Network security solutions comprise software tools that protect computer networks from unauthorized access, cyber attacks, and data breaches. These solutions safeguard sensitive information, uphold data integrity, and maintain private communications within an organization.
The following are our picks for the best network security software:
- BitDefender GravityZone: Best price and best for web security (Read more)
- ESET Protect Platform: Best for network attack protection (Read more)
- TitanHQ: Best for email and DNS security (Read more)
- Malwarebytes: Best for malware detection and removal (Read more)
- Kaspersky: Best for endpoint protection (Read more)
- Avast Business: Best for growing businesses (Read more)
- Sophos: Best for ransomware defense (Read more)
- Trend Micro: Best for threat detection and vulnerability intelligence (Read more)
- SolarWinds: Best for managed service providers (MSPs) (Read more)
- Perimeter 81: Best for cloud-based networks (Read more)
Featured Partners: Cybersecurity Software
Table of Contents
Top network security software comparison
The table below shows an overview of what each network security software offers beyond firewall, web security, and malware protection. It presents data on network monitoring and visibility, built-in data loss prevention (DLP), resource consumption, and impact on speed:
| Network Security Software | Network monitoring and visibility | Built-in data loss prevention | Resource consumption | Impact on speed | Starting price |
|---|---|---|---|---|---|
| BitDefender GravityZone | Comprehensive | Yes | Resource-intensive | Low | $20.99/yr per device |
| ESET Protect Platform | Comprehensive | No | Low resource utilization | Moderate | Contact sales |
| TitanHQ | Good | Yes | Minimal resource utilization | Low | Contact sales |
| Malwarebytes | Comprehensive | No | Resource-intensive | Moderate | $69/yr per endpoint |
| Kaspersky | Comprehensive | Yes | Resource-intensive | Moderate | $202.50/yr for 5 users ($40.50/user) |
| Avast Business | Advanced | No | Resource-intensive | Moderate | $29.67/yr per device |
| Sophos | Comprehensive | Yes | Resource-intensive | Moderate | Contact sales |
| Trend Micro | Comprehensive | Yes | Resource-intensive | Moderate | See cost calculator |
| SolarWinds | Comprehensive | Yes | Resource-intensive | Moderate | Contact sales; perpetual license available |
| Perimeter 81 | Good | No | Minimal resource utilization | Moderate | $8/mo. per user ($96/yr) |

BitDefender GravityZone
Best price and best for web security
Overall rating: 4.25/5
- Cost: 4.5/5
- Core features: 4.5/5
- Performance and reliability: 3/5
- Integrations: 5/5
- Customer support: 3.5/5
- Ease of use: 3.25/5
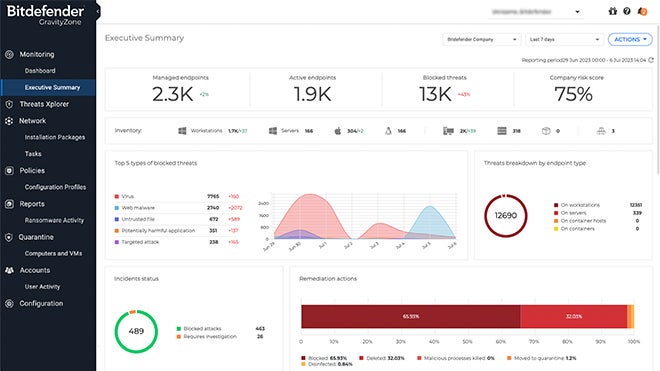
BitDefender’s GravityZone is a comprehensive cybersecurity platform you can deploy on-premises or have hosted by BitDefender. You can also opt for a combination of both. The platform offers risk assessment and mitigation to help businesses understand cybersecurity risks. It comes with Extended Detection and Response (XDR) to provide enhanced threat detection and visibility.
GravityZone responds to security incidents automatically and guides you for fast containment of attacks. Additionally, it includes advanced capabilities, such as hardening and risk analytics, anti-ransomware, application control, exploit defense, fileless attack defense, and machine learning (ML) technology to detect sophisticated threats.
Pros and cons
| Pros | Cons |
|---|---|
| Integrated risk analytics that constantly scansendpoints. | Limited support for macOS systems. |
| Anomaly detection and exploit defense block threats earlier in the attack chain. | Admin console is not user-friendly. |
| Identifies user behaviors that pose a security risk. | No built-in security information and event management (SIEM). |
Pricing
BitDefender has different pricing options for small businesses and medium to large enterprises, as well as MSPs:
Small businesses
- GravityZone Business Security Premium: $286.99 per year for 5 devices, including 2 servers and 8 mailboxes
- GravityZone Business Security: $129.49 per year for 5 devices, including 2 servers
- Small Business Security: $20.99 per year for 1 device, including 1 server
Medium and large businesses
- GravityZone Business Security Enterprise
- GravityZone Business Security Premium
- GravityZone à la carte
Contact their sales team to learn more.
Features
- Presents insight into cybersecurity risks associated with endpoint configuration and user actions.
- Leverages XDR to defend endpoints and for enhanced threat detection and visibility.
- Automatic and guided responses to security incidents for fast containment of attacks.
- Reduces the attack surface through hardening and risk analytics.
- Automatic backup of target files.
- Prevents malware and zero-day attacks
- Anti-exploit technology.
- Preventive ML technology specifically designed to detect complex threats and cybersecurity attacks on execution.
- Offers quick triaging alerts and supports incident investigation though its attack timeline and sandbox output.
- Human and endpoint risk analytics uncovers, prioritizes, and automatically enables hardening actions to remedy configuration risks.

ESET PROTECT Platform
Best for network attack protection
Overall rating: 4.25/5
- Cost: 2.5/5
- Core features: 4.25/5
- Performance and reliability: 4.25/5
- Integrations: 5/5
- Customer support: 4.5/5
- Ease of use: 5/5
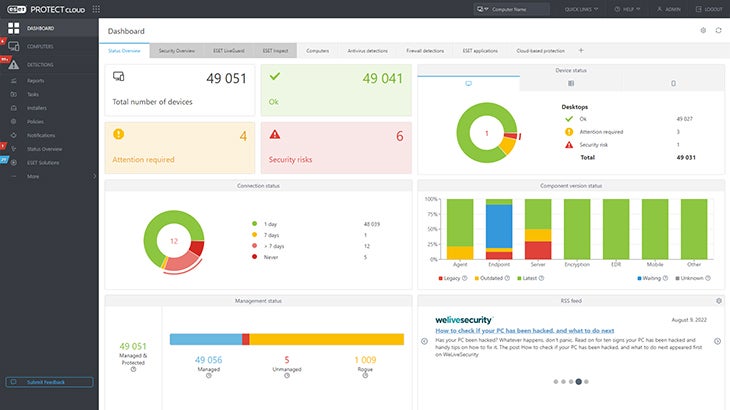
ESET PROTECT Platform delivers real-time visibility for on-premise and off-premise endpoints as well as full reporting. It brings a range of features, including ransomware prevention, zero-day threats detection, botnet protection, and automatic updates.
The platform also has access controls and permissions, activity monitoring and tracking, alerts and notifications, anomaly and malware detection, and anti-spam features.
ESET’s solutions are designed to be lightweight and have minimal impact on system performance, making them suitable for various IT environments. The ESET PROTECT Platform allows businesses to shield their networks and data, ensure business continuity, and comply with regulations.
Pros and cons
| Pros | Cons |
|---|---|
| Advanced role-based access control (RBAC) feature. | Lacks transparent pricing. |
| Botnet protection. | No SIEM. |
| Detects and neutralizes zero-day threats. | No built-in data loss prevention (DLP) feature. |
Pricing
ESET doesn’t display pricing for their solutions. Contact their sales team for pricing information.
Features
- Inspects incoming packets and blocks attempts to infiltrate the computer at the network level.
- Provides automatic updates at each endpoint.
- Advanced protection for data passing through all general servers, network file storage, and multi-purpose servers.
- Protects against infiltration by botnet malware, preventing spam and network attacks launched from the endpoint.
- Offers access controls and permissions.
- Activity dashboard that gives a quick overview of the network’s security status.
- Monitors network activity with a record of events.
- Zero-day threat detection.
- Alerts/notifications.
- Anomaly and malware detection.
- Anti-spam features.

TitanHQ
Best for DNS and email security
Overall rating: 3.5/5
- Cost: 1.75/5
- Core features: 2.5/5
- Performance and reliability: 5/5
- Integrations: 5/5
- Customer support: 3.25/5
- Ease of use: 5/5
TitanHQ provides a comprehensive suite of cybersecurity solutions focusing on network security, particularly for email and web protection. Its products SpamTitan, WebTitan, SafeTitan, EncryptTitan, and ArcTitan collectively deliver an integrated solution.
- SpamTitan is an advanced spam protection tool that blocks spam, viruses, malware, and ransomware. It uses ML and heuristics to defend against evolving threats.
- WebTitan is a DNS security and content filtering tool that delivers proactive protection from malicious web threats and attacks. It also maintains adherence to corporate web usage policies by blocking access to certain categories of websites.
- SafeTitan is a Security Awareness Training (SAT) tool that powers human layer protection by delivering contextual training in real-time.
- EncryptTitan is a full-featured encryption system suitable for both MSPs and enterprises that facilitates secure exchange of information via email.
- ArcTitan is a cloud-based email archiving tool that reduces the cost and complexity of archiving emails and satisfying discovery requests. It also enhances Office 365 email search and storage functionality.
Pros and cons
| Pros | Cons |
|---|---|
| Has advanced threat detection techniques like Bayesian auto learning and heuristics to defend against evolving threats. | Lacks transparent pricing. |
| Lightweight. | No dedicated vulnerability scanning and patch management features. |
| Uses AI-powered protection against active and emerging phishing URLs including zero-minute threats. | No built-in EDR or XDR. |
Pricing
TitanHQ doesn’t directly list product pricing on its website but states that its pricing model is based on a per-user approach. They also offer monthly pricing options to cater to specific needs and budgets.
Get in touch with their sales team for full pricing details.
Features
- Triple threat, multi-layered cybersecurity.
- Protecting against spam and web threats with cloud-based email archiving.
- Blocks spam, viruses, malware and ransomware.
- Email spam filtering.
- Advanced threat protection uses Bayesian auto learning and heuristics to defend against evolving threats.
- Security Awareness Training (SAT).
- Unlimited phishing simulations.
- DNS security and content filtering.
- Proactive protection from malicious web threats and attacks.
- Data loss prevention and regulatory and legal compliance.
- Enhances Office 365 email search and storage functionality.
- Full featured encryption system.
- Secure information exchange via email.

Malwarebytes
Best for malware detection and removal
Overall rating: 3.5/5
- Cost: 3/5
- Core features: 3.25/5
- Performance and reliability: 2.5/5
- Integrations: 5/5
- Customer support: 2.75/5
- Ease of use: 4.25/5
Malwarebytes offers a single agent with simple management. It includes endpoint detection and response (EDR) which uses unique anomaly detection ML to detect both known and unknown threats across Windows, Mac, and Linux platforms. In addition, it offers managed detection and response (MDR) services that hunt down hidden threats based on suspicious activity and past IOCs, reducing dwell time and potential impact of hidden threats.
Furthermore, Malwarebytes provides DNS filtering that blocks access to known suspicious web domains and has in-depth virus scanning that finds threats other software misses.
The solution’s network isolation restricts device interactions, preventing unauthorized access from potential attackers and malware from establishing outbound connections. Malwarebytes also offers centralized management, flexible push-install options, and asset management to deploy solutions, track, manage, and monitor endpoints.
Pros and cons
| Pros | Cons |
|---|---|
| Real-time protection. | Has conflicts with other antivirus software. |
| Simple and user-friendly interface. | No data breach protection. |
| Browser Guard feature blocks ads, scams, and trackers. | No built-in SIEM. |
| Uses unique anomaly detection machine learning to detect both known and unknown threats across different platforms. |
Pricing
Malwarebytes offers for per-device pricing plans:
- Core
- Advanced
- Elite
- Ultimate
Plans start $69 per endpoint per year with a minimum of 3 devices. Reach out to the Malwarebytes sales department to know more.
Features
- Integrated protection through a user-friendly single agent.
- EDR using unique anomaly detection ML.
- MDR services.
- DNS filtering with customizable rules and set up notifications.
- In-depth virus scanning.
- Virtual private network (VPN) for safe and private online browsing.
- Push-install options and asset management to safeguard endpoints.
- Blocks ads, scams, and trackers.
- Protects against clickbait and potentially unwanted programs (PUPs).

Kaspersky
Best for endpoint protection
Overall rating: 3.75/5
- Cost: 3.75/5
- Core features: 4.5/5
- Performance and reliability: 2.5/5
- Integrations: 3.25/5
- Customer support: 3.75/5
- Ease of use: 5/5
Kaspersky network security solutions reduce exposure to cyberattacks through endpoint hardening and boost productivity with cloud-enabled controls. Its Endpoint Security for Business stands out with its special features that defend against fileless threats.
The platform streamlines security management with a unified console. Moreover, its agile protection technologies and multi-layered protection approach based on ML technology and threat intelligence ensure effective security. Kaspersky also offers straightforward migration from third-party endpoint protection, making the transition seamless.
Pros and cons
| Pros | Cons |
|---|---|
| Quick deployment on any platform or infrastructure. | Slows down network performance. |
| Real-time threat intelligence from 80 million global sensors. | Resource intensive. |
| VPN with wide OS support and extensive server locations. | Limited pricing details. |
| Robust password policies. | No built-in SIEM. |
Pricing
Kaspersky has different pricing plans for SMBs and large enterprises.
SMB pricing starts at $202.50 (per year for 5 users).
Kaspersky doesn’t publish prices for enterprise plans — contact their sales department for more details.
Features
- Multi-layered, next-generation threat protection like application, web, and device controls.
- Vulnerability and patch management.
- Data encryption.
- Robust password policies.
- Real-time protection against online threats, monitors for suspicious files and programs, and detects and prevents attacks.
- Multi-level adaptive endpoint protection, automated threat defense, and systems hardening for mixed environments.
- Computer protection against network and phishing attacks.
- Unified console for simplified security management.
- Post-execution behavior detection and ML technologies.
- Straightforward migration from third-party endpoint protection.
- VPN and firewall.
- Web and device control.
- Asset management.
- System isolation.
- Malware detection.
- Incident reports.

Avast Business
Best for growing businesses
Overall rating: 3.75/5
- Cost: 3.75/5
- Core features: 3.75/5
- Performance and reliability: 2.5/5
- Integrations: 5/5
- Customer support: 3.25/5
- Ease of use: 3.25/5
Avast Business optimizes network security by delivering all its services from the cloud. This approach reduces costs, such as WAN expenses, and eliminates the need to deal with network appliances.
The solution performs full inline inspection of SSL and internet traffic to all ports and protocols, updating global threat feeds in real time. It also includes device and policy management, centralized alerts and notifications, real-time commands, network discovery, and remote deployment.
Avast provides anti-malware and antivirus protection to keep devices and data safe against cyberattacks. It shields businesses against viruses, ransomware, spyware, zero-second threats, and Wi-Fi network vulnerabilities.
Pros and cons
| Pros | Cons |
|---|---|
| Protects mail and web activity. | Time-consuming installation process. |
| Anti-spam feature. | Resource intensive. |
| Monitors threats network-wide across all connected endpoints. | Limited pricing details. |
| App behavior monitoring. | No built-in SIEM. |
Pricing
Avast offers three pricing plans for small businesses:
- Essential Business Security: $29.67 per device per year
- Premium Business Security: $37.40 per device per year
- Ultimate Business Security: $45.42 per device per year
These plans include up to 100 devices. For organizations with over 100 devices, contact the Avast Business sales team.
Features
- Full SSL inspection across all ports and protocols.
- Complete inline inspection of SSL and internet traffic.
- Updates global threat feeds in real time.
- Built-in device and policy management.
- Remote access and support tools.
- Anti-malware and antivirus.
- Protects against ransomware, spyware, zero-second threats, and Wi-Fi network vulnerabilities.
- Secure internet gateway.
- CyberCapture blocks unknown files and new threats.
- App behavior monitoring.
- Mail and web activity shields.
- Security browser extension.
- Anti-spam.
- Sandbox for running untrusted or unknown apps in a safe environment.

Sophos
Best for ransomware defense
Overall rating: 4/5
- Cost: 2.5/5
- Core features: 4.5/5
- Performance and reliability: 2.5/5
- Integrations: 5/5
- Customer support: 4.5/5
- Ease of use: 5/5
Sophos brings a range of network security tools to protect businesses from various cyberthreats. Its solutions include Sophos Firewall Security for network defense and Sophos Wireless for cloud-managed Wi-Fi. The platform also brings Zero Trust Network Access (ZTNA) for better segmentation, security, and visibility.
For businesses looking to automate their network security and management workflows, Sophos Central APIs are available. In addition, Sophos’ Extended Detection and Response (XDR) lets businesses identify and respond to threats across multiple security services.
Pros and cons
| Pros | Cons |
|---|---|
| Active adversary mitigations and ZTNA. | Doesn’t have SIEM. |
| Built-in anti-ransomware technology, deep learning, and exploit prevention. | Lacks pricing transparency. |
| Shared threat intelligence between endpoints and network. | Limited endpoint agent capabilities for macOS environments. |
Pricing
Sophos doesn’t publish pricing details for any of its solutions. Reach out to their sales team for complete pricing details.
Features
- Next-gen firewall.
- Cloud-managed Wi-Fi with high-performance scalability, synchronized security threat detection, and network access control.
- Cloud-managed network access layer switches to connect, power, and control device access at the LAN edge.
- Enhanced segmentation, security, and visibility over traditional remote-access VPN.
- Secure SD-WAN VPN connectivity with zero-touch deployment.
- Deep Packet Inspection (DPI).
- TLS 1.3 inspection.
- Zero-day and ML protection.
- Web protection.
- Two-factor authentication (2FA).

Trend Micro
Best for threat detection and vulnerability intelligence
Overall rating: 4/5
- Cost: 2.5/5
- Core features: 4.5/5
- Performance and reliability: 3/5
- Integrations: 5/5
- Customer support: 3.75/5
- Ease of use: 4.25/5
Trend Micro delivers solutions for effective protection for the entire IT environment, including users, devices, applications, and networks. These solutions come with a variety of features, like hardware for data-intensive data centers, virtual appliances for branch offices, and SaaS-based solutions that integrate seamlessly with AWS and Azure to streamline cloud operations. Additionally, they offer detection and response functionalities across multiple security layers.
What sets Trend Micro’s network security solutions apart is their adaptability. For instance, they offer secure access service edge (SASE) capabilities for real-time risk assessments of the connections between users, devices, and applications. This feature is particularly useful in minimizing risk and maintaining a secure network environment.
Pros and cons
| Pros | Cons |
|---|---|
| Provides ransomware rollback features. | Significant number of false positives during testing. |
| Native SASE capabilities. | Lacks transparent pricing. |
| Deep Discovery Inspector feature offers 360 degrees of visibility by monitoring all network ports and over 105 different protocols. | No SIEM. |
| Runtime protection for virtual, physical, cloud, and container workloads. |
Pricing
Trend Micro doesn’t give out pricing details on their website, though they do offer a handy (if highly complex) pricing calculator for estimates. For more information, you can get in touch with their sales team.
Features
- Protects against known, unknown, and undisclosed network vulnerabilities.
- Automatically enables threat intelligence.
- Runtime protection for virtual, physical, cloud, and container workloads.
- Zero Trust Secure Access.
- XDR.
- Uses bug bounty program Trend Micro (ZDI) to accelerate protection against threats.
- Customizable deployment options.
- VPN.
- Ransomware rollback.
- File encryption.
- Performs dark web scans.
- Endpoint security.
- Delivers 360 degrees of visibility.
- Built-in SASE capabilities

SolarWinds
Best for managed service providers (MSPs)
Overall rating: 3.5/5
- Cost: 1.75/5
- Core features: 3.5/5
- Performance and reliability: 2.25/5
- Integrations: 5/5
- Customer support: 4.75/5
- Ease of use: 3.25/5
SolarWinds has an extensive suite of network security tools to help businesses of all sizes protect their networks from threats. It excels in providing real-time visibility into network firewall security, monitoring firewall changes, and creating custom filters for specific firewall events. It also offers scheduled configuration backups and a configuration comparison tool, which are necessary for maintaining compliance and ensuring the availability of backups.
SolarWinds’ network performance monitoring and network configuration management capabilities help detect, diagnose, and resolve network performance issues. Additionally, its IP address management and switch port management features prevent IP conflicts and keep track of device connections, enhancing network security. SolarWinds is ideal for managed services providers (MSPs) wanting to provide scalable, reliable, and secure network management services.
Pros and cons
| Pros | Cons |
|---|---|
| Central IP address management. | Steep learning curve |
| Network configuration management that prevents network outages. | Upgrades are time-consuming. |
| Scheduled configuration backups. | Lacks transparent pricing. |
| Native SIEM feature. |
Pricing
SolarWinds offers subscription and perpetual licensing but doesn’t display pricing information. Contact their sales team to find out more.
Features
- Monitors firewall activity to quickly identify anomalous activities.
- Allows users to create custom filters that highlight specific firewall events.
- Supports scheduled configuration backups.
- Configuration Comparison Tool lets users identify changes between two different backups.
- Inventory and Auditing capabilities.
- Automates network configuration management, including firmware upgrades.
- Comprehensive network performance monitoring.
- Network configuration management prevents network outages and improves network performance.
- IP Address Manager (IPAM) enables centralized IP address management that can prevent IP conflicts.
- User Device Tracker (UDT) supports switch port management.
- VoIP and Network Quality Manager (VNQM) monitors the performance of VoIP calls and logs quality issues for security and reliability of VoIP communications.

Perimeter 81
Best for cloud-based networks
Overall rating: 3.25/5
- Cost: 1.25/5
- Core features: 2.75/5
- Performance and reliability: 4.25/5
- Integrations: 5/5
- Customer support: 3.25/5
- Ease of use: 4.25/5
Perimeter 81 offers cloud network security services that give unified access to remote servers, control access to infrastructure resources, and establish secure connections between the internet, private clouds, and public cloud providers. It combines network and application security capabilities within the cloud security model for complete coverage for both network and cloud applications.
This platform is built to meet the needs of businesses of all sizes, from small startups to large enterprises. One of its notable features is its ZTNA model, which makes sure that only authorized users can access network resources. Several advanced features complement this capability, including Firewall as a Service (FWaaS), Secure Web Gateway (SWG), and malware protection.
Pros and cons
| Pros | Cons |
|---|---|
| Uses cutting-edge FWaaS. | No free trial. |
| HIPAA-compliant VPN. | No SIEM. |
| Built-in SASE. | No vulnerability scanning and patch management. |
| Bank-level encryption. |
Pricing
Perimeter 81 offers multiple pricing plans:
- Essentials: $8 per user per month. Includes basic features.
- Premium: $12 per user per month. Includes advanced features.
- Premium Plus: $16 per user per month. Includes layered security for larger organizations.
- Enterprise: For businesses with over 50 employees. Pricing for this plan is available upon contacting the Perimeter 81 sales department.
Features
- ZTNA for creating adaptive least-privilege access policies based on device, identity, role, and location.
- Firewall as a Service (FWaaS).
- SWG controls web access and stops malware with a multi-layered approach for device and cloud protection.
- Maintains encrypted connections to private internal resources and unencrypted connections to the open internet simultaneously.
- Agentless Access to third-party contractors and other personnel who need limited application access with private connections for individual applications.
- Bank-level AES-256 encryption and individual user-to-app SSL connections.
- Ensures Zero Trust access across iOS and Android devices as well as PC, Linux, and Mac desktops.
- Web filtering.
- Multi-factor authentication (MFA).
- Automatic Wi-Fi protection.
- DNS filtering.
- Device posture check.
- Cloud management console.
- Monitoring dashboard.
Key features of network security software
There are several types of network security tools and technologies that form a comprehensive network security platform. These include firewalls, antivirus/anti-malware, network monitoring and visibility, identity and access management, encryption and data protection, web security, detection and response, vulnerability scanning and patch management, and SIEM. Having high performance and reliability is also an important feature of network security software.
Firewalls
Firewalls are a fundamental component of a network security software that control and track the flow of network traffic. They function as a barrier between trusted internal networks and untrusted external networks, and enforce predefined security rules to prevent unauthorized access and potential cyber threats.
Essentially, firewalls serve as the first line of defense, mitigating the risk of cyberattacks and securing the integrity of networked systems.
Antivirus and anti-malware
Antivirus and anti-malware guard against malicious software threats. They detect, quarantine, and remove various types of malware, including viruses, worms, Trojans, and spyware. By continuously scanning files, emails, and other data for known malware signatures and behavioral patterns, antivirus programs help stop the spread of infections and protect sensitive information.
Antivirus and anti-malware tools block harmful software that could compromise data confidentiality and disrupt network operations.
Network monitoring and visibility
Network monitoring and visibility features give real-time insights into network activities. Monitoring detects anomalies and potential threats early, allowing rapid responses. Visibility offers in-depth understanding of network behavior, aiding in incident response, performance optimization, policy enforcement, and compliance management.
Together, monitoring and visibility contribute to a proactive security posture by swiftly uncovering and addressing security incidents and optimizing overall network performance.
Identity and access management (IAM)
Identity and access management (IAM) tools control and manage user access to network resources. These tools guarantee that only authorized individuals have appropriate access privileges, reducing the risk of unauthorized access, data breaches, and insider threats.
By providing centralized control over user identities, authentication, and authorization, IAM tools boost security and streamline user management.
Encryption and data protection
Encryption and data protection play a pivotal role in the success of DLP within network security. Encryption safeguards the confidentiality and integrity of sensitive information, while DLP extends this defense by actively monitoring data, detecting policy violations, and preventing unauthorized access or data leaks.
Encryption, data protection, and DLP mechanisms create a strong defense against threats, ensuring a solid approach to safeguarding sensitive data.
Vulnerability scanning and patch management
Vulnerability scanning finds gaps in a network, allowing for proactive threat mitigation. Patch management, on the other hand, promotes prompt action against known vulnerabilities by applying patches and updates. These features help fortify the network against potential exploits, reduce the attack surface, and minimize the window of opportunity for cyber criminals to exploit vulnerabilities.
Security information and event management (SIEM)
By aggregating and analyzing data from various sources, SIEM elevates the overall security posture by detecting and responding to potential threats in real-time, improving the resilience of the network against cyberthreats.
SIEM solutions facilitate centralized monitoring, analysis, and correlation of security events across the network and allows organizations to meet compliance requirements.
High performance and reliability
High performance and reliability are also critical features in a network security solution due to their impact on overall system efficacy. Minimal resource utilization makes sure that the software operates smoothly without significantly slowing down network speed. Reliability enables continuous and consistent security operations, decreasing downtime and potential security gaps.
How we evaluated network security software
To find the best network security software and tools for the year 2023, we systematically assessed different vendors. Our approach involved evaluating six key aspects of every software solution: cost, core features, performance and reliability, customer support, integrations, and ease of use.
We delved into the effectiveness of each software in meeting the standards set by these categories. We then assigned scores based on our evaluation and calculated the scores for each solution.
Cost – 20%
To evaluate the costs, we considered the pricing transparency and availability of free trials and their duration. We also checked if the provider offers multiple pricing models/options and gives businesses the opportunity to choose a plan that will suit their needs.
Criterion winner: BitDefender GravityZone
Core features – 25%
For the core features, we verified if the network security software has the following features as built in capabilities: firewall, intrusion detection and prevention, vulnerability scanning and patch management, identity and access management, network monitoring and visibility, antivirus and malware protection, encryption and data protection, web security, detection and response, and SIEM.
Criterion winners: Bitdefender GravityZone, Kaspersky, Sophos, and Trend Micro
Performance and reliability – 10%
To measure each vendor’s performance and reliability, we researched their resource consumption, scalability, and impact on network speed.
Criterion winners: ESET PROTECT Platform, Perimeter 81, and TitanHQ
Customer support – 20%
We determined if each provider offers the following support options to their customers: live chat, phone, email, community, documentation.
We also factored in the availability of these options to all users regardless of payment tiers, their hours of availability, and the response times according to actual users.
Criterion winner: SolarWinds
Integrations – 15%
For integrations, we examined the number of third-party solutions the solutions directly integrate with. We also considered the support for custom integrations.
Criterion winners: BitDefender GravityZone, Malwarebytes, Avast Business, Sophos, Trend Micro, ESET PROTECT Platform, SolarWinds, and Perimeter81
Ease of use – 10%
We looked into various user feedback to gauge the user-friendliness of the network security tools. We assessed whether each software was easy to install and manage for users of different levels of technical expertise.
Criterion winners: Kaspersky, Sophos, and ESET PROTECT Platform
Frequently Asked Questions (FAQs)
Can a network be completely secure?
No network can be considered completely secure because cybersecurity is dynamic and constantly evolving, with new threats and vulnerabilities emerging all the time. However, you can implement robust security measures to significantly reduce the risk of breaches.
What tool is the best for defending a network?
Ultimately the best tool for defending your network is going to depend on the variety of factors that add up to your own unique use case. Networks are complex and multifaceted, and network security no less so.
That being said, based on our rigorous research, the security solutions best for the widest range of network defense use cases are tied between BitDefender GravityZone and ESET PROTECT Platform. Both tools provide a broad set of native features to protect nearly every aspect of your network and systems.
Are there free network security solutions?
Yes, there are many free network tools and services available today, including the following:
| Free network security software | Description |
|---|---|
| FortifyData | Vulnerability assessment |
| OpenVAS | Vulnerability scanner |
| ShadowServer | Network reporting |
| Zscaler | Ransomware risk assessment |
| Cloudflare Unmetered DDoS Protection | Distributed Denial of Service (DDoS) protection |
For a more comprehensive list of free cybersecurity tools and services, check out recommendations from the Cybersecurity and Infrastructure Security Agency (CISA) page.
Bottom line: Choosing the best network security solution for your business
Choosing the right network security software can have a huge effect on the efficiency of your business operations. It’s not just about selecting the most advanced solution, but the one that best fits your specific needs and context.
Consider factors such as the size of your network, the nature of your data, and of course, your budget. Don’t hesitate to sign up for free trials to experience firsthand what the software can do for your organization. Look for solutions that offer a good balance between sophisticated features and usability.
The goal of network security is not to achieve complete security — which is impossible — but to manage and minimize risk to an acceptable level. It’s a continuous process that involves monitoring, improvement, and adaptation to new threats.
There is a broad selection of tools you can use to further strengthen your network security. Explore our article on types of network security solutions to implement to learn more.








