

Image: Sashkin/Adobe Stock
Secure your small or medium-sized business by comparing the best firewall for your specific needs.
Firewalls enable small and medium-sized businesses (SMBs) to establish a critical barrier between internal networks and the external environment. They safeguard against unauthorized access, cyberthreats, and malicious activities, and play a pivotal role in protecting sensitive data.
Investing in an SMB firewall is a proactive step that bolsters the overall security posture of growing businesses, minimizing the risks associated with cyberthreats and ensuring business continuity.
Here are our top recommendations for best firewalls for small and medium business networks:
The comparison table below shows the key differences between SMB firewalls. It gives a summary of the type of firewall product, the available firewall appliance selection, features, and pricing transparency to help you choose the best firewall for small business enterprises:
| Type | Firewall appliance selection | Features | Pricing | |
|---|---|---|---|---|
| Perimeter 81 | FWaaS | N/A | Comprehensive | Starts at $12/user/mo. |
| SonicWall TZ Series | NGFW | Substantial | Wide-ranging | Lacks transparency |
| Palo Alto Networks | NGFW | Extensive | Comprehensive | Lacks transparency |
| pfSense | Traditional | Adequate | Satisfactory | Has a free version. Premium version: $129/yr |
| Sophos XGS | NGFW | Substantial | Wide-ranging | Lacks transparency |
| Cisco Meraki MX | NGFW | Substantial | Wide-ranging | Limited details |
| Fortinet FortiGate | NGFW | Extensive | Comprehensive | Lacks transparency |
| Zscaler Cloud Firewall | FWaaS | N/A | Comprehensive | Lacks transparency |

Best overall firewall for small and medium businesses
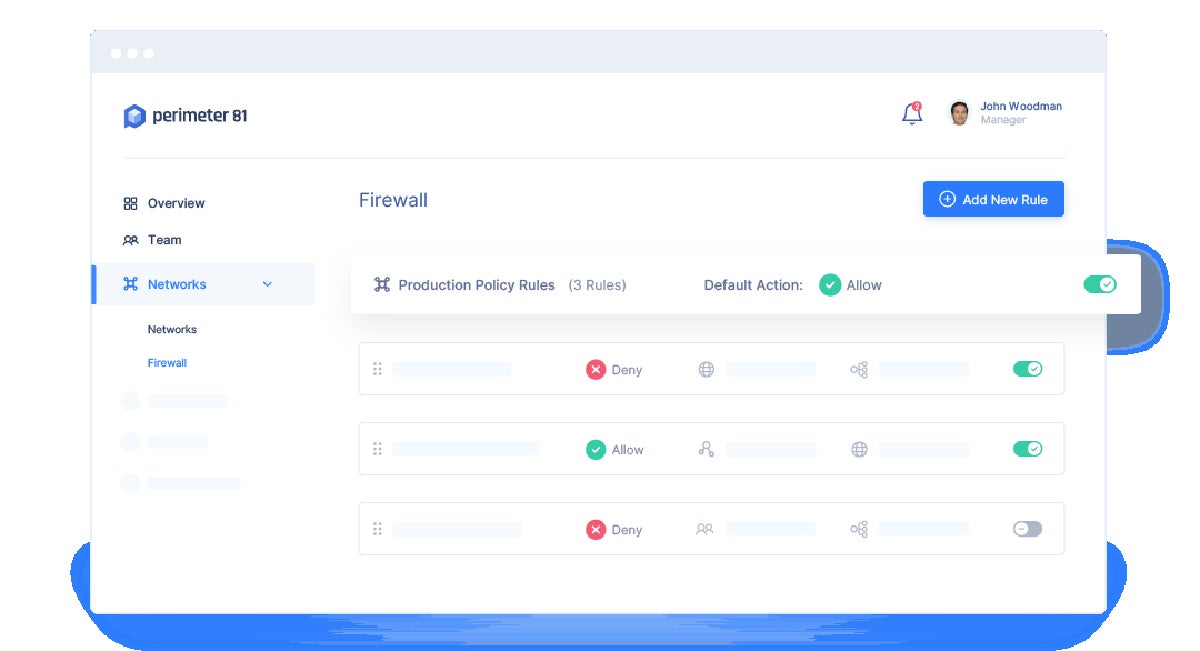
Perimeter 81’s Firewall as a Service (FWaaS) delivers advanced security features, such as multi-factor authentication (MFA), single sign-on (SSO) integration, strong encryption, automatic Wi-Fi protection, and malware protection. It also works seamlessly with various cloud IaaS environments, on-premises firewalls, routers, or SD-WAN devices, making it a flexible and adaptable solution for businesses of all sizes.
As a cloud-based solution, Perimeter 81 FWaaS eliminates the need for physical hardware, reducing costs and easing deployment. It is also scalable, allowing businesses to adjust their security measures as they grow. The solution is manageable from anywhere, at any time, promoting convenience and flexibility.
Recent product development:
Check Point Software Technologies acquired Perimeter 81 in August 2023. Check Point will integrate Perimeter 81’s capabilities into its Infinity architecture for a unified security solution across the network, cloud, and remote users. Perimeter 81 is ideally positioned to enhance Check Point’s secure SASE solution.
Perimeter 81 emerged as our best overall firewall for small business enterprises and medium organizations because it has a comprehensive feature set, wide variety of integrations, and reliable customer support. On top of that, it offers flexible pricing options and is fairly easy to set up and manage.
Its simple user interface (UI) promotes a seamless experience even for non-technical users to navigate and perform tasks, like creating, managing, and securing custom networks that span across multiple regions. Its ability to integrate with major identity providers and support for various VPN protocols make it a versatile solution that can cater to a wide range of business needs.
| Pros | Cons |
|---|---|
| All-in-one ZTNA, SWG, and FWaaS. | Occasional connection issues. |
| Quick deployment. | System slowness from time to time. |
| User-friendly. | No free trial, only a 30-day money-back guarantee. |
| Transparent pricing. |
Perimeter 81 offers the following pricing plans for its FWaaS. It is one of the few vendors who displays pricing information on their page.

Best for advanced security and operational simplicity
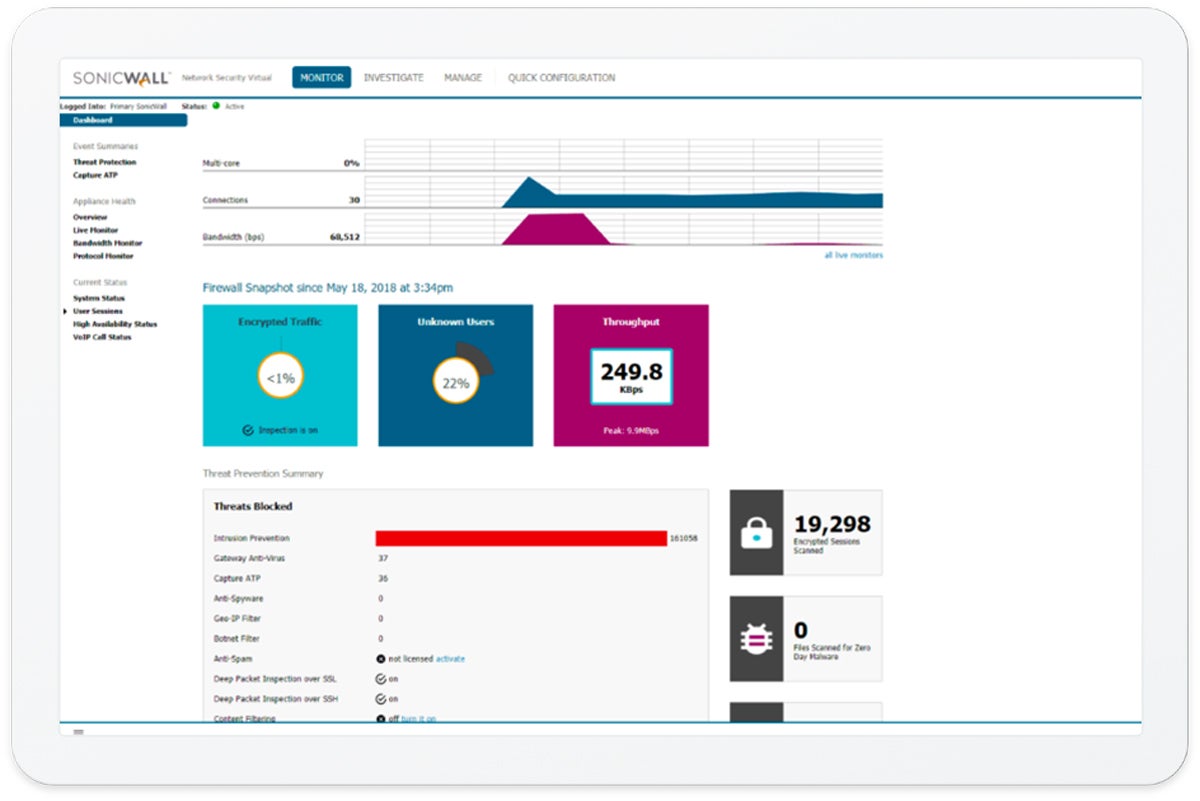
The SonicWall TZ series is a robust line of next-generation firewalls (NGFWs) providing a unique blend of sophisticated security features and operational simplicity. It has cutting-edge capabilities, such as Real-Time Deep Memory Inspection (RTDMI) technology, advanced firewall protection, and multilayer malware protection.
RTDMI proactively detects and blocks unknown mass-market malware in real-time. This, coupled with threat prevention and integrated security solutions, boosts protection against a wide array of threats. Its firewall security offers network management, anti-spam, and a real-time sandbox. Furthermore, its multilayer malware protection eradicates known, new, and updated ransomware variants, and can roll back endpoints to their prior clean state.
Despite its advanced features, the SonicWall TZ series gives importance to operational simplicity. Features like Zero-Touch Deployment streamline the installation and operation process, while the single-pane-of-glass management feature allows for centralized control of all firewall operations. In terms of design, SonicWall TZ balances modern security and ease of use, making it a compelling choice for businesses seeking a reliable and manageable network security solution.
Recent product development:
SonicWall acquired Solutions Granted, Inc. (SGI), a top Managed Security Service Provider (MSSP), expanding its line of cybersecurity solutions. These combined solutions will leverage the latest in AI to provide a differentiated service.
We picked SonicWall TZ because of its user-centric design and around-the-clock protection against persistent cyberattacks. Its network firewall can defend your organization from malware, ransomware, viruses, intrusions, botnets, spyware, trojans, worms, and other malicious attacks.
Aside from that, SonicWall’s clear and intuitive UI can help you quickly understand the status of the firewall, potential security incidents, and other relevant information.
| Pros | Cons |
|---|---|
| Zero-touch deployment. | Reporting needs improvement. |
| Single-pane-of-glass management. | Lacks transparent pricing. |
| RTDMI technology identifies and mitigates threats through deep memory inspection. | Customer support is hard to get a hold of. |
SonicWall doesn’t publish pricing information on their page. Get in touch with their sales department for more details.

Best for complete visibility and control
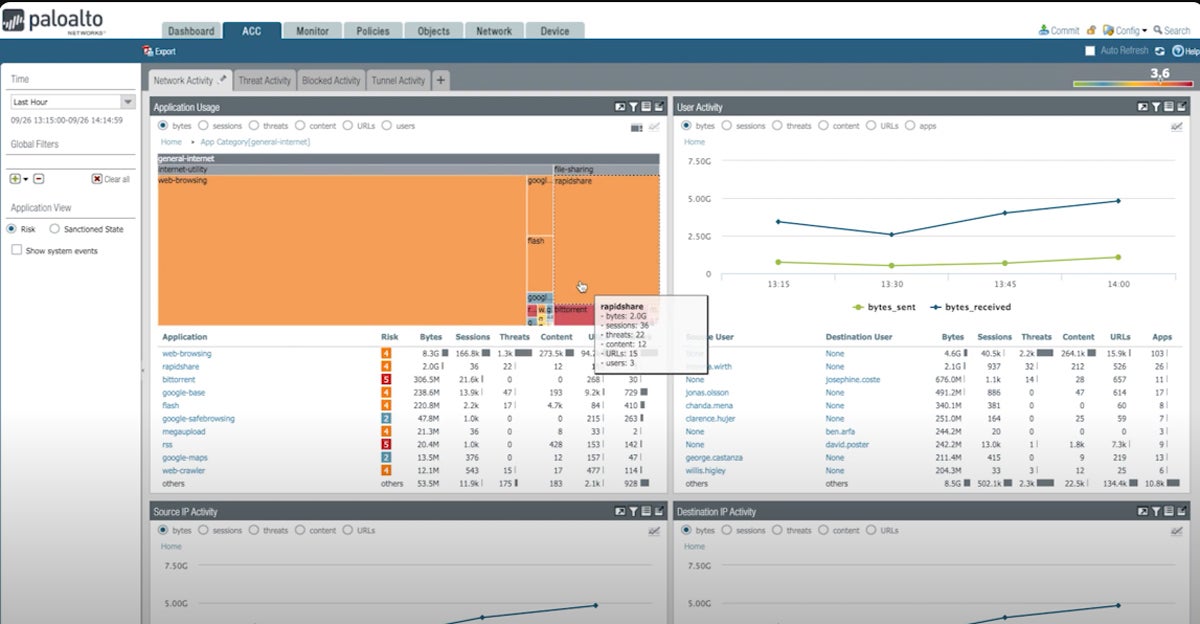
Palo Alto Networks NGFW brings advanced threat prevention, URL filtering, and application visibility and control. One of its standout features is its use of machine learning (ML) capabilities to protect your organization against a vast majority of unknown file and web-based threats instantly. This NGFW adapts and provides real-time protection, offering a level of security that is hard to match.
Palo Alto Networks NGFWs leverage key technologies built into PAN‑OS natively, namely App‑ID, Content‑ID, Device-ID, and User‑ID, to give complete visibility and control of the applications across all users and devices in all locations all the time. Additionally, it can extend visibility to unmanaged IoT devices without the need to deploy additional sensors.
That said, it has an elaborate UI that could make it harder to perform configurations.
Recent product development:
Palo Alto added a feature in August 2023 to further expand its NGFW’s capabilities. Its newly enhanced Capacity Analyzer uses ML models to anticipate resource consumption nearing its maximum capacity and raise alerts in advance to flag potential capacity bottlenecks. This proactive approach makes sure that you receive early notifications about possible capacity constraints, so you can take preemptive action to safeguard your business operations.
We selected Palo Alto Networks NGFW for its scalability and broad integration capabilities. These NGFWs are deployable in various environments, including on-premises and cloud platforms like AWS and Azure, letting SMBs grow and adapt their network security as their business needs change. Moreover, its integration with different third-party tools, like cloud platforms and third-party VPN clients delivers flexibility in securing your network.
| Pros | Cons |
|---|---|
| Complete visibility and control. | Poor customer support quality. |
| Policy automation. | Overwhelming interface. |
| IoT defense. | Lacks transparent pricing. |
Palo Alto Networks doesn’t offer pricing information on their website. To know more, contact their sales team.

Best free, open source firewall
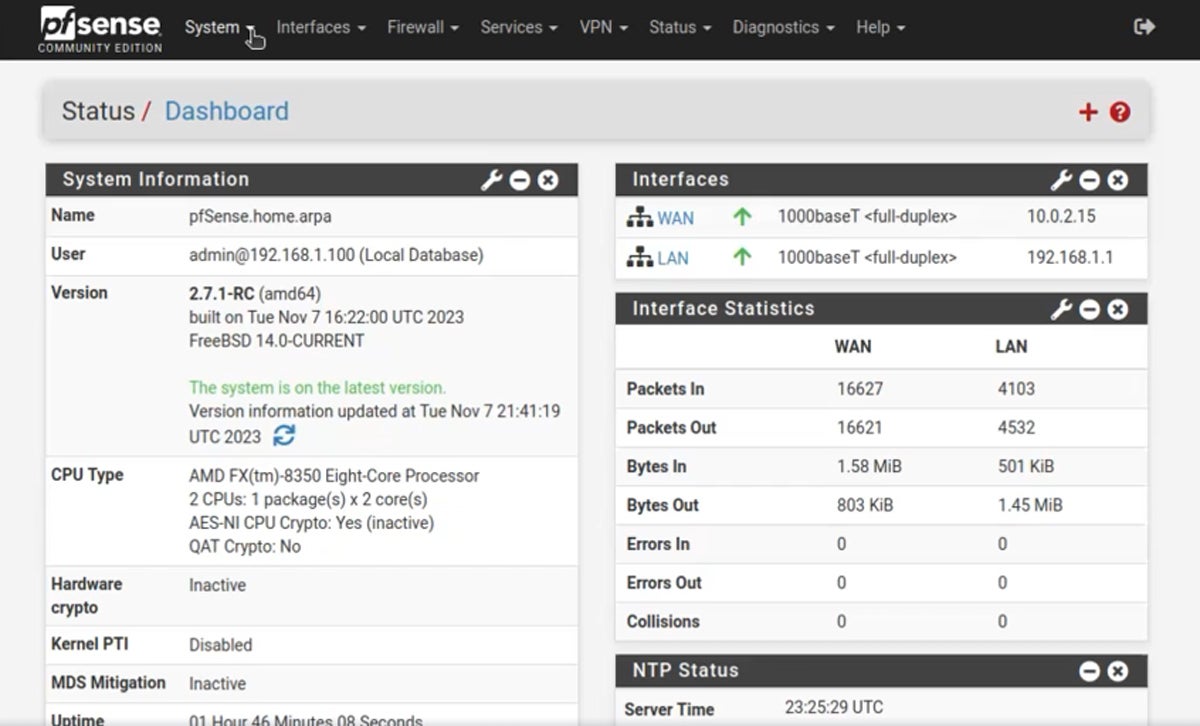
pfSense, developed and maintained by Netgate, is a free, open-source firewall with a wide range of features, such as stateful packet inspection, IP/DNS-based filtering, anti-spoofing, captive portal guest network, time-based rules, and connection limits. It also comes with NAT mapping, policy-based routing, concurrent IPv4 and IPv6 support, and configurable static routing.
What sets pfSense apart from other SMB firewalls is its versatility and cost-effectiveness. You can deploy it with limited hardware resources, making it a low-cost solution for SMBs. In addition, its open-source nature allows for a high degree of customization, enabling it to support numerous use cases.
While pfSense’s UI is designed to be user-friendly, setting up and configuring the software requires a certain level of technical skills. This entails an understanding of networking concepts, firewall rules, and VPNs.
If you’re new to pfSense, there are many resources available to help you get started, including the official documentation, community forums, and several online tutorials. However, if you’re setting up a complex network or you’re not comfortable with these concepts, it might be a good idea to consult with a network professional to avoid security risks.
Recent product development:
Netgate continuously updates pfSense community edition, with the latest update just released recently. This update includes OpenSSL upgrade, introduces Kea DHCP as a feature you can opt into, and enhances SCTP support. Since 2008, Netgate has been the steward of pfSense and has provided resources for its development.
We selected pfSense because of its affordability and flexibility. Since it is free to use and modify, it could bring a significant advantage for SMBs operating on a tight budget. The solution is also customizable to meet the specific needs of different networks, from basic network security to complex protection. So, whether you’re looking for the best firewall for small business ventures or for startups with financial constraints, pfSense could be an ideal choice.
| Pros | Cons |
|---|---|
| Has a free version. | Set up requires a high level of technical expertise. |
| Flexible and customizable. | Steep learning curve. |
| IP/DNS-based filtering. | Some capabilities are only available as add-ons. |
| Transparent pricing. |
pfSense has free and paid versions. The pricing for paid plans are as follows:
Contact Netgate for additional details.

Best for flexible deployment and protection
The Sophos XGS Series firewall gives comprehensive protection for SMBs through deep learning technology for advanced threat prevention and synchronized security that integrates firewall and endpoint defense.
Additionally, Sophos XGS firewalls have built-in web and email protection, network visibility, and flexible deployment options. They also use a pioneering form of ML to detect known and unknown malware without relying on signatures. Together, these features can effectively defend against different cyberthreats, making Sophos firewalls a reliable solution for network security.
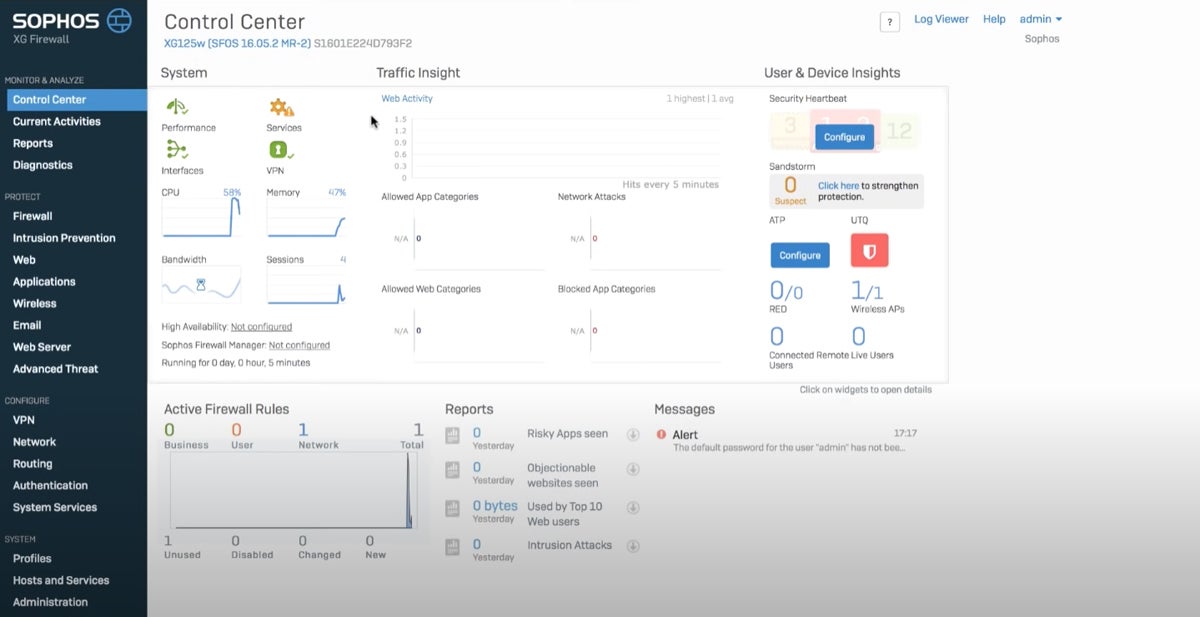
The UI design of Sophos XGS presents an all-in-one view of different security aspects, like system status, traffic insights, user and devices, active firewall rules, and alerts. This detailed design, although informative, may be overwhelming to some users.
Recent product development:
Sophos has incorporated a new feature called Active Threat Response in its Sophos Firewall v20. This feature offers an immediate and automated reaction to active threats. Analysts from Sophos XDR and MDR can directly send threat intelligence to firewalls from Sophos Central. This allows the firewalls to instantly coordinate defenses without requiring manual intervention or creating new firewall rules.
Aside from its rich feature set, we picked Sophos XGS because it gives you flexible deployment options. You can choose from hardware, software, virtual, or cloud deployments to fit your specific network requirements, budget, and IT environment. Furthermore, having multiple deployment options lets you scale your security solutions in line with your business growth.
| Pros | Cons |
|---|---|
| Uses deep learning technology. | Lacks detailed pricing. |
| Comprehensive SD-WAN capabilities. | Steep learning curve. |
| Built-in ZTNA. |
Sophos doesn’t reveal information about their payment models on their pricing page. Reach out to their sales department to get a quote.

Best for remote work
Cisco Meraki MX is a unified threat management (UTM) and software-defined WAN (SD-WAN) with a wide array of sophisticated firewall services. Alongside site-to-site VPN, it has intrusion prevention capabilities powered by SNORT, a Cisco-developed system. It also includes content filtering, anti-malware protection, and geo-based firewalling features.
Meraki MX comes with features particularly beneficial for remote work, like employee onboarding, secure cloud access, quick BYOD set-up, and data protection. Its cloud-based management also facilitates remote system management, configuration, and installation, which are crucial for remote work scenarios. Moreover, the Meraki Systems Manager accelerates remote employee onboarding with seamless provisioning. This means new employees can quickly get set up with the tools they need to work from home.
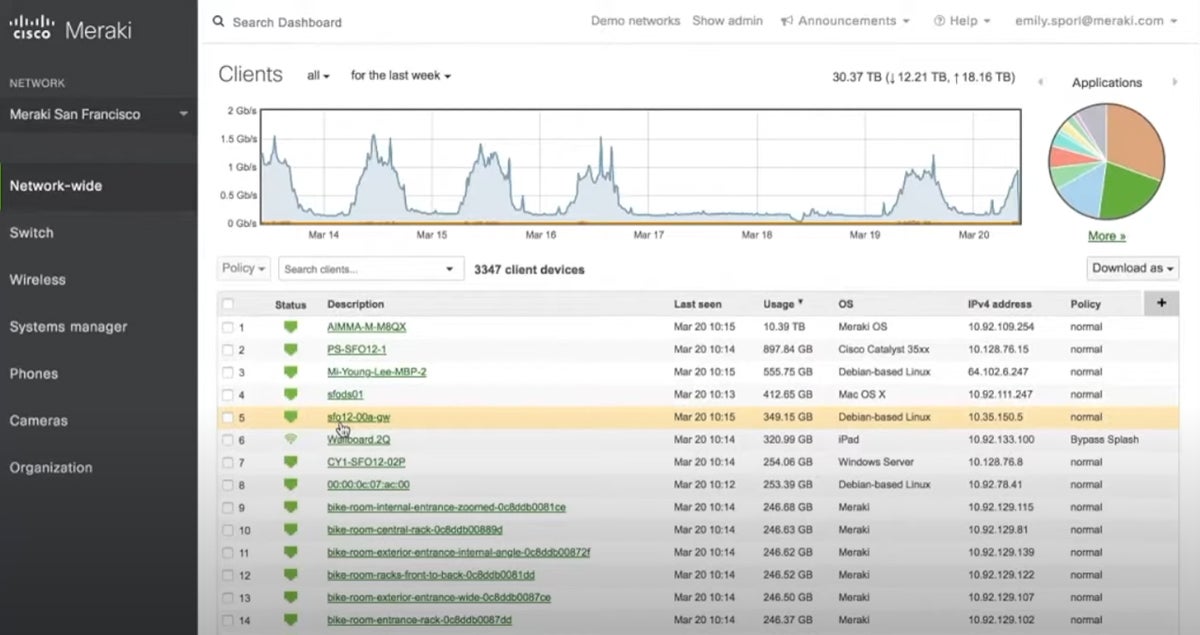
The Meraki dashboard displays complete network and application data, making it easier for IT teams to monitor and manage the network remotely. It has a simple and straightforward UI that streamlines network administration tasks. It allows you to track all Meraki products in a single, consolidated dashboard.
Recent product development:
Cisco Meraki introduced its Colorblind Assist Mode, adjusting the dashboard colors to make it easier for customers who are colorblind or have low vision issues to view information at a glance. It also has updates for remote network traffic analysis flow improvement and network security enhancement.
We chose the Cisco Meraki MX series for its extensive features and accessibility. These features include application layer filtering, customizable security policies, and advanced logging and reporting capabilities, all of which cater to a wide range of network requirements. The Meraki MX series’ cloud-based platform further enhances accessibility, enabling your distributed workforce to securely access a reliable connection to your corporate resources from any location.
| Pros | Cons |
|---|---|
| User-friendly. | Limited pricing details. |
| Cloud-managed IT enhances scalability, flexibility, and control. | Logging capabilities need improvement. |
| Unified Threat Management (UTM) and SD-WAN solution. | Occasional system slowness. |
Cisco Meraki has a product catalog with pricing details on hardware appliances and estimates. For full pricing information, contact their sales team.

Best for hybrid cloud environments
FortiGate, a high-performance firewall and network security platform, forms the backbone of Security Fabric, Fortinet’s solution for multi-cloud security. It provides a vast array of security and networking capabilities, such as comprehensive stateful inspection, packet filtering, DPI, and intrusion detection and prevention systems (IDPS). Additionally, it offers application layer filtering, antivirus and antimalware protection, and web content filtering, among other features.
FortiGate is a good fit for hybrid cloud environments as it has solid security features that can protect the communication between on-premises and cloud-based resources. It also supports various deployment modes, including an extensive selection of hardware appliances, virtual appliances, and cloud-native instances. In addition, this NGFW brings dynamic micro- and macro-segmentation to prevent the lateral spread of malware, which is particularly imperative in hybrid environments.
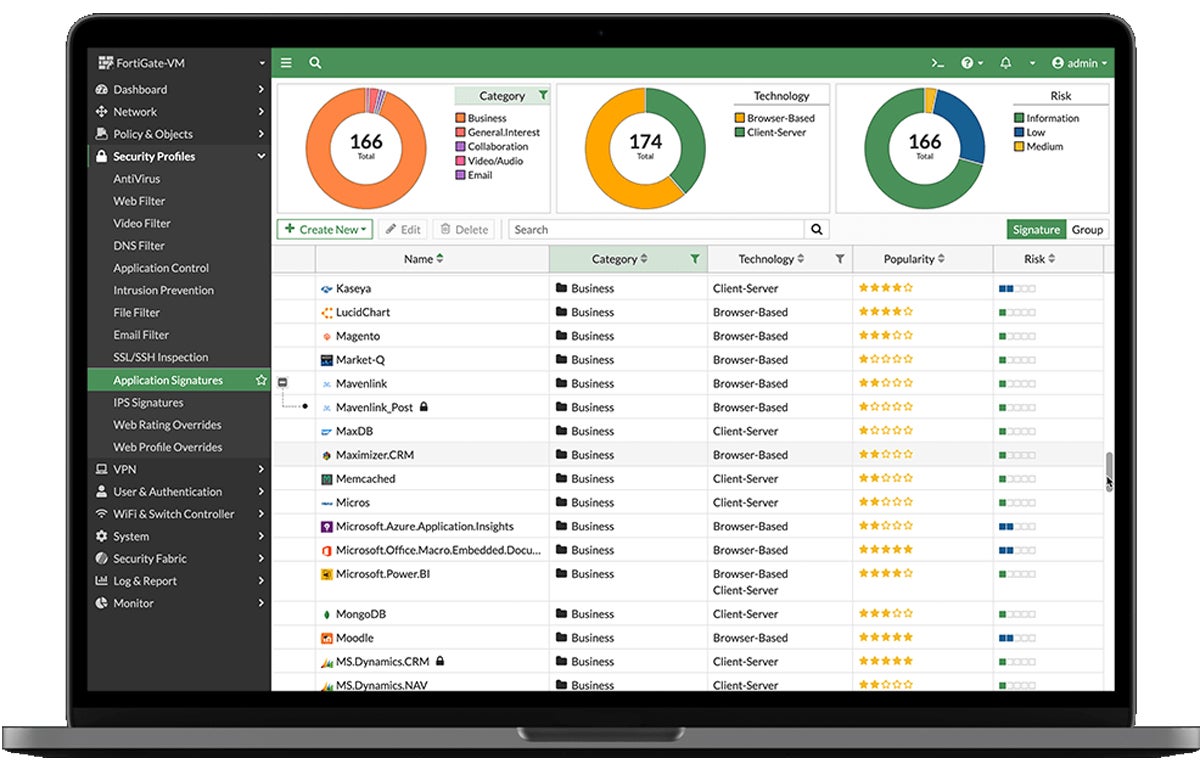
FortiGate has a user-friendly and clear UI design that gives an overview of everything from your network to logs and reports. It also has charts that help you understand risks at a glance and controls that allow you to sort data the way you prefer.
Recent product development:
Fortinet’s strategic expansion with Digital Realty, a global leader in data center, colocation, and interconnection services, marks a significant step forward in its commitment to providing robust and scalable security solutions. This partnership enhances Fortinet’s ability to deliver its Universal Security Architecture (USG) across Digital Realty’s extensive network of data centers worldwide. This means that as a Fortinet customer, you can scale your security infrastructure for optimal protection regardless of your organization’s size.
We chose Fortinet FortiGate for its ability to simplify management processes without sacrificing efficiency. It provides centralized control and visibility into suspicious activities, anomalies, and advanced threats. Moreover, its SSL-inspection feature does not slow down network speed, eliminating compromise between security and performance.
| Pros | Cons |
|---|---|
| Web filtering uses a database of hundreds of millions of URLs classified into over 90 categories to enhance granular web controls. | Lacks transparent pricing. |
| Antivirus includes signature-based detection, heuristic and behavior-based detection, and AI- and ML-driven analysis. | Logging needs more details. |
| Has a rich set of tools to centrally manage 100,000+ devices from a single console with advanced visibility. | Customer support takes a long time to respond. |
Fortinet doesn’t show pricing information for FortiGate. Contact their sales team for complete pricing information.

Best for multi-cloud environments
Zscaler Cloud Firewall is a cloud-based solution that forms an integral part of the Zscaler Zero Trust Exchange. It offers comprehensive security for users, data, and devices, providing real-time visibility and control over network traffic. This firewall supports granular control, allowing centralized policy management for all users and traffic. It also integrates seamlessly with other Zscaler services for a unified security approach.
Zscaler Cloud Firewall’s architecture promotes scalability and ease of management. It lets you protect users, data, and devices no matter where they are. This makes it particularly suitable for multi-cloud environments, where traditional hardware firewalls may struggle to deliver consistent protection across diverse platforms and locations.
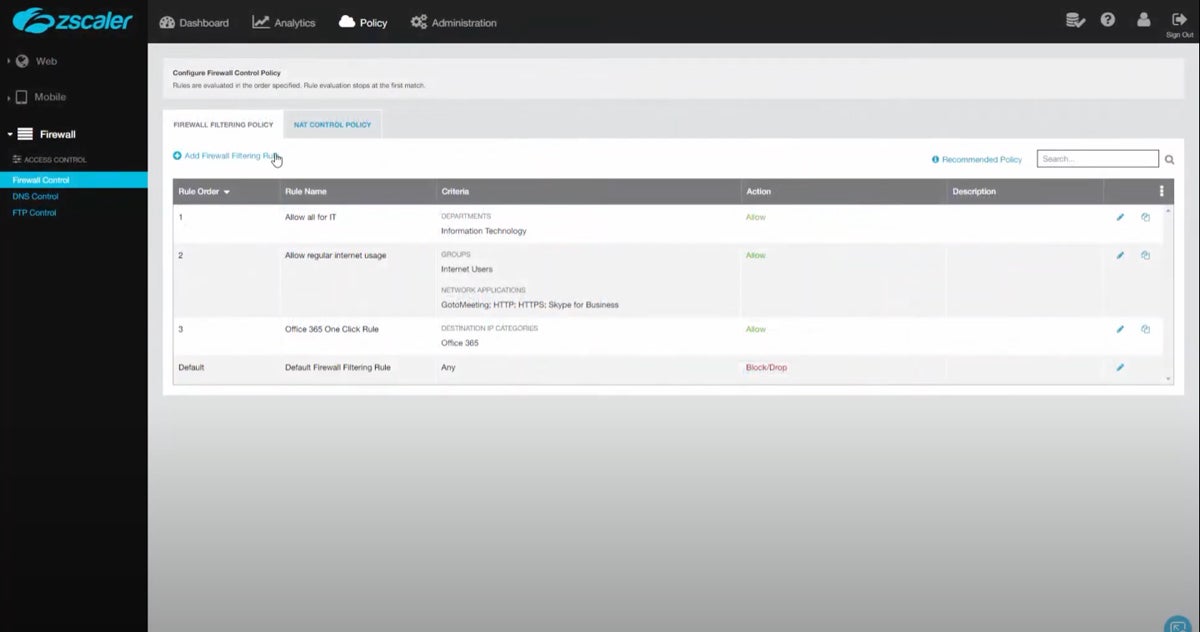
With a minimalistic and modern design, Zscaler’s UI facilitates quick access to key features, such as rule configurations, analytics, and firewall controls. The logical organization of menus and the use of visual elements contribute to a seamless user experience, making it accessible for admins to implement firewall policies effortlessly.
Recent product development:
In November 2023, Zscaler unveiled major updates to its Zero Trust Exchange platform to bolster cloud workload security. Notable features include the ability to create custom security groups on AWS through user-defined tags, real-time resource discovery, and multi-session VDI security inspection for public cloud deployments. Additionally, Zscaler expands its cloud coverage to include Google Cloud Platform, Azure China Regions, and AWS GovCloud with FedRAMP certification, expanding its solutions across major public cloud providers.
We picked Zscaler Cloud Firewall because its cloud-first approach enables scalability and centralized management for consistent security policies across multi-cloud deployments, which is especially important today, where remote work continues to grow.
| Pros | Cons |
|---|---|
| Long free trial duration of 90 days. | Lacks transparent pricing. |
| Advanced centralized management tools. | Complex deployment. |
| Global coverage improves connection speed and reliability. | False positives. |
According to Zscaler’s pricing page, its firewall solution is included in Transformation and Unlimited plans in Zscaler for Users Editions and Zscaler Internet Access (ZIA) Editions. However, it doesn’t publish actual pricing information on their page. Get in touch with their sales team to learn more.
Core features of an SMB firewall includes stateful inspection and packet filtering, intrusion detection and prevention, VPN support, application layer filtering, and logging and reporting.
Stateful inspection and packet filtering are crucial to a firewall as they form the first line of defense in network security, making sure that only safe and necessary traffic gets through. This not only protects the network and its data, but also optimizes network performance by eliminating unwanted traffic.
Stateful inspection actively scrutinizes the context of ongoing connections and permits or restricts traffic flow depending on the connection’s state. On the other hand, packet filtering evaluates individual packets against a set of predefined rules. It ensures that only legitimate connections are established and minimizes the chances of unauthorized access to sensitive business data.
Intrusion detection and prevention system (IDPS) monitors network or system activities for suspicious behavior or known attack patterns. It strengthens the firewall’s effectiveness by offering an additional layer of security that goes beyond basic access control. IDPS actively mitigates detected threats and provides real-time prevention, decreasing the risk of data breaches and protecting the integrity of business operations.
Good virtual private network (VPN) support enables secure communication over the internet by encrypting data transmissions between connected devices. This firewall feature is vital for safeguarding remote access, protecting confidential business communications, and guaranteeing the privacy of sensitive data.
Application layer filtering examines data at the application layer of the OSI model. It controls application usage, mitigating risks from unauthorized or non-business-critical applications, and maintains network efficiency. This feature not only boosts security, but also optimizes network performance, reduces potential cyberthreats, and supports efficient network resource utilization.
The firewall’s logging and reporting feature records network activities and generates detailed reports so network administrators can monitor traffic, spot patterns, detect anomalies, and troubleshoot issues. This feature gives visibility into network activities, aids in identifying and mitigating security threats promptly, and presents compliance evidence, thereby maximizing the firewall’s effectiveness.
To ensure a data-driven evaluation for this best small business firewall review, we meticulously compared and scrutinized different SMB firewall solutions. Five major criteria make up our assessment. These include cost, core features, customer support, integrations, and ease of use.
We measured each firewall provider’s performance against each of these criteria and scored them based on their effectiveness. We then aggregated the scores for each SMB firewall software provider.
To compute the scores for this criteria, we considered each company’s pricing model, transparency, and the availability of a free trial, as well as its duration. We favored free trials over money-back guarantees, as they usually allow potential buyers to test the service without making any initial payments.
Criteria winner: pfSense
For core features, we examined the range of features each SMB firewall offered as a built-in capability. We measured features such as stateful inspection and packet filtering, IDPS, VPN support, application layer filtering, web content filtering, antivirus and malware protection, logging and reporting, centralized management, customizable security policies, and user authentication and access control. We took the extensiveness of hardware appliance selection into consideration, if applicable.
Criteria winners: Perimeter 81, Palo Alto Networks, Fortinet FortiGate, and Zscaler Cloud Firewall.
We factored in the availability of live chat, phone, and email support, active community, and in-depth documentation or knowledge base to all users across all payment tiers to calculate the scores for customer support. We also considered customer support knowledge and response times.
Criteria winner: Sophos XGS
For integrations, we assessed the number of third-party integrations each SMB firewall directly integrates with. We primarily focused on relevant solutions, like identity providers, SIEM systems, authentication systems, cloud services, endpoint security solutions, and VPN solutions. We also checked if the firewall integrates with threat intelligence feeds and supports custom integrations.
Criteria winner: Fortinet FortiGate
To determine scores for this criteria, we considered the ease of deployment and management of the SMB firewall solutions for users of different technical skill levels.
Criteria winners: Perimeter 81, SonicWall TZ Series, Cisco Meraki MX, and Fortinet FortiGate
Choosing between a cloud firewall and a traditional firewall for small business enterprises isn’t a straightforward decision. It depends on several factors, like your business needs, budget, IT resources, and work setup. Here’s a quick comparison to give you an idea:
| Cloud firewalls/FWaaS | Traditional firewalls | |
|---|---|---|
| Best for | Businesses with limited IT resources or with remote/mobile workers. | Businesses with specific compliance requirements or on-premise network environments. |
| Pros | • Typically easier to scale. • Automatic updates and patches from service providers. | • Provides control and a strong line of defense. • Often more customizable. |
| Cons | • Dependent on internet connectivity. • Ongoing costs. | • Upfront hardware costs. • Requires hands-on management. |
In some cases, a combination of both or a hybrid approach might be the best option. It’s important to evaluate your specific situation and consult with a cybersecurity expert before making a decision.
There are many different types of SMB firewalls, like UTM firewalls, NGFWs, software firewalls, hardware firewalls, and cloud-based firewalls or FWaaS:
To choose the best firewall for small business ventures, you must consider several factors, including your enterprise needs, the structure of your business, available IT resources, and your budget. Finding the right firewall for your organization can help you take proactive measures to safeguard your growing business from potential threats and maintain the trust and confidence of your customers.
We have created this best small business firewall review to guide you in making the right decision. It will provide you with sufficient information to determine which SMB firewall is most compatible with your organization.
With a firewall in place, don’t neglect supporting documentation! Read our quick guide to establishing a firewall policy for your organization, complete with free, downloadable template.
Liz Laurente-Ticong is a tech specialist and multi-niche writer with a decade of experience covering software and technology topics and news. Her work has appeared in TechnologyAdvice.com as well as ghostwritten for a variety of international clients. When not writing, you can find Liz reading and watching historical and investigative documentaries. She is based in the Philippines.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.