

Image: Chor muang/Adobe Stock
Network vulnerability assessments allow security professionals to see the state of the network’s vulnerability exposure and allows them to take action.
Network vulnerability assessment (NVA) is a process that identifies and assesses security flaws in a network’s publicly accessible devices. It also provides mitigation strategies to address these vulnerabilities and reduce the risk of security breaches.
A vulnerability assessment is important because it enables you to discover and fix security vulnerabilities before attackers can exploit them. It can protect your organization from data theft, system disruptions, and other security incidents.
Security professionals conduct regular vulnerability assessments because new vulnerabilities occur constantly. These assessments provide valuable information for developing plans to mitigate identified risks.
Network vulnerability assessments look for potential threats and weaknesses across applications and IT infrastructure to strengthen network security. These specialized tools probe unpatched software and operating systems, open ports and services, unsecured wireless networks, misconfigurations in web or network applications, network architecture weak points, security policy compliance, mobile device vulnerabilities, access control and permissions, physical security issues, exposed (Internet of Things) IoT devices, weak passwords, and application-level vulnerabilities:
There are many different types of vulnerability assessments that you can conduct to discover and evaluate the security risks and weaknesses in your systems, networks, and applications. Below is a comparison showing various vulnerability assessment types and their key differences:
| Vulnerability assessment type | Key differences |
|---|---|
| Network vulnerability assessment | • For computer networks, including open ports, misconfigurations, and software vulnerabilities. • Can be external or internal in scope. |
| Host vulnerability assessment | • For individual devices (e.g., servers, workstations) to uncover vulnerabilities in their operating systems, software, and configurations. • Not network-wide. |
| Web application vulnerability assessment | • For web applications online services. • Discovers SQLi, XSS, and security misconfigurations. • Focused on web-specific issues. |
| Database vulnerability assessment | • For database systems, focusing on configurations, access controls, and data leakage risks. • Specific to database-related vulnerabilities. |
| Wireless network vulnerability assessment | • For wireless networks, identifying vulnerabilities in encryption, authentication, and access controls. • Focused on Wi-Fi and related technologies. |
| Cloud vulnerability assessment | • For cloud environments, assessing vulnerabilities specific to cloud services, configurations, and permissions. |
| Physical security assessment | • For physical security measures, access controls, surveillance systems, and policies. • Focused on preventing unauthorized physical access to facilities. • Not for digital security. |
| Social engineering assessment | • Concentrates on social engineering attacks or human-related vulnerabilities, such as phishing or pretexting. |
| IoT vulnerability assessment | • For IoT-specific vulnerabilities like weak passwords, insufficient data protection, and poor IoT device management. |
| Compliance and regulatory assessment | • For compliance with industry regulations or standards (e.g., PCI DSS, HIPAA, GDPR). |
Numerous vulnerability assessment solutions in the market can perform these vulnerability assessments effectively.
There are two major categories of vulnerability assessment platforms: multi-faceted and focused.
There are six essential steps in the vulnerability assessment process: planning and designing, asset discovery, configuration, network scanning, result analysis, vulnerability prioritization, and report generation.
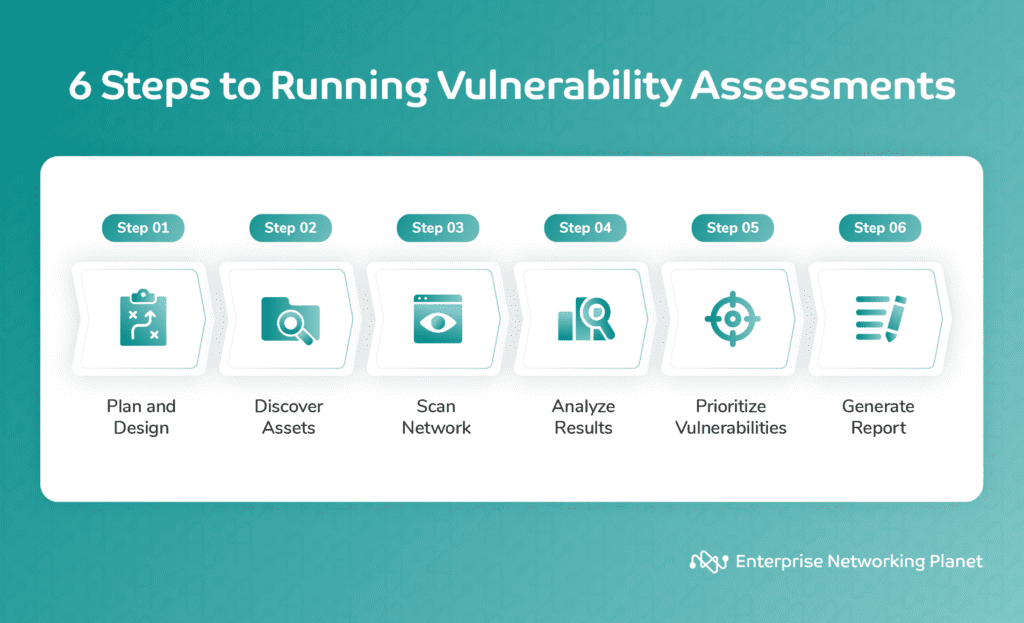
To begin a network vulnerability assessment, you must first determine the scope and exact components for assessment. This includes hardware, user devices, applications, and network infrastructure.
After establishing the scope, identify assets and set baselines for their individual security capabilities, risk tolerance, user permissions, configuration, and other factors.
Finally, set up the test environment, gather any necessary tools and resources, and complete any further planning and preparation.
The next step is deciding what you want to scan. This can include Bring Your Own Device (BYOD) mobile devices or IoT devices. Then, specify the network components for the assessment, such as devices, applications, hardware, and network infrastructure. You must identify these assets and set baselines for their security capabilities, risk tolerance, user permissions, configuration, and other factors.
Network scanning involves checking your network for security vulnerabilities. You can use a vulnerability scanner to spot potential security risks in your network.
After scanning, you’ll have to analyze any flagged concerns to pinpoint possible vulnerabilities.
Then you can assess and score the newly-discovered vulnerabilities based on their associated risk.
Finally, create a comprehensive report detailing the findings from the assessment. The report should also include information on actions taken and recommendations for future assessments.
A network vulnerability checklist is a must-have for conducting a network vulnerability assessment. It lets you plan and organize your assessment activities, ensuring completeness and accuracy. The checklist also enables you to follow best practices and standards of network security, boosting your assessment efficiency.
Keep in mind that there is no one-size-fits-all answer to what should exactly be on a network vulnerability checklist, as different organizations have varied network security needs and goals.
Some common items that the checklist typically includes are asset identification, scope definition, scan configuration, scan execution, result analysis, risk evaluation, remediation plan, implementation of fixes, network vulnerability assessment process update, and repetitive testing.
To identify assets, you need to discover and document network assets, including devices, systems, applications, and data. This involves enumerating all network components, devices, systems, and software, by making a list of everything that makes up your network.
Determine the network extent that you will evaluate by specifying the systems and components, such as servers, routers, firewalls, and switches for evaluation. You also need to set the parameters and constraints like the time frame, budget, and resources.
Prepare for scanning activities by configuring your vulnerability scanning tool with the target IP addresses. Select appropriate tools and methods for the network. Additionally, document the plan and seek approval from stakeholders as part of the setup process.
Initiate the vulnerability scan on the defined targets to detect known threats and vulnerabilities within the network. Run scans using selected tools and methods, and evaluate the functionality and performance of network security controls such as antivirus, firewall, email filters, and DDoS protection.
Evaluate the scan results and explain the findings using facts and evidence to support your conclusions. You must also validate the results, removing any false positives or negatives that might skew your analysis.
You need to rank vulnerabilities based on how severe, impactful, and exploitable they are. You can use this information to create and execute a mitigation plan, as well as to revise and refine the network vulnerability assessment process.
You must create a mitigation plan to address the identified vulnerabilities. Document the remediation actions for each vulnerability, such as patching, updating, configuring, or replacing the affected systems or components. You must also obtain approval from the stakeholders for the mitigation plan.
Execute the remediation actions outlined in the plan, including applying patches, updates, or other fixes. Monitor and test the effectiveness of these actions, ensuring they don’t introduce new vulnerabilities or issues. The goal of these fixes is to resolve or reduce vulnerabilities and enhance network security.
After conducting the assessment, document the outcomes and lessons learned. Additionally, update and adjust the network vulnerability assessment process using feedback and best practices. Thoroughly document the network vulnerability assessment process, covering all activities from start to finish, along with the discovered threats and the methods for mitigating them. This documentation is of utmost importance.
It is vital to constantly review and analyze systems to discover new threats and attacks and take all possible steps to mitigate them.
The cost of a network vulnerability assessment can vary drastically depending on the tools used, the size and skill of your IT department, and the size and complexity of your network. According to some sources, the average cost of a network vulnerability assessment is between $4,000 and $5,000.
It’s worth noting that there are many open-source vulnerability assessment tools available today. These tools are typically free to use, which means you could potentially conduct a vulnerability assessment at little to no cost.
Keep in mind that while the tool itself may be free, proficiently using it often requires a certain level of expertise. Therefore, there may still be costs associated with training or hiring a professional to use these tools optimally.
The actual network vulnerability assessment cost can vary depending on several factors, like your network’s scope and complexity, your organization’s size and scale, the type of vulnerability scanning tools, your report’s comprehensiveness, support quality for remediation, and assessment frequency.
Carrying out regular network vulnerability assessments can bring many benefits to your organization, such as risk mitigation, cost savings, better patch management, optimized resource allocation, and continuous improvement.
Your organization can proactively manage and mitigate risks by uncovering vulnerabilities, effectively reducing the likelihood and impact of cyberattacks. This approach allows you to address potential security threats before hackers or bad insiders can manipulate them, thereby stopping cyberattacks before they occur.
You can save your organization significant financial resources and avoid spending on incident response, recovery, and legal costs by preventing data breaches, downtime, and other cyber incidents through vulnerability assessments.
Regular vulnerability assessments can aid organizations in promptly addressing known vulnerabilities by finding outdated software and configurations that require patching or updating. As a result, your organization can maintain a more secure environment by addressing known vulnerabilities promptly.
You can decide where to best allocate your security resources by conducting vulnerability assessments. This ensures that time and budget are spent on areas of greatest need, increasing the efficiency of security efforts.
Network vulnerability assessments are ongoing processes, not one-time activities. Regular assessments promote a culture of continuous improvement in cybersecurity, allowing organizations to adapt to evolving threats and technologies.
Some people use the terms penetration testing (or pentesting) and vulnerability assessment interchangeably, but there are critical differences between the two approaches.
Pentesting is a security practice where ethical hackers simulate real-world attacks to find vulnerabilities in computer systems, networks, and applications. The goal is to assess security controls and discover potential entry points for malicious actors.
Vulnerability assessment is a list-based, automated, and high-level process that scans the system for potential vulnerabilities and reports them without attempting to exploit them.
Here are the key distinctions between pentesting and vulnerability assessment:
| Penetration testing | Vulnerability assessment |
|---|---|
| Actively exploits vulnerabilities. | Identifies vulnerabilities but does not exploit them. |
| Narrower in scope. | Broader in scope. |
| Simulates real-world attacks. | Primarily focuses on scanning and discovery. |
| Conducted periodically. | Conducted regularly. |
| Requires skilled ethical hackers. | Can be performed by security analysts. |
| Provides detailed exploitation reports. | Generates lists of identified vulnerabilities. |
| Emphasizes real-world risks. | Prioritizes vulnerabilities based on severity. |
| Less frequent. | More frequent. |
| Higher cost and resources. | Lower cost and resources. |
| Often required for compliance. | Contributes to compliance but not its primary focus. |
Network vulnerability assessments are a critical part of a comprehensive vulnerability management strategy and any organization’s security posture. By identifying and addressing vulnerabilities, you can protect your organization from a wide range of attacks. There are a number of different ways to conduct a network vulnerability assessment, and the best approach will vary depending on the specific needs of your organization.
Assessing networks for vulnerabilities and taking steps to address them enables you to stay one step ahead of the attackers and helps you to fix any security issues before they become serious problems. Ultimately, network vulnerability assessments empower you to elevate your network’s performance and reliability.
Boost your vulnerability assessment practices and fortify your network security using one of the top vulnerability management tools.
Liz Laurente-Ticong is a tech specialist and multi-niche writer with a decade of experience covering software and technology topics and news. Her work has appeared in TechnologyAdvice.com as well as ghostwritten for a variety of international clients. When not writing, you can find Liz reading and watching historical and investigative documentaries. She is based in the Philippines.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.