
Image: kras99/Adobe Stock
Network vulnerability scanning allows security teams to identify weak points in networks before they are exploited by attackers. Here’s how it works.
Network vulnerability scanning is the cybersecurity practice of systematically identifying and assessing potential security weaknesses within a computer network. It uses automated tools to find potential areas of risk across your organization’s networks and systems before an attacker does, protecting these systems as well as data.
This process is a crucial part of managing network security. Once network vulnerability scanners find vulnerabilities, network admins can then take steps to fix them, bolstering network defense.
Network vulnerability scanning tools empower organizations to proactively reduce the risk of data breaches, service disruptions, and unauthorized access. Additionally, network vulnerability scanning software enables organizations to comply with regulatory requirements, gain insights into their security posture, and allocate resources effectively.
The network vulnerability scanning process may also incorporate manual testing in certain cases to uncover complex or non-standard vulnerabilities. Regular scanning aids organizations in maintaining a strong security posture, adapting to evolving threats, and keeping up with software updates.
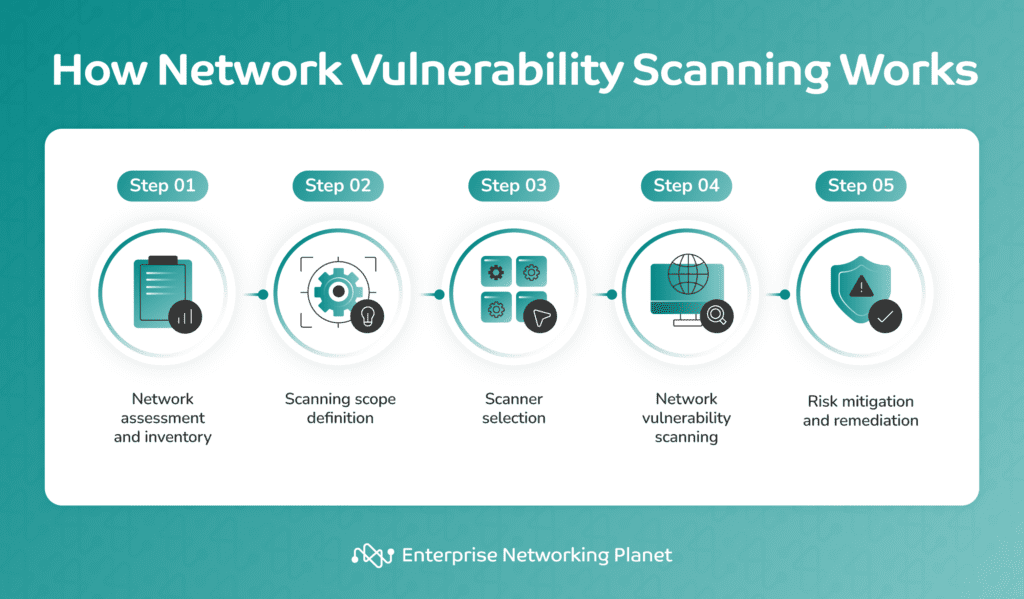
Network vulnerability scanning is a structured procedure that begins with network assessment and discovery, followed by scanning scope definition, scanner selection, and culminates in the identification and mitigation of network vulnerabilities.
The process starts by identifying and cataloging all devices and systems connected to your network. This inventory includes servers, workstations, routers, firewalls, and other network components.
Defining the scope involves determining which assets and services to include in your scan and deciding whether the IT team will conduct the scanning process internally or externally.
Once you define the scope, you must choose an appropriate vulnerability scanning tool or software. This tool should align with the defined scope and have an updated database of known vulnerabilities.
After selecting a scanner, the actual scanning process begins. The network vulnerability scanning tool methodically checks the network assets within the defined scope for known vulnerabilities. It does this by sending test requests and analyzing responses from network assets to pinpoint potential security weaknesses.
Following the scanning phase, network admins or security professionals review the results thoroughly and categorize vulnerabilities based on their severity. This categorization — which often includes labels like critical, high, medium, or low risk — guides subsequent actions.
Your organization can then implement measures to mitigate and remediate the identified vulnerabilities. This may entail applying security patches or reconfiguring systems to reinforce security measures and reduce the risk of unauthorized access or security breaches.
Network scans typically identify vulnerabilities like outdated software, weak passwords, unpatched security, open ports, misconfigured security settings, missing security updates, weak encryption, insecure services and protocols, vulnerable third party components, and denial of service (DoS) vulnerabilities.
To conduct a vulnerability scan on your network, you need to define your scope, select a scanner, build a plan, initiate the scan, analyze the results, mitigate and remediate, regularly scan, and maintain proper documentation.
Clearly outline which network assets and services you want to assess in your vulnerability scan. Decide whether it’s an internal or external scan.
Choose a suitable vulnerability scanning tool that aligns with your defined scope and objectives.
Develop a plan specifying your scan objectives, schedule, and any specific requirements. Inform relevant teams about the plan.
Launch the scanning tool, configure it according to your scope, and initiate the network vulnerability scan to uncover known vulnerabilities.
Examine the scan results, categorize vulnerabilities by severity, and prioritize urgent ones for immediate action.
Take measures to address identified vulnerabilities, such as updating necessary systems, deploying patches, or fixing system configurations.
Schedule routine vulnerability scans to account for new vulnerabilities and maintain a strong security infrastructure.
Maintain records of scan results and actions taken. Furthermore, create reports detailing the vulnerabilities detected and the steps for mitigation.
There are various types of network vulnerability scanners for different purposes. These include web application scanners, authenticated scanners, passive scanners, continuous monitoring scanners, and cloud-based vulnerability scanners.
These are a subset of vulnerability scanners focusing on vulnerabilities specific to web applications rather than addressing vulnerabilities in the broader network.
This type of network vulnerability scanner specializes in assessing vulnerabilities that require authentication to access.
Passive scanners are a unique type of network vulnerability scanners that monitor network traffic passively but don’t actively scan for vulnerabilities.
These are network vulnerability scanners that zero in on continuous, ongoing scanning to identify changes and new vulnerabilities.
These mainly scan for vulnerabilities in cloud environments but may also encompass broader cloud security assessments.
There are several network vulnerability scanning methods, each designed to detect network weak points. These techniques include remote scanning. agent-based scanning, credential-based scanning, non-credential-based scanning, passive scanning, and active scanning.
This is the universal approach where a scanner sends packets to the target network from a remote location to identify vulnerabilities.
For this method, target devices have agents that constantly monitor and report vulnerabilities back to a central console.
Credential-based scanning employs tools that use valid usernames and passwords to access target systems for a more detailed assessment.
Cybersecurity professionals and ethical hackers commonly use this technique to scan for vulnerabilities without using login credentials or access privileges. This simulates how an unauthorized attacker might search for weaknesses in a system or network from an external standpoint, where access is limited to what’s publicly visible without authenticated entry.
This scanning approach involves the passive monitoring of network traffic to collect information about devices, software, and configurations without actively probing the target systems.
There are two different types of network vulnerability scanning approaches: external and internal vulnerability scans. This table provides a concise comparison between the two, highlighting their differences in scope, perspective, methodology, purpose, and primary focus.
| Aspect | External vulnerability scan | Internal vulnerability scan |
|---|---|---|
| Scope and target | Public-facing systems and services | Internal network and systems |
| Perspective | External (outsider’s perspective) | Internal (insider’s perspective) |
| Methodology | Port scanning, banner grabbing, vulnerability scanning | Network scanning, configuration assessment |
| Purpose | Identify external vulnerabilities, protect against external threats | Discover internal vulnerabilities, protect against insider threats |
| Primary focus | Protect external attack surface | Secure internal network assets |
Best practices for scanning networks for vulnerabilities include gaining proper authorization, keeping an updated inventory, using the right tools, segmenting and isolating systems, scanning regularly, performing credential-based scanning, prioritizing findings, and documenting and reporting results.
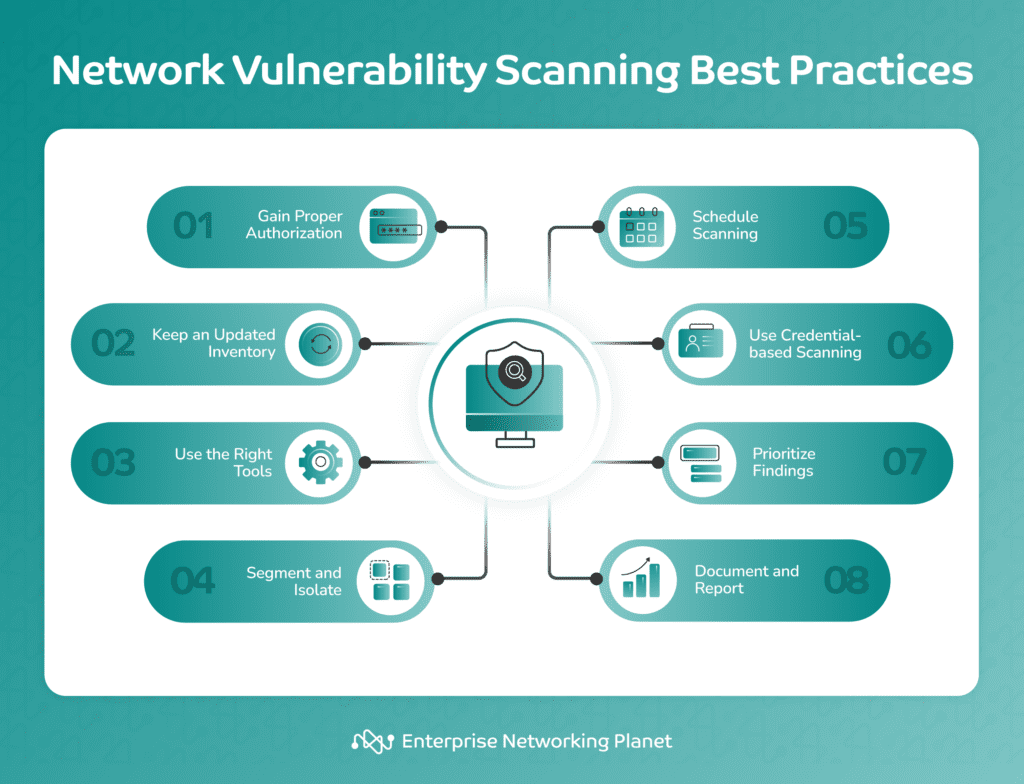
Always obtain explicit authorization from the network owner or administrator before conducting any vulnerability scans. Unauthorized scanning can lead to legal and security issues.
Maintain an up-to-date inventory of all devices, systems, and software on the network. This helps in understanding the scope and reduces the chances of missing vulnerabilities.
Choose a reliable and up-to-date network vulnerability scanning tool. You should regularly update these tools to incorporate the latest threat intelligence and vulnerability databases.
Isolate and segment critical systems from less critical ones. This reduces the attack surface and the potential harm during the scanning process.
Set up recurrent, scheduled scans rather than scanning haphazardly to ensure consistent network monitoring for vulnerabilities.
When possible, use credential-based scanning to gain deeper insights into the target systems and obtain a more accurate picture of vulnerabilities by accessing internal configurations.
Not all vulnerabilities are equally urgent. Implement a process for prioritizing and addressing vulnerabilities based on their severity and potential impact.
Keep a detailed documentation of the scanning process, including the results, remediation steps, and any changes made. Generate in-depth reports to communicate findings with relevant stakeholders.
There is a broad selection of network vulnerability scanning tools in the market today. Many of these tools come with rich features and capabilities that can help your organization assess and strengthen its cybersecurity posture. Here are a few of the best network vulnerability scanning tools in 2023:

Qualys VMDR is a powerful tool for managing vulnerabilities in complex IT environments, which can be challenging to secure. The platform stands out for its ability to give additional threat and risk context, helping to identify high-risk network vulnerabilities. This transparency in the rating algorithm facilitates prioritization and alignment among security and IT stakeholders, leading to swift risk remediation.
One key feature of Qualys VMDR is its integration of asset visibility with vulnerability management, offering organizations a clear view of their global assets. It equips enterprises with insight into cyber risk exposure, simplifying the prioritization of vulnerabilities, assets, or asset groups based on business risk.
However, Qualys VMDR requires technical expertise for optimal use. Nonetheless, it excels in providing threat context and asset monitoring, making it valuable for organizations aiming to fine-tune their cybersecurity posture.

ManageEngine Vulnerability Manager Plus scans and discovers exposed areas on all local and remote office endpoints, as well as roaming devices, to offer you a thorough 360-degree view of your security exposure. It is second to none in network vulnerability scanning and detects known or emerging vulnerabilities across workstations, laptops, servers, web servers, databases, virtual machines, and content management systems.
This solution combines vulnerability scanning, patch management, and security configuration management into one tool, unifying the detection and resolution of security risks from a central location.
However, ManageEngine Vulnerability Manager Plus does not auto-approve vulnerability patches, which means users must manually approve them. Additionally, immediate patch deployment in the system lets you select only up to 50 clients.
The strengths of ManageEngine Vulnerability Manager Plus greatly outweigh its minor weaknesses, establishing it as an invaluable asset in maintaining network security.

SolarWinds Network Vulnerability Detection, a component of the Network Configuration Manager, enables easy scanning of network devices’ firmware for reported Common Vulnerabilities and Exposures (CVEs), maintaining network security and compliance. Network automation is its main feature, allowing for quick deployment of firmware updates to network devices.
The tool effectively prevents unauthorized network configuration changes with its configuration change monitoring and alerting functionalities. Another notable strength is its capability to audit network routers and switches for policy compliance, consistently checking configurations for any non-compliant changes.
But like other network vulnerability scanning tools, SolarWinds Network Vulnerability Detection has weaknesses. For instance, its level of dashboard customization may not match that of some competitors, potentially affecting your ability to tailor the tool to your specific needs. In addition, the platform does not have a free version. Nevertheless, with its significant capabilities in network vulnerability scanning and management, it remains an excellent choice in the industry.
Network vulnerability scanning is an indispensable practice for defending your digital infrastructure. It’s a proactive, all-inclusive approach to detecting and addressing vulnerabilities, enabling continuous monitoring and compliance with regulatory standards. By adopting this process as an ongoing security measure and remaining vigilant, you can safeguard your network from potential threats and ensure its long-term security.
A network vulnerability scan is now a high-priority practice for maintaining strong security. It allows you to understand vulnerabilities, prioritize them based on risk, and take the necessary steps to remediate them.
Regular network scanning helps your organization stay one step ahead of potential threats and promotes timely detection and risk mitigation. Remember, the ultimate objective is to shrink the attack surface to its minimum, creating a fortress so robust that it becomes virtually impenetrable for attackers.
Read our complete guide to the best network vulnerability scanning tools, carefully selected and reviewed for a variety of use cases.
Liz Laurente-Ticong is a tech specialist and multi-niche writer with a decade of experience covering software and technology topics and news. Her work has appeared in TechnologyAdvice.com as well as ghostwritten for a variety of international clients. When not writing, you can find Liz reading and watching historical and investigative documentaries. She is based in the Philippines.

Enterprise Networking Planet aims to educate and assist IT administrators in building strong network infrastructures for their enterprise companies. Enterprise Networking Planet contributors write about relevant and useful topics on the cutting edge of enterprise networking based on years of personal experience in the field.
Property of TechnologyAdvice. © 2025 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.