Network segmentation involves splitting a large network into multiple smaller ones to improve security, management, and performance. These network segments not only reduce congestion and improve traffic flow, but also provide a failsafe against intruders, who are limited to the segment they attacked rather than the entire organization.
Thanks to these features, network segmentation is an increasingly popular technique to give network managers more control over network traffic.
However, it can be overwhelming to figure out where to start. Here are the basics of network segmentation, from its prime use cases to specific tools and techniques to build your strategy.
Why is network segmentation needed?
You might want to employ network segmentation for several reasons, from improved functionality to heightened security. The most common is customized cybersecurity for different parts of a single network.
Network segmentation provides more precise control over how traffic flows and cybersecurity are managed. This can result in a much more secure, well-organized system that performs better for individual users.
People may also want to use network segmentation for greater privacy. You can do this on your home, office, or small business system with a basic router’s guest feature.
Network segmentation is needed whenever you want to create separate space in one larger system, whether for organization, privacy, or security.
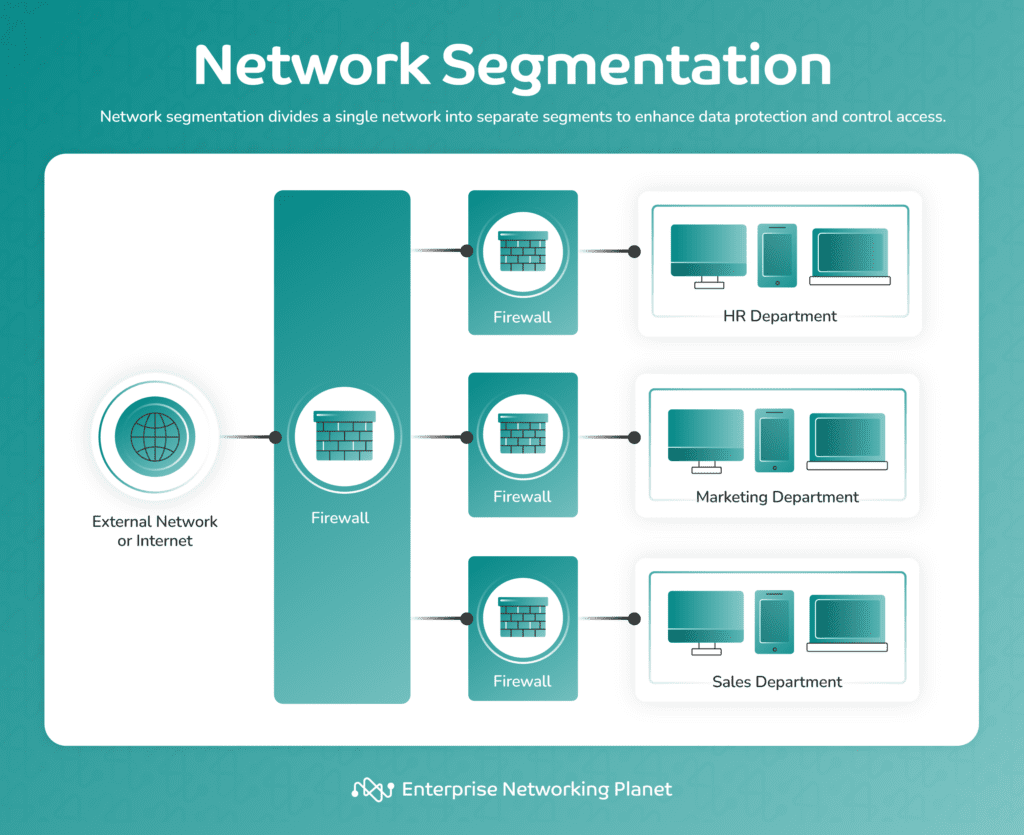
How network segmentation works
Network segmentation involves splitting a network into separate, isolated sections physically or virtually. It can be as simple as creating a guest network on a home Wi-Fi router. The process is more complicated for large organizations with large amounts of data and traffic.
Regardless of the scale involved, network segmentation generally works the same way. Additional barriers are added to limit movement and access. Users on a guest network can’t see activity on a corresponding private network and vice versa.
Each segment can have its own security protocols so higher-risk data gets more advanced protection, while low-risk information is still conveniently easy to access. Network segmentation isolates vulnerable data without impeding the system’s everyday functionality, striking a balance between security and usability.
5 steps to network segmentation
On a technical level, the process of segmenting a network varies significantly depending on the specific technology used. However, a few vital steps apply regardless of your chosen technology.
1. Map data and traffic
The first step is mapping data and traffic in the network as it currently operates. Mapping how users access information and move through your network provides a better understanding of how many segments you need and the best way to secure them.
This can be a time-consuming task, but it’s crucial for success. Fortunately, there are some excellent network mapping tools that can help you simplify the process.
2. Determine security needs
One of the best benefits of network segmentation is the ability to customize your cybersecurity protocols for different data types. Security is rarely one-size-fits-all. Using high-level protections on everything makes your system difficult to navigate for many users, while undersecuring it leaves high-risk data vulnerable.
Separate your data into groups based on risk. Determine what level of cybersecurity would be best for each type by analyzing sensitivity and how often users access it.
3. Organize segments by risk level
Use the risk-based groups to outline your network segments. Put together groups of data with similar security and accessibility needs.
For example, you’ll probably notice users access certain types significantly more than others. Everyday data, such as a customer service website or employee directory, is often low risk and requested frequently. It should go in a low-risk network segment with minimal protections so it’s convenient for users to access.
In contrast, sensitive data like customers’ financial information is too vulnerable to be exposed in a low-security segment. It should go in a separate area with high-level protection and encryption.
4. Implement segmentation
It’s time to put your network segmentation outline into action. The process for accomplishing this depends on what technology you use. Leave plenty of time to install or integrate your segmentation technology and test it afterward to ensure everything operates correctly.
5. Monitor segment security
Successful cybersecurity is all about visibility, transparency, and continuous improvement. You must carefully monitor your network after segmenting it.
Monitoring is a core part of today’s leading cybersecurity frameworks, such as the National Institute of Standards and Technology (NIST). This security model emphasizes the importance of threat detection through continuous monitoring to ensure the highest level of security.
This is vital for ensuring your segments remain secure and keeping you aware of optimization opportunities and vulnerabilities. For instance, you might notice that a certain type of data needs stronger or less security.
3 benefits of network segmentation
Network segmentation requires time and resources, so it’s worth understanding why it’s necessary. There are several benefits, whether you have a simple small-business network or an entire data center.
1. Increased network security
Improved cybersecurity is the top benefit of network segmentation. It lets you customize security protocols with a high level of precision. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recommends using network segmentation to achieve the highest possible level of cybersecurity.
Customizing unique security “zones” within your network is invaluable. It can even save your data in the event of a cyberattack. Hackers that break into a segmented network are trapped in one segment. As a result, the potential damage is significantly reduced and confined to a limited subset, rather than the entire network.
2. Improved visibility
Network segmentation requires carefully mapping your data and traffic so administrators have a clearer picture of operations. It makes it easier to track which information users are accessing.
These processes improve network visibility, which is vital for ensuring effective security. Having a clear view of user traffic and understanding exactly how your system functions makes you better equipped to notice suspicious activity immediately.
3. Better user experience
Network segmentation can positively impact the user experience if implemented properly. This too can affect network security.
Surveys show at least 68% of internet users recycle the same password across multiple accounts. The most common reason for this behavior is inconvenience. Users are more likely to employ strong security measures when they are convenient to use, such as by using a password manager.
People will have a poor experience with your network if they must use the highest level of security possible. Network segmentation resolves this by allowing you to protect sensitive data while leaving customer-facing content easily accessible.
Network segmentation vs. microsegmentation
Microsegmentation applies network segmentation on a small scale with specific areas for individual apps, devices, or users. You can employ it within a larger framework.
For instance, you might need to run a certain app in a network segment that requires high accessibility and minimal protection. You can create a microsegment to give the application extra security compared to the larger area that it’s in.
Types of network segmentation
A network segmentation strategy will lean one of two ways: physical or logical. Physical segmentation primarily relies on dividing a network using hardware, whereas logical segmentation utilizes virtual methods like software and security protocols.
1. Physical segmentation
You can physically segment a network by separating data and apps onto different servers. Firewalls are also effective for physical segmentation.
This is the simplest type of network segmentation for many users, and also the most secure, since there is no chance of crossover for cyberattackers.
The most complicated part is ensuring your different server stacks aren’t interconnected. The main drawback of purely physical segmentation is that you can end up with a heavily siloed system, making it highly inconvenient for employees who need to access information across segments.
2. Logical segmentation
Logical segmentation is much more varied than physical segmentation. It can involve various technologies, including local area networks (LANs), virtual machines, hypervisors, microsegmentation, and cybersecurity protocols.
Logical network segmentation can be more complex to set up but offers more flexibility, versatility, and customization than purely physical segmentation. Most strategies employ a combination of both.
Tools used in network segmentation
Depending on your approach to network segmentation, you may use different tools, but the most common include hypervisors and other virtualization tools, access control lists (ACLs), and firewalls.
Firewalls
Firewalls are the bread and butter of network segmentation. They’re one of the foundational tools most strategies employ.
Firewalls are effective and versatile. You can place them between layers and segments to create a highly fortified network. They also let you create customized access filters from one layer to another.
Start with firewalls if you’re completely new to network segmentation. IT professionals will already be familiar with them, and they’re relatively easy to set up. Individuals can use them to segment their home or office network. Most consumer routers offer basic options and let you create a guest network with its own firewall and access rules.
Access control lists (ACLs)
ACLs, also known as allow lists, are a basic tool for identity and access management. They allow you to specify who can access different parts of your network. You define rulesets and approved users, and your network uses these to automatically enable or reject traffic.
ACLs are straightforward and highly effective. They’re a great place to start if you want to create segments based on user-specific access or one that’s only accessible to a few users, such as administrators.
Hypervisors, virtual networks and VLANs
Hypervisors, virtual networks, and virtual local area networks (VLANs) are a few of the top technologies for logical network segmentation. They involve virtually creating segments on shared physical servers.
Virtual networks and VLANs are software-defined networking technologies. They use overlays to virtually create segments at different layers of the network.
VLANs operate at the Ethernet layer. Traffic passes through the router, a network switch, and into one of numerous isolated VLANs. This creates a virtual network where traffic and data can be isolated within a shared server infrastructure.
Hypervisors are more commonly utilized to create private servers in cloud computing, but they can also be applied to network segmentation. A hypervisor is essentially a network overlay that creates virtual machines within shared computing infrastructure.
One crucial difference between hypervisors and VLANs is that hypervisors divide the computing resources. Each virtual machine is effectively its own computing environment that doesn’t share resources with others. This helps ensure every segment or virtual machine has the computing resources it needs.
Bottom line: Network segmentation for everyone
Network segmentation is an increasingly vital part of modern cybersecurity. It’s a versatile and robust way to create customized layers of security and maximize protection for vulnerable data. It’s also highly scalable, so anyone can utilize it.
Adopting network segmentation enables you to create a well-organized network fortified to defend sensitive data without compromising performance and accessibility.
Get started on segmenting your own network with one of the best network segmentation tools, designed to simplify the process for IT professionals at all experience levels.


