A patch management policy empowers organizations to maintain the security and integrity of their IT infrastructure by providing a structured approach to handling updates. It serves as a proactive defense mechanism against cyberthreats by ensuring that all systems have the latest security patches. The policy reduces the risk of breaches that can occur due to unpatched vulnerabilities, which are a common cause of security incidents.
Your company can avoid conflicts and streamline operations with a well-defined patch management policy. It outlines the timing and methods for applying patches, directly preventing disruptions from improper patching practices.
Furthermore, by having a robust patch management policy, organizations can demonstrate their commitment to maintaining secure systems, which can be significant during audits.
Featured Partners
Table of Contents
What is a patch management policy?
Patch management policies are a set of documented guidelines to ensure controlled, efficient, and secure patching. Organizations follow these guidelines when patching bugs and vulnerabilities to maintain the security, stability, and performance of computer systems and networks.
Components of patch management policies
The specific details of a patch management policy can vary depending on your organization’s size and complexity and the nature of your IT infrastructure. However, a typical patch management policy includes asset inventory, role assignments, patch testing and deployment, risk assessment and prioritization, scheduling, documentation, backup, policy approval, rollback plan, and periodic review and modification.
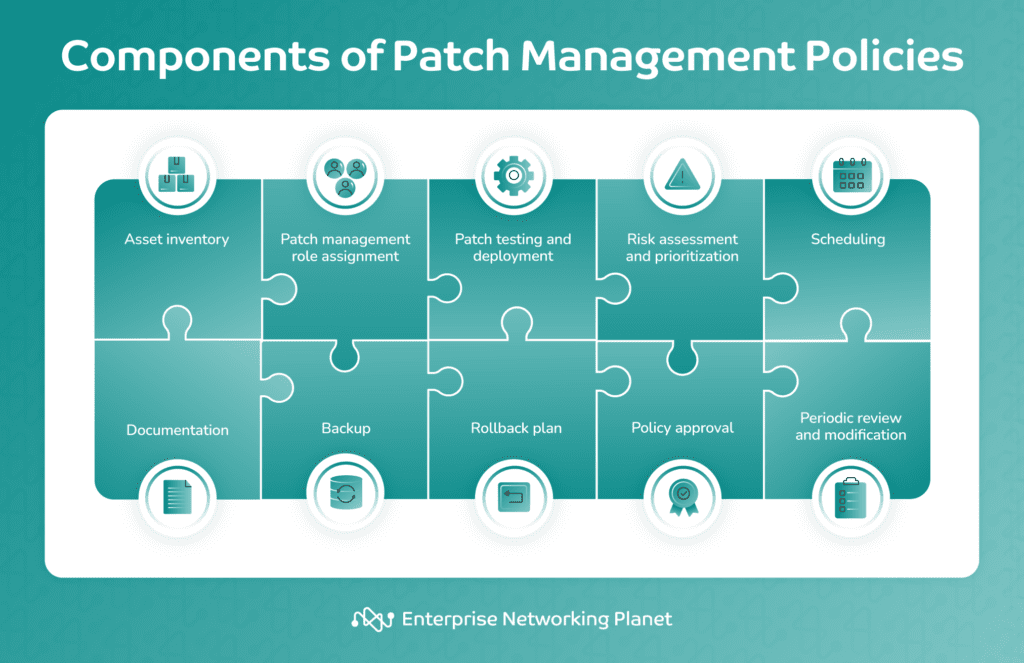
Asset inventory
This entails maintaining a detailed list of all hardware and software assets used in your organization. It serves as a comprehensive catalog of your IT resources, including servers, computers, and applications.
Role assignments
This involves designating specific roles to team members involved in the patch management process. It defines who is responsible for tasks like identifying patches, testing them, deploying them, and monitoring their effectiveness. Clear roles ensure accountability and a smooth patch management workflow.
Patch testing and deployment
The core of patch management, this element covers identifying software with vulnerabilities, evaluating the patches available to fix these vulnerabilities, testing these patches in a controlled environment, deploying them across the organization, and verifying their successful installation.
Risk assessment and prioritization
Responsible patch management requires evaluating the risks associated with vulnerabilities that patches aim to address. This allows IT teams to prioritize patching efforts, focusing on vulnerabilities with the highest criticality and potential damage. By prioritizing, your organizations can deal with the most severe security issues first.
Scheduling
You’ll want to carefully schedule your patch applications and maintenance windows outside of normal business operating hours to minimize disruption to employee productivity or customer service. Make sure you trigger notifications to warn your users in advance of any planned or expected downtime.
Documentation
Maintain detailed records of all patching activities, including dates, details of patches, and any issues encountered by you or your end users. This should include recording the installed patches, the installation time, the systems updated with these patches, and any problems that occurred during the process.
Backup
Backing up refers to regularly preserving important data and system configurations. This is crucial to ensure data integrity and give a fallback option in case patching leads to unexpected problems.
Backups prevent data loss and offer a quick recovery to a stable system state. They support rollback procedures, facilitate patch testing, and serve as part of disaster recovery planning, ultimately reducing the risks associated with patch deployment.
Rollback plan
This section outlines the process and procedures for reverting or undoing a software patch or update in case it causes unforeseen issues or system instability. The main purpose of a rollback plan is to guarantee system reliability and reduce downtime or negative impact on your organization’s IT infrastructure by preparing for the worst.
Policy approval
After developing the policy, stakeholders and executives should circulate it for approval to confirm that everyone understands its implications and is on board.
Periodic review and modification
Once it’s all been codified and confirmed, keep regularly reviewing and updating your patch management policy. Technology evolves, and so do security threats. Periodic review and modification ensure that the policy remains effective and adapts to changing needs and circumstances within your organization.
How to create a patch management policy
Creating a patch management policy commonly involves defining scope and objectives, identifying responsible parties, building an inventory and assessing vulnerability, setting criteria for prioritizing patches, testing and deployment, selecting a patch deployment schedule, and monitoring and generating reports.
1. Define the scope and objectives
Begin by defining the scope of your patch management policy clearly. Decide which systems and software you will cover, including operating systems, applications, and devices. Also, set the objectives of the policy. These objectives will aid in maintaining the security and reliability of your systems.
2. Identify responsible parties
Determine who will be responsible for various aspects of patch management, such as patch testing, deployment, and monitoring. This may involve IT administrators, security teams, and other relevant personnel.
3. Build an inventory and assess vulnerability
Create an inventory of all the hardware and software assets in your organization. Perform regular vulnerability assessments to uncover security weaknesses and prioritize which systems or applications require immediate attention. Tools like vulnerability scanners can assist in this process.
4. Set criteria for prioritizing patches
Establish a clear criteria and methodology for prioritizing patches. You should consider factors such as the severity of the vulnerability, the potential impact on your organization’s network security, and any regulatory or compliance requirements. Address serious vulnerabilities as a top priority.
5. Testing and deployment
Build a structured process to test patches before you deploy them in your production environment. Set up a staging or test environment to evaluate patches for compatibility and potential issues. Deploy patches to the live systems only after successful testing and use automated deployment tools to make the process more efficient.
6. Establish a patch deployment schedule
Establish a patch deployment schedule that aligns with your organization’s needs. This could include regular maintenance windows or maintenance cycles. Make sure to have procedures ready for managing emergency patches, particularly for vulnerabilities that require prompt resolution.
7. Monitor and generate reports
Implement continuous monitoring to keep an eye on missing patches, system health, and security events. Create a reporting mechanism for regular updates on the status of patch management to relevant stakeholders. Use information from these reports to adjust your patch management policy as needed.
Tips and best practices when creating a patch management policy
There are several things to keep in mind when creating a patch management policy, like understanding the impact of patch updates, establishing clear protocols, creating an inventory, conducting a risk assessment, enabling automatic updates, performing regular reviews, creating an enterprise strategy, and measuring the policy’s success.
Understand the impact of patch updates
It’s vital to comprehend how patch updates will affect the reliability of various products, services, and systems. This understanding can help in planning and executing the patching process in a way that decreases disruption and maximizes efficacy.
Establish clear protocols
Clear protocols provide a roadmap for security teams and IT admins to follow before approving a patch for deployment across all systems. These protocols should cover risk assessment, testing, validation, and change management, optimizing management of every aspect of the patch management process.
Create an inventory
Build an up-to-date inventory of all hardware and software assets within your organization. This includes servers, workstations, laptops, mobile devices, and applications. Outline procedures for identifying, categorizing, and prioritizing systems to prevent overlooking any resource during the patching process.
Conduct a risk assessment
By conducting a rigorous risk assessment, you can make informed decisions about which vulnerabilities to address first. You can evaluate the potential damage of vulnerabilities and the likelihood of exploitation and direct your management efforts toward the most critical areas of concern.
Enable automatic updates
The Cybersecurity and Infrastructure Security Agency (CISA) recommends enabling automatic updates whenever possible. This allows your organization to keep systems up-to-date without manual intervention. Fortunately, most leading patch management software solutions come with automatic patching features.
Perform regular reviews
Regularly reviewing your policy ensures that it still meets the evolving organizational needs, changes in technology, and emerging threats. This helps in maintaining the effectiveness of the policy over time.
Create an enterprise strategy
The National Institute of Standards and Technology (NIST) recommends creating an enterprise strategy that simplifies and operationalizes patching while also improving its risk reduction capabilities. It should encompass collaboration between leadership at all levels of an organization, along with business owners and security/technology management teams. Collaborating helps every individual grasp the role of patching and actively contribute to preserving the organization’s security.
Measure success of the policy
Finally, gauge the success of the policy with metrics to evaluate how well your patch management policy is working in your organization. Here are some of the metrics you can use:
- Key performance indicators (KPIs): Establishing KPIs for your patch management program is the best way to evaluate its success. These could include historical data on the average time it takes to apply a patch and historical data on unpatched vulnerabilities.
- Patch compliance rate: This metric gauges how well an organization adheres to its own patch management policies and requirements. It can help identify areas where you can refine the patching process.
- Time to patch: This important metric measures the average time it takes to apply a patch after its release. A shorter time to patch generally indicates a more efficient patch management process.
- Patch management solution coverage: This measures what proportion of the organization’s devices the current patch management solutions cover.
- Efficiency measures: These measures cover information on patch compliance, failed patches, and similar data.
8 benefits of patch management policies
Despite the upfront work involved, developing a comprehensive patch management policy can provide a bevy of benefits to your organization, ranging from better documentation and accountability to improved system performance — not to mention, of course, all of the security benefits.
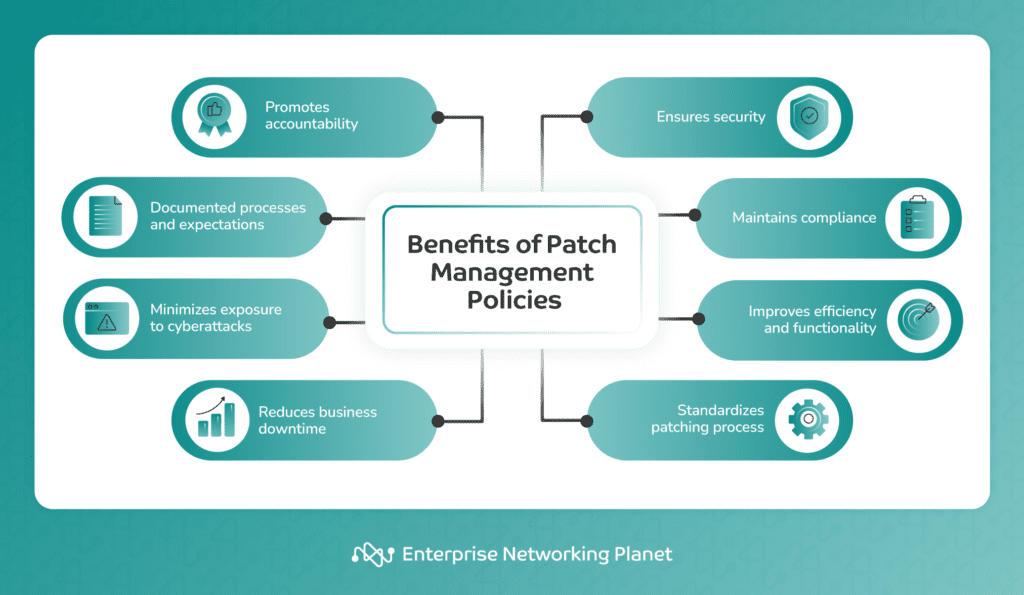
- Promotes accountability: A patch management policy clearly defines the roles and responsibilities of each team member relevant to the patching process. This promotes accountability and guarantees that everyone knows their role in maintaining the security of the organization.
- Documented processes and expectations: A well-documented patch management policy presents guidelines on how to handle patches. Both new and existing employees can easily understand their expectations, promoting consistency in the patching process.
- Minimizes exposure to cyberattacks: A good patch management policy reduces your organization’s vulnerability to cyberattacks. By updating all systems with the latest security patches, it decreases the chances of a breach.
- Reduces business downtime: A good patch management policy can also help in minimizing business downtime caused by improper patching practices. By outlining procedures for testing and deploying patches, it supports correct and efficient patch application, thereby reducing the likelihood of system downtime.
- Increases security: A well-established patch management policy can bolster the overall security of an organization by fixing security vulnerabilities promptly. By applying patches swiftly, the policy addresses known vulnerabilities in software that attackers might take advantage of. This reduces the risk of unauthorized access to business systems and data.
- Maintains compliance: Many industry regulations require businesses to have certain security measures in place, including regular systems patching. Therefore, having a comprehensive patch management policy can help an organization stay compliant with these regulations.
- Improves efficiency and functionality: Patch management policies can also contribute to better system performance and efficiency because patches often include enhancements to the actual functionality of a system.
- Standardizes patching process: A well-defined patch management policy standardizes the patching process across the organization. As a result, all technicians follow the same procedures when applying patches, leading to more consistent results and easier troubleshooting.
Bottom line: Boost security with an effective patch management policy
A well-structured patch management policy helps organizations address vulnerabilities, bolster security, and maintain operational stability. It can also aid in ensuring compliance with industry standards and regulatory requirements, instill confidence among stakeholders, and offer adaptability to changing security environments.
In creating your patch management policy, there are many things to consider, including understanding the results of patch updates, establishing clear protocols, activating automatic updates, creating an enterprise strategy, and measuring the policy’s success. Following best practices in crafting your patch management policy will boost its effectiveness.
To get started, you can create your own, or use our free patch management policy template. Also, be sure to review our list of the best patch management software.




