and improving performance. It also amplifies network reliability by automatically rerouting traffic in case of network issues, making it a fundamental part of the SASE approach to network optimization.
Endpoint security
Endpoint security in SASE is necessary for safeguarding user devices, such as laptops and mobile phones, from threats, particularly when used to access corporate resources beyond the traditional network perimeter. It applies the zero trust model, demanding authentication and authorization for endpoints before granting access.
This component extends protection to devices operating outside the traditional network perimeter, meeting the requirements of remote and mobile users.
Unified management
Unified management simplifies network security by centralizing policy control and configuration. It offers a single point of control for administrators to configure, monitor, and manage policies, reducing complexity and maximizing efficiency.
This approach ensures consistent policy enforcement and real-time visibility for threat detection and response, while also supporting scalability for easy adaptation to changing requirements. Unified management is the final step in securing a network, as it streamlines the management of all the other components and provides a holistic view of the network security posture.
Top 6 SASE benefits for network security
SASE brings a variety of benefits that enhance network security in today’s dynamic and distributed digital landscape. These include reduced transition costs, minimized latency and bandwidth usage, stronger security, seamless workforce and business expansion, consistent policy enforcement, and granular access controls.
Reduced transition costs
Transitioning to a SASE architecture saves costs by eliminating the need for maintaining and upgrading on-premises hardware. Also, adopting cloud-based services on a subscription basis aligns costs with actual usage, preventing resource over-provisioning.
You can strategically reinvest these savings in security measures like advanced threat detection systems, personnel security training, and other improvements, strengthening overall network security.
Minimized latency and bandwidth usage
SASE optimizes network performance by lowering latency and mitigating bandwidth congestion. Its global PoPs minimize delays for users accessing resources, even remotely. This latency reduction and systematic bandwidth management allow security services to inspect and respond to network traffic in real time, limiting the window for cyberattacks.
Furthermore, better bandwidth management lets security solutions operate effectively and analyze network traffic without bottlenecks.
Enhanced security
SASE provides comprehensive security services by consistently applying firewalls, threat detection, DLP, and ZTNA across the network. This uniformity elevates security by making all access requests go through strict authentication and authorization processes, decreasing the chance of unauthorized access or data breaches.
Seamless workforce and business expansion
With SASE, organizations can accommodate the growth of their workforce and business operations by scaling resources up or down within their cloud-native environment. This adaptability is imperative for network security, as organizations must scale security measures accordingly as they expand and their network traffic increases.
SASE’s ability to seamlessly onboard new branches, remote workers, and partners enables a consistent and robust security posture, regardless of the organization’s evolving network landscape.
Consistent policy enforcement
In a traditional network environment, it is difficult to ensure that security policies are consistently enforced across distributed locations and remote users. SASE simplifies this through a unified platform for defining and enforcing security policies.
By consistently applying policies across the entire network, your organization can maintain a cohesive security posture, reducing the risk of misconfigurations or policy gaps vulnerable to attackers.
Granular access controls
SASE lets organizations implement granular access controls based on user roles, device types, and contextual factors. This granularity guarantees that only the users who need access to specific resources and data have it, reducing the attack surface. By adjusting access permissions, organizations can boost security by minimizing the potential impact of insider threats or unauthorized access attempts.
Challenges of secure access service edge
While SASE offers numerous benefits, it also presents several challenges that organizations must address to fully leverage its potential, such as complex transition, security concerns, data privacy and compliance, user experience, and vendor selection.
Complex transition
Shifting from traditional network and security models to a SASE architecture can be a complex undertaking. Careful planning and execution are essential to integrate various services and components into a unified cloud-based platform.
Security concerns
SASE enhances security through a zero trust model, but it also introduces new security challenges like:
- Siloed departments.
- On-premise security and routing limitations.
- Complex integration.
- Tool sprawl.
Organizations must actively check if robust security measures are in place and effectively configured to prevent vulnerabilities and threats.
Data privacy and compliance
Storing and processing data in the cloud raises concerns about data privacy and compliance with regulations. It is important to guarantee data protection and compliance with industry-specific standards.
User experience
User experience is a challenge in SASE due to potential latency introduced by cloud-based security services, network complexity, geographic distribution variations, scalability issues, integration complexities, and ensuring seamless user authentication and access control within the zero trust framework.
Organizations can optimize network routing, reduce latency through efficient PoP placement, invest in robust global content delivery networks (CDNs), and secure proper load balancing to elevate user experience.
Vendor selection
Selecting an appropriate SASE vendor or service provider can be a major undertaking. The process involves a thorough evaluation of available choices, confirming compatibility with the current infrastructure, and conducting a reliability assessment of the chosen vendor, all of which are key factors in the vendor selection process.
Top 3 SASE vendors
Numerous SASE vendors have emerged to offer their own unique set of features and capabilities in response to the growing demand for flexible and secure network access solutions. Some of the top SASE vendors in 2023 are Prisma SASE, FortiSASE Solution, and Forcepoint ONE.

Prisma SASE
Palo Alto Networks’ Prisma SASE is a cloud-based solution that combines network security, SD-WAN, and Autonomous Digital Experience Management (ADEM). It offers advanced ZTNA security for all applications used by a hybrid workforce, including Prisma SD-WAN for hyperconnected branch locations.
Moreover, Prisma SASE uniquely integrates AI Operations (AIOps) with ADEM for automating complex operations using AI-based problem detection and predictive analytics, making it a scalable and user-focused solution.
While Prisma SASE delivers a comprehensive suite of features, it’s worth noting that the setup can be complex due to its wide range of functionalities and integration capabilities. However, once set up, it provides robust security and automation features that can greatly benefit organizations.

FortiSASE Solution
FortiSASE Solution from Fortinet offers cloud-based security and networking to remote users. It enables organizations to manage SWG, ZTNA, CASB, FWaaS, and secure SD-WAN through a single console on a unified operating system.
This solution levels up the capabilities of the Fortinet Security Fabric. One of its standout features is its utilization of AI for improved security services and real-time threat protection through FortiGuard AI-powered Security Services.
Bear in mind that FortiSASE’s extensive features may lead to high bandwidth usage, affecting network performance. Organizations with bandwidth constraints should factor this in when considering this SASE vendor.

Forcepoint ONE
Forcepoint ONE combines zero trust and SASE technologies, streamlining policy management with a single console. It promotes secure remote work by offering cloud and web security while also securing access to private applications.
This platform provides continuous visibility into user interactions with data, helping maintain compliance across the entire organization.
However, Forcepoint ONE’s comprehensive security features might potentially hinder integration with third-party solutions, which could reduce flexibility for organizations reliant on specific external tools. Before implementing it, you should carefully assess how this new solution aligns with your organization’s existing technology stack.
Bottom Line: SASE in networking
SASE in networking represents a groundbreaking architecture that delivers network and security services as a cloud-based solution. It seamlessly integrates SD-WAN and ZTNA solutions to bolster the security of edge networks and establish secure connections for users, devices, and applications across various locations.This is a significant step up from traditional VPNs, which often struggle to provide such comprehensive and integrated services.
By unifying multiple network and security functions into a single service, SASE simplifies operations, slashes costs, and reduces complexity. Additionally, it optimizes traffic, cutting down on latency, which enhances user experience and performance.
Furthermore, SASE facilitates consistent security policies and protection at all edges, whether they are physical or digital, while simultaneously increasing flexibility and scalability to adapt to evolving needs and demands.
SASE emerges as a proactive solution for fortifying network access, rendering it a compelling choice for contemporary businesses. Though SASE is not yet a fully realized model, it presents a visionary blueprint for the future of secure networking that enterprises can progressively integrate. Through SASE adoption, your business can confidently harness the power of cloud-based SD-WAN architecture.
If you’re considering implementing SASE in your organization, be sure to review our picks for the best SASE vendors, carefully evaluated for a variety of use cases.



